Users should have proper access to the data they need, neither more nor less.
MySQL Administrator provides a graphical interface that can be used to manage users and account permissions.
MySQL creates a user account named root, which has complete control over the entire MySQL server. In daily work, root should never be used, and a series of accounts should be created for different users to use to prevent malicious or unintentional damage to the database.
MySQL user accounts and information are stored in a database named mysql, to get a list of all user accounts:
USE mysql;
SELECT user FROM user;
The user table contains all user accounts. The user column in the table stores user login names. The new server may only have one root user.
It is best to open multiple database clients when changing the authority, one to change the authority, and one to test the changed authority.
Create a new user:
CREATE USER ben IDENTIFIED BY 'password';
The new user ben is created above, and the password is password.
The password specified by IDENTIFIED BY is in plain text, and MySQL encrypts it before storing it in the user table. To use the encrypted hash value as the password, use IDENTIFIED BY PASSWORD.
GRANT statement can also create users, but CREATE USER is simpler and clearer. You can also directly insert rows into the user table to add users, but for safety, don’t do this. The tables and table schemas where MySQL stores user account information are extremely important. Damage to them will damage the MySQL server, so it’s best to use commands and functions. Process these tables.
Rename a user:
RENAME USER oldName TO newName;
The RENAME USER statement was only supported after MySQL 5. Before that, in order to rename a user, you need to use the UPDATE statement to directly update the user table.
Delete user account and related permissions:
DROP USER userName;
DROP USER is only supported after MySQL 5. Before that, DROP USER can only be used to delete user accounts, and cannot delete related permissions. Therefore, the old version needs to REVOKE the permission to delete this account first, and then delete the user.
After creating a user, you must assign access permissions, otherwise the new user can only log in to MySQL, cannot see the data, and cannot perform any database operations. View user permissions:
SHOW GRANTS FOR userName;
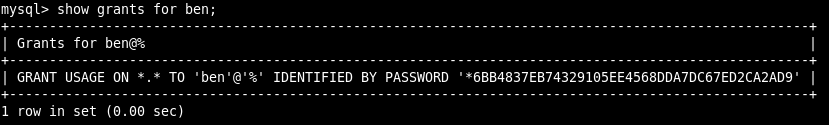
The output shows that the user ben has permission USAGE ON *.*, and USAGE means no permission. This result indicates that there is no permission for anything on any database or any table.
MySQL permissions are defined by a combination of user name and host name. If the host name is not specified, the default value %means that the user is granted access rights regardless of the host name.
Granted permission:
GRANT SELECT ON crashcourse.* TO ben;
The above example grants ben the SELECT permission on all tables in the database crashcourse.
Revoke permissions:
REVOKE SELECT ON crashcourse.* FROM ben;
The revoked authority must exist, otherwise an error will be reported.
Grant and revoke permissions:


When using GRANT and REVOKE, the user account must exist, but the involved database or table and other objects do not need to exist. This allows the administrator to design and implement security measures before creating the database and table. The side effect is that when a library or table is deleted, the related access permissions still exist. If the library or table with the same name is rebuilt, the permissions still work.
Simplify multiple authorizations:
GRANT SELECT, INSERT ON crashcourse.* TO bforta;
Change user password:
SET PASSWORD FOR bforta = Password('密码');
The new password must be encrypted using the Password function.
Change your own password:
SET PASSWORD = Password('密码');