JSON injection and CSRF vulnerability principle and recurrence
1. JSON (JavaScript Object Notation) JavaScript object notation
2. It is a data format, not a programming language
3. The syntax of JSON:
There are three types of values: simple values, objects, and arrays;
About the writing of JSON:
Represents the object (written using the object literal of JS):
{
“name”:”John”,
“age”:40
}
(The attribute name must use double quotation marks, without a semicolon at the end, allowing embedded writing, that is, the value is allowed to be an object)
{
“name”:{
“age”:10,
“sex”:’w’},
“address”:”wuhan”
}
Represents an array:
[25,"john","man" ]—(Objects can also be nested in an array)
4. JSON global variable object provided by JS
Contains two methods: stringify() and parse(), which respectively represent converting objects into JSON and converting JSON into objects;
Usage: JSON.stringify (object) and JSON.parse (string);
About stringify() filtering serialization:
In the second parameter, pass in the array of attribute names you want to serialize, and only the corresponding attribute names will be serialized;
For example: the person object has three attributes: name, age, and sex
Use JSON.stringify(person,["name"]);—Indicates that the string returned after serialization has only the name attribute, that is, {"name":"..."};
You can also pass in a function: function (key, value), if it returns undefined, it means that the item will not be serialized;
The third parameter represents indentation, pass in a number or string to indent, because the object string after stringify serialization will not branch
toJSON() method: returns its own JSON data format;
The second parameter of the parse() method can also be passed into a function, which is also a key-value;
Use PHP to format into JSON:
Two functions:
json_encode (object): convert the object into json format data;
json_decode(string): replace the JSON string with an object;
(json_decode() can specify true as the second parameter, then an array is returned)
JSON injection: (usually combined with SQL injection, SQL injection vulnerabilities caused by JSON injection statements)
Use json_decode to parse the incoming json format string to the corresponding array or object, and then call the information stored in JSON to perform the corresponding SQL query;
(The above code, what needs to be constructed is $username)
When constructing the corresponding pseudo code, you need to pay attention to the escape of special characters;
E.g:
Try: 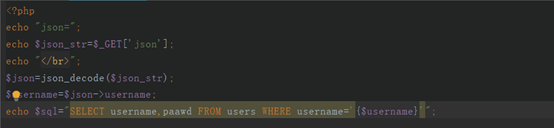
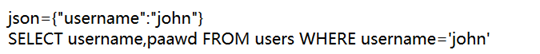
continue to construct json:
 (Finally, you can inject SQL statements... It should be noted that in the constructed statement, the double quotes in the middle must use escape characters) ------ -In the JSON syntax, use double-quoted
(Finally, you can inject SQL statements... It should be noted that in the constructed statement, the double quotes in the middle must use escape characters) ------ -In the JSON syntax, use double-quoted
CSRF: (Cross-site request forgery)
Principle: Use the logged-in state of the user to induce the user to visit a malicious website, thereby realizing the theft of cookies and forging the user's identity to send a request to the target site;
( The constructed malicious website will have a URL that sends a request to the target server. Since the user visits the malicious website, the user will send the cookie to the target server, resulting in a malicious request)
Two common methods:
1. Vulnerabilities in GET requests
Take the CSRF of the pikachu platform as an example:
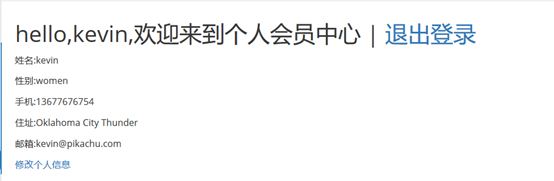
(Log in with kevin, click to modify personal information)
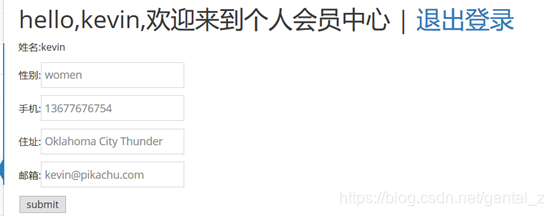
Click submit here directly to capture the packet to view the sent get request header:

(You can find that the sex value corresponds to women, etc., which just match the above information that needs to be modified, construct a malicious link, and change the sex value to man)
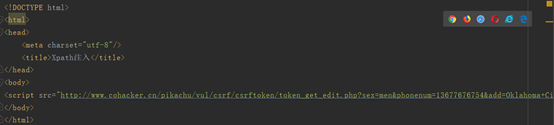
(Visit this page in the same browser, and then check its own properties)

You will find that the sex attribute has changed to men, which leads to a CSRF vulnerability.
2. The general principle of using POST requests
(this vulnerability needs to guide the user to click the submit form)
is similar to the above; for 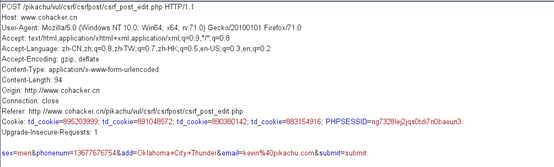
packet capture analysis, the requested fields are all post requests, which is required here Construct form submission and induce users to click on the form; (click hijacking vulnerability can be used) 
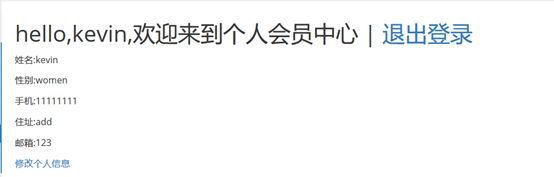
(it seems that you can directly use JS to hide the form directly without temptation)
A special example of CSRF cross-site request forgery: JSON hijacking
Defense method:
specify only from Redirect visit to designated website;