Article Directory
Write in front
This article is a targeted quick review based on the key points given by the teacher.
For the younger students of Henan University, if your teacher is Teacher Yuan, he will review the main points, and follow the review points with a targeted review.
True or False 2*5
- The question type is too mixed and unpredictable. You may test the yellow or black part of the PPT
Short answer question 5*6
range
- Know the reasons why information security majors study cryptography
- Master the basic ideas of stream ciphers
- Understand the CBC working mode of block cipher, and be able to draw a schematic diagram of the mode of encryption
- Understand the definition of weak one-way function and strong one-way function
- Be able to know 5 new directions or new technologies of cryptography (just write 5)
- The sixth may be yellow or black
exercise
1.Know the reasons why information security majors study cryptography (Non-standard answer) (Required!)
Answer: The status and role of information in society are becoming more and more important, and its security is becoming more and more important. Cryptography is the core technology to ensure information security. Cryptography has penetrated into all aspects of our daily lives. For example, public key cryptography is used for digital signatures and authentication services. Without it, common online payment systems cannot exist. There are also some important user login systems, and the encryption of information in mobile communication also relies on cryptography. Studying cryptography for information security majors helps students understand how to ensure information security and establish basic ideas.
2.The basic idea of stream cipher: (Required!)
3.CBC working mode is: It encrypts a plaintext block (8 bytes in a group) at a time, and each encryption uses the same key. The input of the encryption algorithm is the exclusive OR of the current plaintext block and the previous ciphertext block, so the input of the encryption algorithm will not Shows the fixed relationship between the plaintext groups this time, so repeated plaintext groups will not expose this repetitive relationship in the ciphertext (Must remember!)
CBC mode encryption and decryption diagram (Required!)
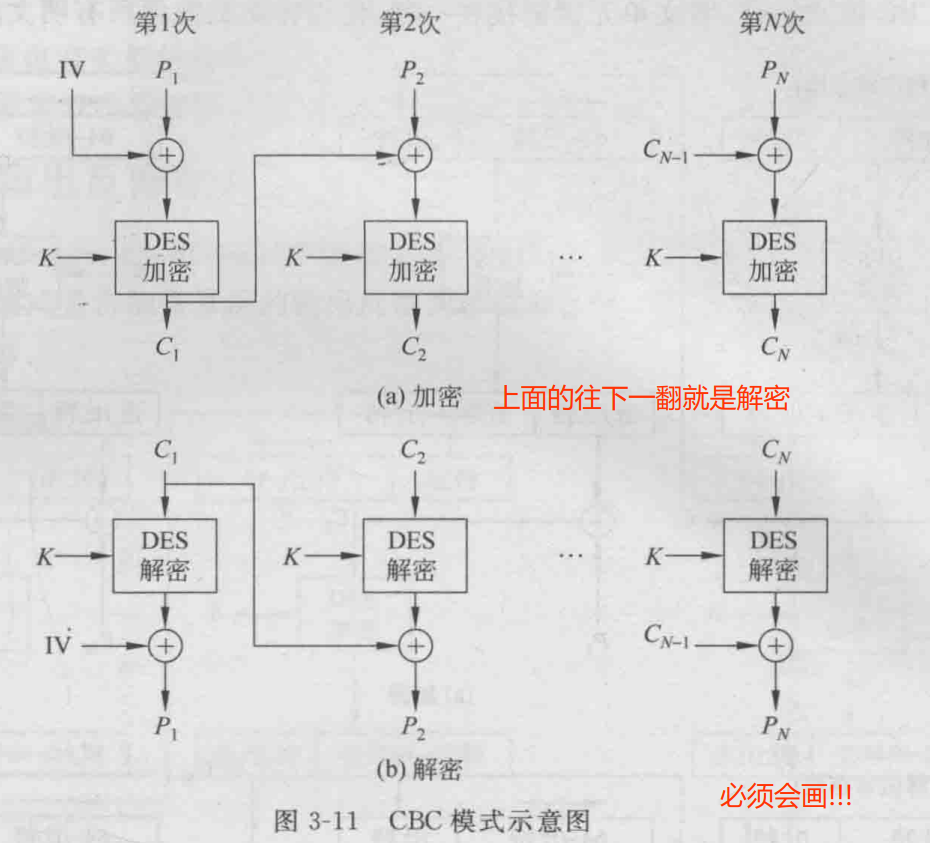
Encryption: C i = E k [P i ⊕C i-1 ] (can be regarded as C 0 =IV) Decryption: P i = D K [C i ]⊕C i-1
The initial vector of IV is XORed with the first plaintext block and should be protected like a key. This mode can obtain confidentiality and authentication, suitable for encrypting 64-bit messages
4.Weak one-way functions and strong one-way functions (Required!)
One-way function: Given h, it is computationally infeasible to find x such that H(x)=h.
Given x, find y (y≠x) such that H(y)=H(x) is computationally infeasible. If the one-way function satisfies this property, it is called a weak one-way function (Must be able to recite!)
It is computationally infeasible to find any two different inputs x and y such that H(x)=H(y). If the one-way function satisfies this property, it is called a strong one-way function (Must be able to recite!)
It is known that finding one and the other to make the H function equal is weak one-way, and arbitrarily giving two to make the H function equal is strong one-way (see who is very single)
5. Write 5 new directions or new technologies in cryptography
Identity-based encryption (IBE), attribute-based encryption (ABE), fully homomorphic encryption, dynamic encryption, searchable encryption
Calculation problem 10*4
range
- According to a given byte a, a given AES affine transformation (*) and irreducible polynomial m(x), the result of byte a in the AES S box can be obtained (you need to invert yourself) , Try it out by yourself)
- Able to perform encryption and decryption calculations based on the RSA algorithm
- a*b (mod q) = a (mod q) * b (mod q)
- φ (n) = φ§ * φ (q) = (p-1) * (q-1)
- Able to use ElGamal digital signature system to perform signature and verification calculations
- a*b (mod q) = a (mod q) * b (mod q)
- Able to calculate and generate the shared key of both parties based on the DH key exchange protocol
exercise
1.For byte a=1011 0110 byte substitution transformation, let the inverse of a be a -1 ( Required!)
Answer: First find the inverse of a, then use affine transformation
1️⃣ From a (x 7 + x 5 + x 4 + x 2 + x) a -1 ≡ 1(mod x 8 + x 4 + x 3 + x+1)
So a -1 = x 6 + x 5 + x 4 + x 3 is 0111 1000 (the binary corresponding digit has 1 means that there is the first power of x)
According to the test points given by the teacher, the affine transformation and m(x) questions will be given, and the inverse of a will come out.
a * a -1 Immediately 1011 0110 * 0111 1000 = 1101 0110 0100 00
a*a-1 mod m(x):1101 0110 0100 00 % 1000 1101 1(m(x)) = 1
During the exam, try 1 binary, 2 binary, 3 binary, and multiply %m(x) with a to see if it is 1
2️⃣ Use affine transformation (note that the inverse of a is used and the order of x is read from bottom to top)
Note that it is modulo 2 plus, that is, only 0 and 1
That is (0100 1110) 2 = (4E) 16 Note that it is also read from the bottom because the bottom is the high byte of the byte, which is the first 01...
2.1 In the RSA encryption system, the public key of the receiver is (e,n)=(5,35), the received ciphertext is C=10, find the plaintext M (Required!)
Answer: (m ≡ c d mod n so you have to calculate d -----> d*e ≡ 1 mod φ(n))
n=35 so p=5, q=7
φ(35) = (p-1)*(q-1) =4*6=24
Because d*e ≡ 1 mod φ(n), d=5 (this time, try one by one)
m ≡ c d mod n ≡ 10 5 mod 35 ≡ 5 (note that it is not an equal sign)
The test can find the plaintext and then reverse the ciphertext test to see if the ciphertext is 10
2.2 Assuming the plaintext m=5, e=7, p=11, q=13, the encryption and decryption process of RSA is given (Required!)
Answer: n=p*q=11*13=143 φ(143) = (p-1)*(q-1) = 10*12=120
Since d*e ≡ 1 mod φ(n) is d*7 ≡ 1 mod 120, d=103
Encryption: c ≡ m e mod n ≡ 5 7 ≡ 47 mod 143
Decryption: m ≡ c d mod n ≡ 47 103 ≡ 5 mod 143
3. In the ElGamal signature system, suppose p=19 and g=13. The private key of signer A is x = 10, try to calculate the public key. Set message M=15, k=11, seek the signature process and verify. (Required!)
Answer: Public key: y ≡ g x mod p ≡ 13 10 mod 19 = 6
Signature: r ≡ g k (mod p) ≡ 13 11 mod 19 = 2
s ≡ (H(m)-xr)k-1 (mod p-1) ≡ (m-xr)k-1 (mod p-1) ≡ (15-10*2)*11-1 mod 18 = 11
So (r,s)=(2,11)
Verification: y r r s ≡ 6 2 *2 11 mod 19 ≡ 8 ≡ g m (mod p) ≡ 13 15 ≡ 8 mod 19
According to the teacher’s key point, a*b (mod q) = a (mod q) * b (mod q) should be used in this question, for example, seeking 6 2 *2 11 mod 19 is equivalent to seeking 6 2 mod 19 * 2 11 mod 19 ≡ 17 *15 ≡ 8 mod 19
Find the above 11 -1 mod 18:
11*x ≡ 1 mod 18 can be calculated as x=5, and 11*11 -1 ≡ 1 mod 18 is 11 -1 ≡ 5 mod 18
4. In the Diffie-Hellman key exchange process, suppose that the large prime number p=11, a=2 is the primitive root of p. (Required!)
(1) User A's public key Y A =9, find its secret key XA.
(2) Set user B's public key Y B =3, find the shared key K of A and B.
Answer: 1️⃣ Y A =a XA mod p = a XA mod p ie 9=2 XA mod 11 so X A =6 (try one by one during the exam)
2️⃣ K = Y B XA mod p = 3 6 mod 11 = 3
Essay questions 1*20 (you can choose one)
- Introduce the research and application of a cryptographic protocol.
- Propose a security application scenario, and try to design a corresponding cryptographic protocol to implement security applications.
- Introduce a security application scenario, analyze which cryptographic technologies are used in the security scenario, and briefly describe how to ensure security.
https://baike.baidu.com/item/%E9%9B%B6%E7%9F%A5%E8%AF%86%E8%AF%81%E6%98%8E
Zero-knowledge proof
Introduction
The zero-knowledge proof was proposed in the early 1980s. It means that the prover can convince the verifier that a certain assertion is correct without providing any useful information to the verifier. Zero-knowledge proof is essentially an agreement involving two or more parties, that is, a series of steps that two or more parties need to take to complete a task. The prover proves to the verifier and makes it believe that he knows or possesses a certain message, but the certification process cannot disclose any information about the certified message to the verifier.
If there are too many paragraphs can be omitted
The zero-knowledge proof originated from the minimum leakage proof. Let P denote an entity that has certain information and hopes to verify this fact, and let V be an entity that proves this fact. If a certain protocol proves to V that P does have certain information, but V cannot infer what the information is, we say that P achieves the minimum leakage proof. Not only that, if V can not get any knowledge except knowing that P can prove a certain fact, we say that P realizes zero-knowledge proof, and the corresponding protocol is called zero-knowledge protocol.
For example, if A wants to prove to B that he has the key to a certain room, suppose that the room can only be opened with the key and cannot be opened by any other method. There are 2 methods at this time:
①A shows the key to B, and B uses the key to open the lock of the room to prove that A has the correct key to the room.
② B confirms that there is an object in the room, and A uses the key that he owns to open the door of the room, and then takes out the object and shows it to B to prove that he does have the key to the room.
The latter method ② is a zero-knowledge proof. Its advantage is that, in the entire certification process, B can never see the appearance of the key, thus avoiding the leakage of the key.
Application dynamics
Zero-knowledge proofs are widely used in blockchains. The first blockchain to use zero-knowledge proof technology is called Zcash, which is one of many zero-knowledge proof methods and the most famous one. God V once stated that zero-knowledge proof can be applied to almost all scenarios on the Ethereum blockchain.
Compared with ZCash, Bitcoin transfers are not completely anonymous. As long as they know a Bitcoin address, anyone can check all the "consumption" behaviors of this address through this website. For example, to whom the transfer was made and from whom the transfer was received are recorded in detail on the "ledger" based on blockchain technology.
For example, if A has 3 BTC and wants to transfer 1 BTC to B, then it will be recorded on the ledger: A transferred two BTCs, one is 1BTC and transferred to B; the other is 2BTC, transferred to Lost myself.
So how does ZCash, which uses "zero-knowledge proof", achieve the so-called anonymity?
The token of ZCash is ZEC. Also suppose that A has 3 ZECs, and 1 ZEC needs to be transferred to B.
First, A will divide one of its own ZEC into several parts and randomly put it into a series of "mixed containers", specify the address of the recipient B, and when mixed in, there will be several ZEC output by other parties. These ZECs are randomly split by the mixing container, and then from all the ZECs generated by the splitting, a total of 1 ZEC is taken out and transferred to the address of B. At the same time, a certain delay can be set in the sending time.
The "hybrid container" is a "public chain". After a series of "currency mixing" processes on this public chain, transaction information including transaction addresses and specific amounts becomes impossible to verify.
Although the zero-knowledge proof technology will bring stronger anonymity to the blockchain, it will also cause a lot of regulatory problems. This is a problem that the zero-knowledge proof technology cannot avoid.