Next, we will actually demonstrate how Terraform deploys resources. Taking Azure as an example, we first need to prepare Azure CLI. CLI can be used for authentication. Terraform itself has no authentication function. How to determine whether we have permission to proceed The deployment/change of resources mainly depends on the cloud platform itself, so we need to verify our identity first, and then we can deploy and change cloud resources.
Azure CLI can use the service principle to log in, we can first create an SP
$sp = New-AzADServicePrincipal -Scope /subscriptions/6dxxxxxxxxxxxxxxxxxx
You can see the newly created sp in the application registration
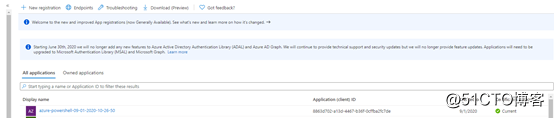
Then you can authorize the sp. You can first give the sp a resource group contributor permission or subscription permission
Then you can log in in Azure CLI. First, specify the login environment as China
az cloud set --name AzureChinaCloud
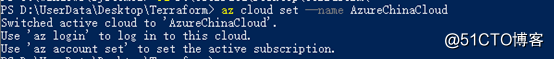
the login
Pop up the browser login window, enter the password to log in
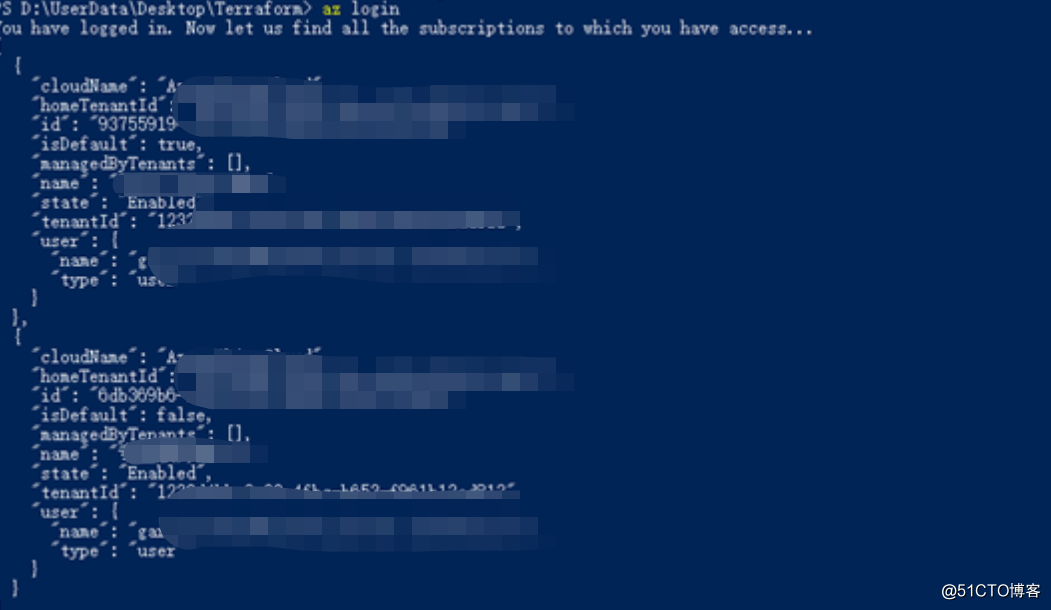
The cloud environment has been prepared, and then you can write Terraform code. If you simply create a virtual machine, the terraform code will be very simple. As for the parameters that need to be specified when creating a virtual machine, such as the name of the virtual machine, size, etc. We can all be defined as variables, which is very similar to other programming languages
Terraform version 0.13 or higher needs to define the provider in the following way. The required provider must first define the provider version if it is used. It can be a fixed version or a range can be specified.
terraform {
required_providers {
azure = {
source = "hashicorp/azurerm"
version = "2.14.0"
}
}
}
Next is the definition of resources
The definitions in locals are generally reusable constants, which do not need to be assigned like variables during deployment, but can be used directly
locals {
vm_name = "AzureVM"
}
The beginning below is the definition of Azure resources, including resource groups, virtual networks, network cards, etc.
resource "azurerm_resource_group" "main" {
name = "${var.prefix}-resources"
location = var.location
}
resource "azurerm_virtual_network" "main" {
name = "${var.prefix}-network"
address_space = ["10.0.0.0/16"]
location = azurerm_resource_group.main.location
resource_group_name = azurerm_resource_group.main.name
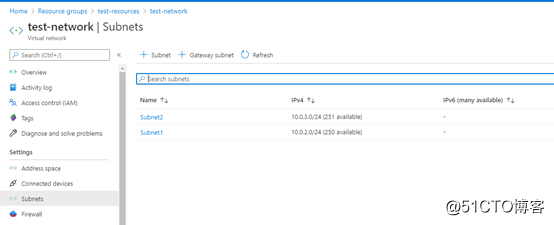
subnet{
name = "Subnet1"
address_prefix = "10.0.2.0/24"
security_group = azurerm_network_security_group.example.id
}
subnet{
name = "Subnet2"
address_prefix = "10.0.3.0/24"
security_group = azurerm_network_security_group.example.id
}
}
resource "azurerm_network_interface" "main" {
name = "${var.prefix}-nic"
resource_group_name = azurerm_resource_group.main.name
location = azurerm_resource_group.main.location
ip_configuration {
name = "internal"
subnet_id = element(azurerm_virtual_network.main.subnet.*.id, 1)
private_ip_address_allocation = "Dynamic"
public_ip_address_id = azurerm_public_ip.example.id
}
}
resource "azurerm_virtual_machine" "main" {
name = "${var.prefix}-vm"
resource_group_name = azurerm_resource_group.main.name
location = azurerm_resource_group.main.location
vm_size = "Standard_DS2_v2"
network_interface_ids = [
azurerm_network_interface.main.id
]
storage_image_reference {
publisher = "MicrosoftWindowsServer"
offer = "WindowsServer"
sku = "2016-Datacenter"
version = "latest"
}
storage_os_disk {
name = "myosdisk1"
caching = "ReadWrite"
create_option = "FromImage"
managed_disk_type = "Standard_LRS"
}
storage_data_disk{
name = "DataDisk"
caching = "None"
create_option = "Empty"
disk_size_gb = 500
lun = 0
managed_disk_type = "Premium_LRS"
}
os_profile {
computer_name = local.vm_name
admin_username = var.username
admin_password = var.password
}
os_profile_windows_config {
enable_automatic_upgrades = false
provision_vm_agent = false
}
}
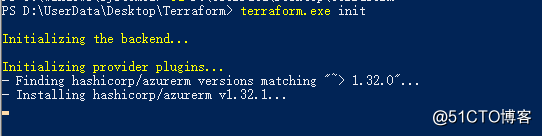
Define the IAC code, first we use terraform init to download the required provider, you can see that the Terraform azurerm provider is being downloaded
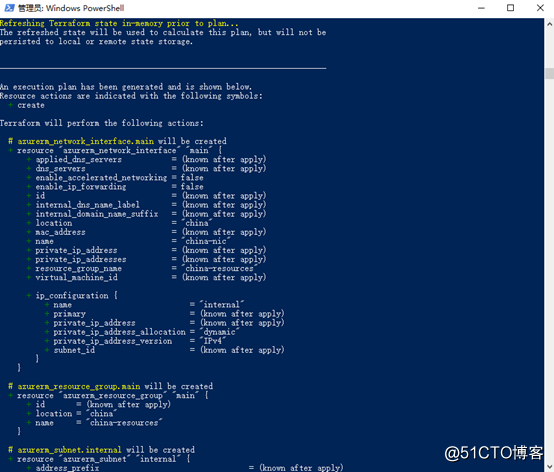
After the download is complete, try to perform a plan to see the changes that will occur during deployment. You can see that there are many + in the front, which means that these resources will be added. If it is destroyed, you may see many-signs. In addition, In fact, terraform makes resource changes mainly based on the state in tfstate. Since we are an empty state, any resource created will be judged as a new addition. If it is an existing state, we must first look at the state. What's in it
Next, apply directly to create, enter yes to confirm
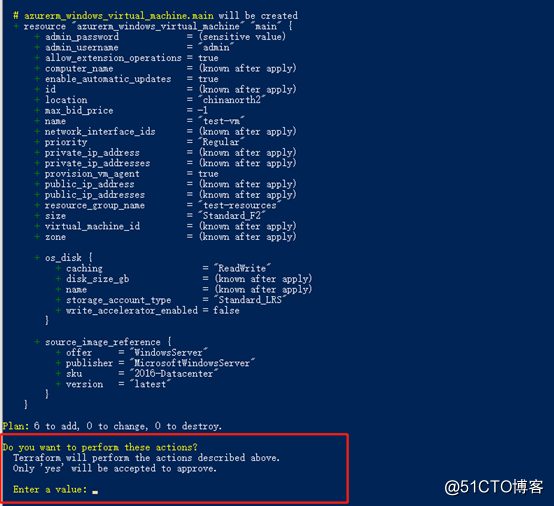
You can see that resources are being created all the time, and this output interface feels much friendlier than ARM Template
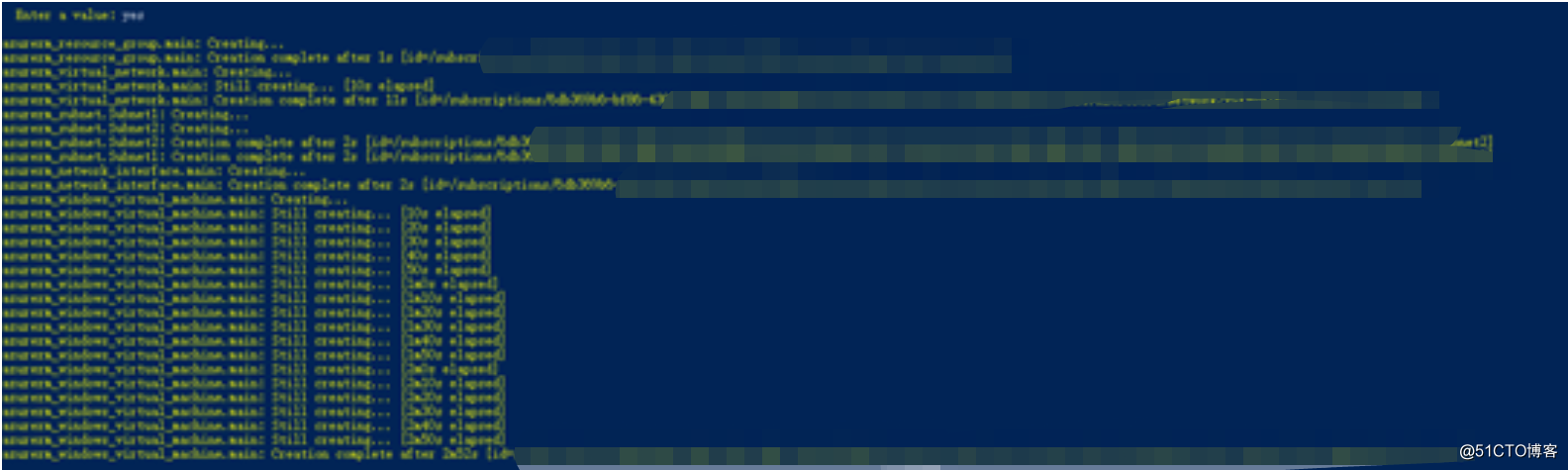
After the deployment is complete, log in to the portal, you can see that the resources have been created