Digital certificate in https
The digital certificate can ensure that the public key in the digital certificate is indeed the owner (Subject) of the certificate, or the certificate can be used to confirm the identity of the other party. In other words, when we get a digital certificate, we can judge who owns the digital certificate.
Certificate composition
First, use the Google browser to view the digital certificate translated by Baidu. The
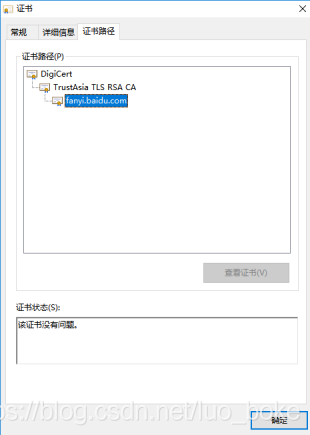

main parameters:
1. Issuer CA (certificate issuing authority)
indicates which authority issued the certificate, that is, the certificate creator. In the screenshot is the certification authority TrustAsia TLS RSA CA.

2. TLS
TLS certificate trust is a process of traceability from the user certificate to the intermediate certificate and then to the root certificate. The browser needs to find a trusted root certificate to trust your certificate.
TLS (Transport Layer Security) is a more secure upgraded version of SSL. Since the term SSL is more commonly used, we usually still refer to security certificates as SSL.TLS 证书一般有ECC、RSA 或 DSA 三种加密方式可以选择,RSA加密只是其中一种方式
3. Certificate format RSA
RSA an asymmetric encryption method
4. Certificate validity period The validity period of the
certificate starts from the start time to the end time, and the validity period generally starts from 12 months
5. Certificate user (Subject)
here is fanyi.baidu.com, which generally refers to the domain name of the website applying for the certificate
6. The public key is
2048bits hexadecimal array data, and the public key is used to decrypt server data
7. Signature algorithm (Signature algorithm)
The sha256RSA algorithm is used in the screenshot, which refers to the digital signature encryption algorithm of this certificate. When the client obtains the encrypted data from the server, it obtains the encrypted digital signature data after decryption by the public key RSA, and then obtains the fingerprint (hash value) of the communication content through the algorithm for data security verification.专用于防止传输过程中,内容信息和签名hash一起被篡改
8. The signature hash algorithm
screenshot uses the sha256 algorithm, which is used to calculate the hash value of the content information after RSA decryption. By comparing the calculated hash value with the hash value passed along with the content, you can verify whether the content is changed during transmission.
9. The fingerprint algorithm (Thumbprint algorithm)
screenshot is sha1. The principle is that when issuing a certificate, the issuer calculates the hash value (fingerprint) of the entire certificate according to the fingerprint algorithm (a hash algorithm) and puts it together with the certificate. When the user opens the certificate, he also calculates the certificate's value according to the fingerprint algorithm. The hash value (fingerprint), if it is consistent with the original fingerprint, it means that the certificate has not been modified.
这个指纹会使用"SecureTrust CA"这个证书机构的私钥用CA自己的数字证书的签名算法(Signature algorithm)加密后和证书放在一起。电脑系统一般默认自带CA的证书,该证书中有公钥和签名算法用于解密颁发的证书
10. When the certificate issuing authority (CA)
issues the certificate, the fingerprint and fingerprint algorithm of the certificate will be encrypted and then released together with the certificate to prevent someone from forging the corresponding digital certificate after modifying the fingerprint.这里的是用发证机构自己的私钥进行加密的
The public key (RSA algorithm) of the certificate issuing authority can be used to decrypt the fingerprint and fingerprint algorithm, which means that in addition to issuing certificates to others, the certificate issuing authority also has its own certificate.
Information transfer verification
Before the information is sent, a hash calculation is performed to obtain a hash value. According to the hash characteristics, this process is irreversible. When the information is sent out, the hash value is encrypted and sent out together with the information as a signature. After receiving the data, the receiver re-calculates the hash value of the information according to the signature algorithm, and compares the hash values of the two sources to verify whether the data has been tampered with.
The key point is why the hash value must be encrypted before being transmitted? This is to prevent people who would not be willing to modify the information content and the hash value at the same time to match, so the hash value needs to be encrypted before it is sent.
The digital certificate of the certificate issuing authority is already installed in the computer when we install the operating system. Operating system developers such as Microsoft will select certificate issuing organizations with good reputation and safety certification based on the evaluation of some authoritative organizations, and install their certificates in the system by default. The certificate authority holds the private key corresponding to its own digital certificate, and uses this private key to encrypt the fingerprint algorithm and fingerprint of the certificate issued by it (the certificate hash value is used as the digital signature of the certificate).
数字证书可以保证数字证书里的公钥确实是这个证书的所有者(Subject)的,或者证书可以用来确认对方的身份。
Why can we determine the subject of the certificate?
- After getting the digital certificate into the computer or mobile terminal, find the digital certificate of the corresponding certificate issuing authority according to the CA name of the certificate, and decrypt the digital signature.
- Decode the certificate's fingerprint and fingerprint encryption algorithm through the public key of the issuing authority, and use the fingerprint algorithm to calculate the fingerprint of the certificate again to obtain the real fingerprint. If the fingerprint contained in the certificate is consistent with the real fingerprint, the certificate has not been tampered with. The certificate is true and reliable, then the subject in the certificate is true and reliable.
to sum up
- The certificate is issued by a professional certificate issuing agency and consists of various information parameters such as user, validity period, signature algorithm and other information.
- The certificate public key is used to RSA decrypt the passed information to obtain the source information
- The signature algorithm is to verify whether the source information has been tampered with, the source information has been signed, and the fingerprint of the source information is calculated whether it matches
- The fingerprint and fingerprint algorithm seem to be the same as the signature algorithm, but their difference is that the fingerprint and fingerprint algorithm is to ensure the security and reliability of the certificate. The signature algorithm is to ensure the safety and reliability of the transmitted information.
该篇博客纯属个人观点和见解,如有错误恳请留言指正,万分感激!
Related Links