principle

The token is the temporary key of the system, which is equivalent to the account name and password. It is used to determine whether to allow this request and to determine which user this request belongs to. It allows you to access without providing a password or other credentials Network and system resources, these tokens persist in the system unless the system is restarted.
The biggest feature of tokens is randomness and unpredictability. Generally hackers or software cannot guess. There are many types of tokens. For example, access tokens represent the system objects of the subject of access control operations; secret security tokens are called authentication tokens. Or a hardware token is a physical device for computer identity verification, and a session token is a unique identity identifier in an interactive session.
Kerberos protocol
Kerberos protocol needs to be used in counterfeit token attacks, so before using counterfeit tokens, first introduce the kerberos protocol.
Kerberos is a network authentication protocol whose design goal is to provide powerful authentication services for client/server applications through a key system.
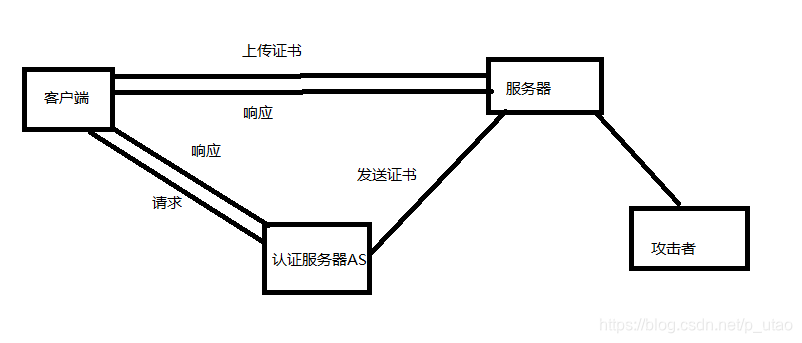
The client request certificate process is as follows:
- 客户端向认证服务器AS发送请求,要求得到服务器的证书
- AS收到请求后,将包含客户端密钥的加密证书响应发送给客户端,该证书包括服务器ticket(包括服务器密钥加密的客户机身份和一份会话密钥)和一个临时加密密钥(又称会话密钥,session key)当然,认证服务器也会给服务器发送一份该证书,用来使服务器认证登陆客户端的身份
- 客户端将ticket传送到服务器上,服务器确认该客户端的话,便允许它登陆服务器
- 客户端登陆成功后,攻击者就可以通过入侵服务器获取客户端的令牌
Exploit
At this point, suppose we have successfully obtained the shell of the target machine through a series of preliminary infiltrations. First enter the getuid command to view the obtained permissions, and then enter getsystem, and find that it fails.
getuid
Enter the use incognito command, and then enter list_tokens-u to list the available tokens
use incognito
Find a high-privileged authorization token and fake it. If you succeed, you can obtain the authorization. Then, use the incognito_token command to attack
incognito_token 目标主机名和登陆用户名
If the attack is successful, you can see that the permissions have been changed