Principle of mirror image hijacking attack based on auxiliary functions
In the Internet where anti-virus software is increasingly complete, ordinary viruses and Trojans, most of which are mainly loaded with system startup items, are increasingly difficult to break through the user's defense barrier, but at the same time, some viruses are "It not only bypassed the detection of anti-virus software, but also broke the system while hiding itself. How did these viruses catch the user's psychology and break through the user's system step by step.
Next, through this article, Metron No. 59 Security Lab will analyze the principle of mirror-based hijacking attacks based on auxiliary functions for everyone, and show you the huge harm and defense means of restoring such attacks.
0x01 Accessibility Introduction
The so-called auxiliary function is that in the Windows system, we can use a variety of key combinations to turn on or off specific functions, such as the commonly used win + ctrl + o to open the on-screen keyboard, win + u to open the setting center, and press 5 shifts to open sticky Keys and so on.

In addition, in order to improve the user experience, Microsoft very 'intimate' allows users to use these functions before logging in. According to this feature, some attackers are likely to run these functions without authorization through the Remote Desktop Protocol, although These functions are 'friendly' and not harmful, but we know that the reason why these functions can be run is actually the system commands that are run on the command line, for example
C: \ WINDOWS \ System32 \ Utilman.exe opens the setting center
C: \ WINDOWS \ System32 \ sethc.exe opens the sticky key
C: \ WINDOWS \ Syetem32 \ osk.exe opens the on-screen keyboard
The problem is that if we use the key combination to run the system command without being logged in, the auxiliary program that should have been opened is very safe but is replaced by another malicious program, which eventually leads to the situation without the user ’s knowledge. Get access to the system and leave a hidden backdoor .
How can the system commands for users to activate auxiliary functions become system commands for running their own malware? This is another technique: image hijacking .
0x02 Introduction to Mirror Hijacking
"Image hijacking", also known as "image hijacking", is also known as "IFEO" (Image File Execution Options). In a Windows NT architecture system, IFEO is intended to cause errors when running in the default system environment. The program execution body provides special environment settings. When an executable program is under the control of IFEO, its memory allocation is set according to the parameters of the program, and the Windows NT architecture system can use this registry entry to use the item that matches the executable file name as the program The control basis at the time of loading can finally set up a program's heap management mechanism and some auxiliary mechanisms. Probably Microsoft considered that adding path control would result in troublesome judgment and inflexible operation, and it would also easily lead to registry redundancy, so IFEO used the path-ignoring method to match the program file name it wanted to control.
Simply put, when I want to run A.exe, the result is B.exe, which means that in this case, the A program is hijacked by the B program, and the image hijacking virus is commonly used by modifying some registry. The key value of the item achieves the purpose of letting malicious programs such as Trojan horses run in the background if the user wants to run frequently used programs without the user's consciousness.
0x03 Principle and Implementation of Image Hijacking
Principle:
In order to achieve image hijacking, you need to first find the path of image hijacking in the registry, "HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ WindowsNT \ CurrentVersion \ Image File ExecutionOptions"
However, when trying to execute an executable file running request called from the command line, the WINDOWS NT system will first check whether the running program is an executable file, and if so, then check the format and then check whether it exists. From this we found that the culprit of the image hijacking is the parameter "Debugger" , which is the first parameter processed in IFEO,If this parameter is not empty, the system will process the program file name specified in the Debugger parameter as the program execution request that the user attempts to start, and only send the program the user attempts to start as the parameter of the program file name specified in the Debugger parameter. past.
The parameter "Debugger" was originally designed to allow programmers to directly enter the debugger to debug their own programs by double-clicking the program file. Now it has become a means of attack by viruses.
Let us think more deeply, what will happen when the changed entry is the entry where the anti-virus software is located. Undoubtedly, the anti-virus software has no way to work, not only bypassing the anti-virus software but also secretly executing its own malicious program, the average user simply does not expect that the registry entries of the anti-virus software will be tampered, which further increases the availability after the attack time. The danger is self-evident.
Recurrence:
Malicious code that modifies the registry:
#include <iostream>
#include <Windows.h>
using namespace std;
int test(){
DWORD dwDisposition;
HKEY hKey;
const char path[] = "C:\WINDOWS\System32\calc.exe";
RegCreateKeyExA(HKEY_LOCAL_MACHINE, "Software\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\chrome.exe", 0, NULL, 0, KEY_WRITE, NULL, &hKey, &dwDisposition);
RegSetValueExA(hKey, "Debugger", 0, REG_SZ, (BYTE*)path, (1 + ::lstrlenA(path)));
return 0;
}
int main(){
test();
return 0;
}
After the malicious program is run, the registry key of chrome.exe added in the Debugger=“C:\WINDOWS\System32\calc.exe”
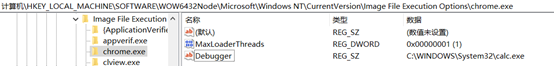
registry is modified, double-click to run chrome, and the calculator program should be opened when the web page should be opened, because the system preferentially executes "C: \ WINDOWS \ System32 \ calc.exe ". Caused a mirror hijacking attack.

0x04 Principle and implementation of image hijacking based on auxiliary functions
Security practitioners should not underestimate any kind of vulnerability, because when different vulnerabilities are combined, it is likely to produce an effect of 1 + 1> 2. This is well reflected in accessibility and mirror hijacking.
Earlier we mentioned that the auxiliary function is to execute system commands and allow users to run without logging in. Then when we use image hijacking attacks, changing the key values of these instructions in the registry IFEO may cause the attacker to not need to log in The system can run some malware.
Principle:
Modify the registry, add the Utilman.exe item in "HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion \ Image File Execution Option", add the debugger key in this item, the key value is the command C: \ WINDOWS to start cmd \ System32 \ cmd.exe.
When the attacker connects to the victim's computer through the remote desktop protocol, he only needs to use the key combination win + u. The setting center that should have been opened, but finally opened the cmd command line, through the command line, you can add users, open the registry, Running malware, adding hidden backdoors, and other attack methods are self-evident.
Reproduce:
Add Utilman.exe entry in the registry, add key-value pair Debugger = "C: \ WINDOWS \ System32 \ cmd.exe"
, run win + u on the login page, and open it without logging in Cmd command box

0x05 defense and removal methods
-
Because the malicious code of this type of attack needs to modify the Image File Execution Options, it must first have permission to read and write, so we can prevent image hijacking by restricting the user's read and write permissions to the registry. Open the registry editor, navigate to HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ WindowsNT \ CurrentVersion \ ImageFileExecutionOptions \, select this item, right-click → permissions → advanced, cancel the write permissions of administrator and system users.
-
Because the image hijacking needs to add auxiliary function entries in the registry, check the program name under the registry path of "HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion \ Image File Execution Option". Some commonly used auxiliary function table entries are as follows : Utilman.exe, stch.exe, osk.exe, etc.
-
Based on the concept of zero trust, you can choose to delete unnecessary entries that may have security risks, and directly disable the auxiliary functions. Open the registry editor, navigate to HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ WindowsNT \ CurrentVersion \, and delete the "ImageFileExecutionOptions" item.
