A, ASA and PIX Basic Configuration
1, ASA firewall configuration
1, GNS configuration
Because the version of GNS3 use may be different, step gns asa firewall configuration may be different
Direct qemu options can be configured directly in the low version of gns, the reference:https://blog.51cto.com/dldxzjr/1905682
Disposed at a higher version of gns can refer to:https://wenku.baidu.com/view/8934accc48649b6648d7c1c708a1284ac850059c.html
2, simple firewall set command
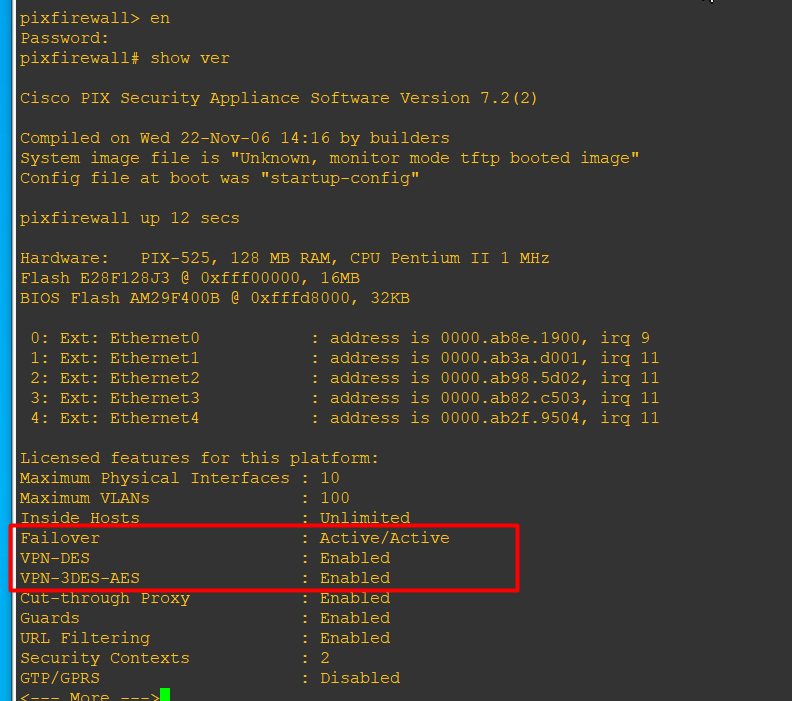
show version
show running-config
show activation-key 查看激活秘钥
activation-key key-values 设置激活秘钥
write mem 将配置保存到非易失flash,重启或断电都不会对配置产生影响
no shutdown 使借口处于启用
show interface ip breif 提供接口的简短概要
interface 接口
nameif inside/outside/dmz
ip address ip地址 掩码
speed auto #连接速度,有10/100/1000Mbps等
duplex auto #双工模式,有Half/Full为半双工/全双工模式
#一般网卡都为Auto/Auto适配出来的情况一般为100M全双工模式
#防火墙上设置静态路由,最多可以配置3个不同的默认路由
例:
指向外部接口上的网关192.168.1.1的路由 route outside 0.0.0.0 0.0.0.0 192.168.1.1 1
可通过内部接口上的网关192.168.254.2找到网络172.21.0.0/16 route inside 172.21.0.0 255.255.0.0 192.168.254.2 1
删除则直接加一个no
show route
#
show xlate
show conn
Example:
###配置ASA防火墙
ciscoasa# show int ip b
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0 unassigned YES unset administratively down up
GigabitEthernet1 unassigned YES unset administratively down up
GigabitEthernet2 unassigned YES unset administratively down up
GigabitEthernet3 unassigned YES unset administratively down up
ciscoasa# conf t
ciscoasa(config)# int g0
ciscoasa(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
ciscoasa(config-if)# ip address 13.0.1.1 255.255.255.0
ciscoasa(config-if)# no sh
ciscoasa(config-if)# show int ip b
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0 13.0.1.1 YES manual up up
GigabitEthernet1 unassigned YES unset administratively down up
GigabitEthernet2 unassigned YES unset administratively down up
GigabitEthernet3 unassigned YES unset administratively down up
###配置pc1的ip
PC1> show ip
NAME : PC1[1]
IP/MASK : 0.0.0.0/0
GATEWAY : 0.0.0.0
DNS :
MAC : 00:50:79:66:68:00
LPORT : 10012
RHOST:PORT : 127.0.0.1:10011
MTU: : 1500
PC1> ip 13.0.1.2 13.0.1.1 24
Checking for duplicate address...
PC1 : 13.0.1.2 255.255.255.0 gateway 13.0.1.1
PC1> show ip
NAME : PC1[1]
IP/MASK : 13.0.1.2/24
GATEWAY : 13.0.1.1
DNS :
MAC : 00:50:79:66:68:00
LPORT : 10012
RHOST:PORT : 127.0.0.1:10011
MTU: : 1500
PC1>
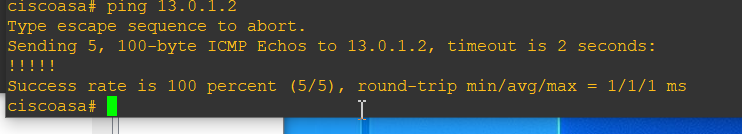
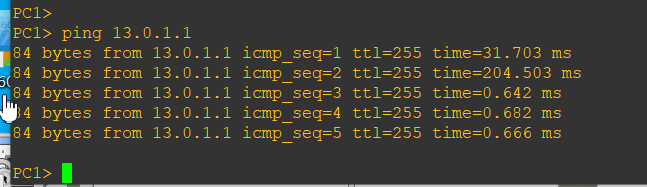
ping test:
2, pix firewall configuration
There needs to be activated by step installation

activation-key key
Close to restart the pix firewall:
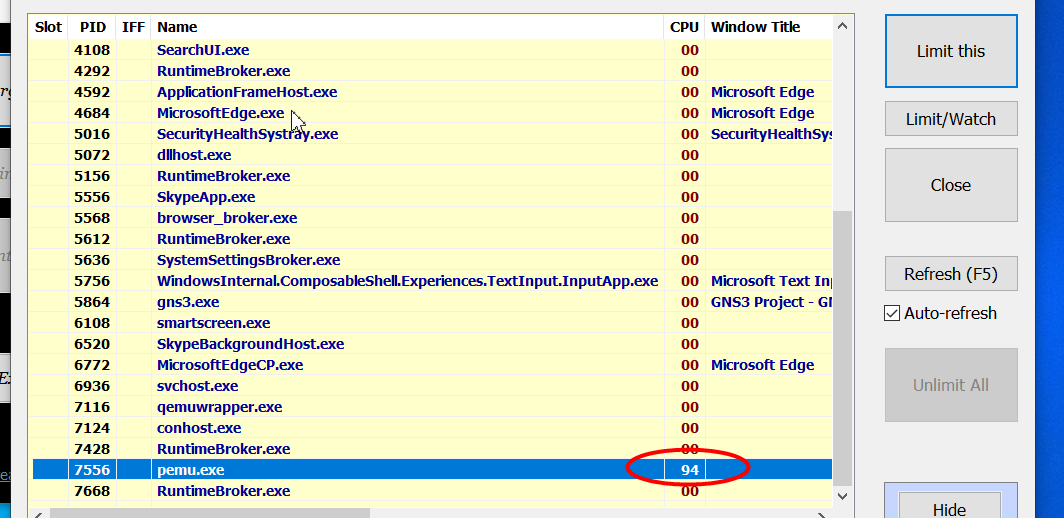
Another point to note is that there is a process pemu take up a lot of cpu resources, resulting in very slow, it can be used to limit the pix BES runtime:
Examples
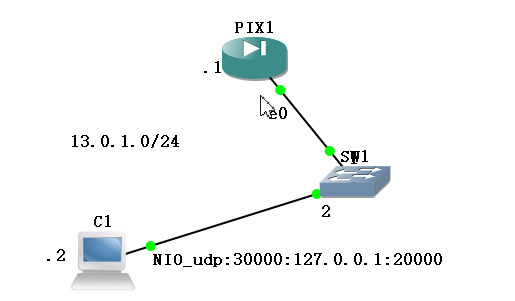
pix:
pixfirewall> en
Password:
pixfirewall# conf t
pixfirewall(config)# exit
pixfirewall# show int ip b
Interface IP-Address OK? Method Status Protocol
Ethernet0 unassigned YES unset administratively down down
Ethernet1 unassigned YES unset administratively down down
Ethernet2 unassigned YES unset administratively down down
Ethernet3 unassigned YES unset administratively down down
Ethernet4 unassigned YES unset administratively down down
pixfirewall# conf t
pixfirewall(config)# int e0
pixfirewall(config-if)# ip address 13.0.1.1 255.255.255.0
pixfirewall(config-if)# no sh
pixfirewall(config-if)# show int ip b
Interface IP-Address OK? Method Status Protocol
Ethernet0 unassigned YES manual up up
Ethernet1 unassigned YES unset administratively down down
Ethernet2 unassigned YES unset administratively down down
Ethernet3 unassigned YES unset administratively down down
Ethernet4 unassigned YES unset administratively down down
pixfirewall(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
pixfirewall(config-if)# show int ip b
Interface IP-Address OK? Method Status Protocol
Ethernet0 13.0.1.1 YES manual up up
Ethernet1 unassigned YES unset administratively down down
Ethernet2 unassigned YES unset administratively down down
Ethernet3 unassigned YES unset administratively down down
Ethernet4 unassigned YES unset administratively down down
pc1
VPCS[1]> ip 13.0.1.2 13.0.1.1 24
Checking for duplicate address...
PC1 : 13.0.1.2 255.255.255.0 gateway 13.0.1.1
VPCS[1]> show ip
NAME : VPCS[1]
IP/MASK : 13.0.1.2/24
GATEWAY : 13.0.1.1
DNS :
MAC : 00:50:79:66:68:00
LPORT : 20000
RHOST:PORT : 127.0.0.1:30000
MTU: : 1500
VPCS[1]>
ping
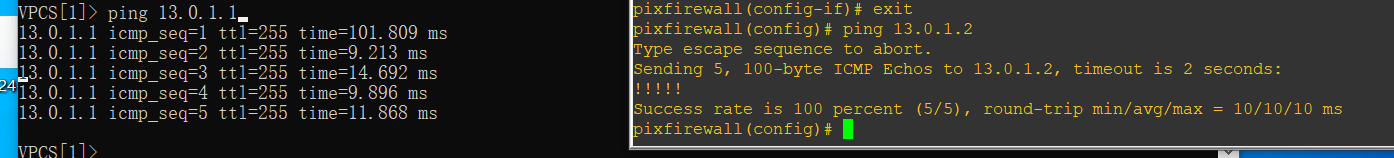
Two, PIX-NAT
1, pix configure dynamic NAT

Basic commands, for example:
show int ip b
hostname
ip address
nameif
security number
show conn 显示所有的活动连接
show conn detail
show local-host
show xlate 显示翻译(xlate)槽位的内容
show xlate detail
#添加acl,访问规则
1)创建标准访问列表
access-list [list-number] [permit|deny] [source-address] [wildcard mask] [log]
access-group list-number in int 接口名
#静态NAT
static [(internal_if_name, external_if_name)] global_ip local_ip[netmask network_mask][max_conns
[em_limit]] [norandomseq]
例:static (inside,outside) 13.0.1.3 192.168.1.2 将本地地址192.168.1.2转换为全局地址13.0.1.3
#static PAT
static [(real_interface, mapped_interface)] {tcp | udp} {mapped_ip | interface}
mapped_port {real_ip real_port [netmask mask]
例:dmz:172.16.1.9 outside:192.168.0.9
static (dmz,outside) tcp 192.168.0.9 ftp 172.16.1.9 ftp netmask 255.255.255.255
#动态NAT
nat (inside) 1 192.168.1.0 255.255.255.0
global (outside) 1 12.0.1.0-12.0.1.9 netmask 255.255.255.0
#PAT
nat (inside) 1 192.168.1.0 255.255.255.0
global (outside) 1 12.0.1.9 netmask 255.255.255.0
#nat 0
nat (dmz) 0 192.168.0.9 255.255.255.255
#
no global (outside) 1 12.0.1.0-12.0.1.9 netmask 255.255.255.0
route if_name ip_address netmask gateway_ip [metric] 为接口口if_name定义一条静态或缺省路由
#
debug icmp trace
no debug icmp trace
#
logging on
show logging
no logging on
show capture inside
#
show users
show run nat-control
show conn detail
show xlate
Configuring pix
pixfirewall> en
Password:
pixfirewall# conf t
pixfirewall(config)# int e0
pixfirewall(config-if)# ip address 192.168.1.1 255.255.255.0
pixfirewall(config-if)# no sh
pixfirewall(config-if)# int e1
pixfirewall(config-if)# ip address 13.0.1.1 255.255.255.0
pixfirewall(config-if)# no sh
pixfirewall(config-if)# exit
pixfirewall(config)# exit
pixfirewall# show int ip b
Interface IP-Address OK? Method Status Protocol
Ethernet0 unassigned YES manual up up
Ethernet1 unassigned YES manual up up
Ethernet2 unassigned YES unset administratively down down
Ethernet3 unassigned YES unset administratively down down
Ethernet4 unassigned YES unset administratively down down
pixfirewall# conf t
pixfirewall(config)# int e0
pixfirewall(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
pixfirewall(config-if)# int e1
pixfirewall(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
pixfirewall(config-if)# exit
pixfirewall(config)# exit
pixfirewall# show int ip b
Interface IP-Address OK? Method Status Protocol
Ethernet0 192.168.1.1 YES manual up up
Ethernet1 13.0.1.1 YES manual up up
Ethernet2 unassigned YES unset administratively down down
Ethernet3 unassigned YES unset administratively down down
Ethernet4 unassigned YES unset administratively down down
pixfirewall# conf t
pixfirewall(config)# access-list test1 permit icmp any any
pixfirewall(config)# access-group test1 in int outside
pixfirewall(config)# nat (inside) 1 192.168.1.0 255.255.255.0
pixfirewall(config)# global (outside) 1 13.0.1.4-13.0.1.6 netmask 255.255.255.0
R1
R1#ip route 0.0.0.0 0.0.0.0 192.168.1.1
!因为我们是用路由器R1模拟的主机,所以要么关闭路由功能,配置网关;要么添加一条路由让路由器发出的消息从192.168.1.1出去
2、static NAT
Configuring pix
pixfirewall> en
Password:
pixfirewall# conf t
pixfirewall(config)# int e0
pixfirewall(config-if)# ip address 192.168.1.1 255.255.255.0
pixfirewall(config-if)# no sh
pixfirewall(config-if)# int e1
pixfirewall(config-if)# ip address 13.0.1.1 255.255.255.0
pixfirewall(config-if)# no sh
pixfirewall(config-if)# int e0
pixfirewall(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
pixfirewall(config-if)# int e1
pixfirewall(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
pixfirewall(config-if)# exit
pixfirewall(config)# show running-config static
pixfirewall(config)# static (inside,outside) 13.0.1.3 192.168.1.2
pixfirewall(config)# static (inside,outside) 13.0.1.4 192.168.1.3
pixfirewall(config)# route outside 0 0 13.0.1.2
pixfirewall(config)# exit
pixfirewall# show int ip b
Interface IP-Address OK? Method Status Protocol
Ethernet0 192.168.1.1 YES manual up up
Ethernet1 13.0.1.1 YES manual up up
Ethernet2 unassigned YES unset administratively down down
Ethernet3 unassigned YES unset administratively down down
Ethernet4 unassigned YES unset administratively down down
pixfirewall(config)# access-l
pixfirewall(config)# access-list acl-outside permit icmp any any
pixfirewall(config)# access-g
pixfirewall(config)# access-group acl-outside in int outside
pixfirewall(config)# exit
pixfirewall# show int ip b
Interface IP-Address OK? Method Status Protocol
Ethernet0 192.168.1.1 YES manual up up
Ethernet1 13.0.1.1 YES manual up up
Ethernet2 unassigned YES unset administratively down down
Ethernet3 unassigned YES unset administratively down down
Ethernet4 unassigned YES unset administratively down down
测试:
pixfirewall# ping 13.0.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 13.0.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/14/20 ms
pixfirewall# ping 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/10/10 ms
pixfirewall# show running-config
: Saved
:
PIX Version 7.2(2)
!
hostname pixfirewall
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet1
nameif outside
security-level 0
ip address 13.0.1.1 255.255.255.0
!
interface Ethernet2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet4
shutdown
no nameif
...
pixfirewall#
R1 arrangement
R1#en
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#int f0/0
R1(config-if)#ip address 13.0.1.2 255.255.255.0
R1(config-if)#no sh
R1(config-if)#
*Mar 1 00:19:52.959: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up
*Mar 1 00:19:53.959: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
R1(config-if)#int f1/0
R1(config-if)#ip address 14.0.1.1 255.255.255.0
R1(config-if)#no sh
R1(config-if)#
*Mar 1 00:25:10.991: %LINK-3-UPDOWN: Interface FastEthernet1/0, changed state to up
*Mar 1 00:25:11.991: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet1/0, changed state to up
R1(config-if)#
pc1 \ pc2 \ pc3 configuration
ping test
192.168.1.2 ping 13.0.1.2
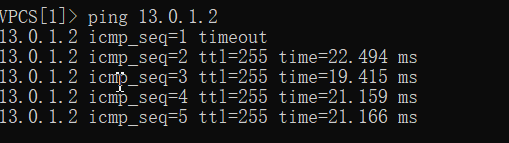
192.168.1.3 ping 14.0.1.2

14.0.1.2 ping 192.168.1.2
3、PAT
Like the dynamic NAT, the external address pool but only one public network ip, mainly through the network address translation sockets (ip + port embodiment)
4, pix firewall ---- two interface testing (inside, outside)
. . Several days did not open GNS3, found in front of ios be all gone. Honestly and reconfigure it again
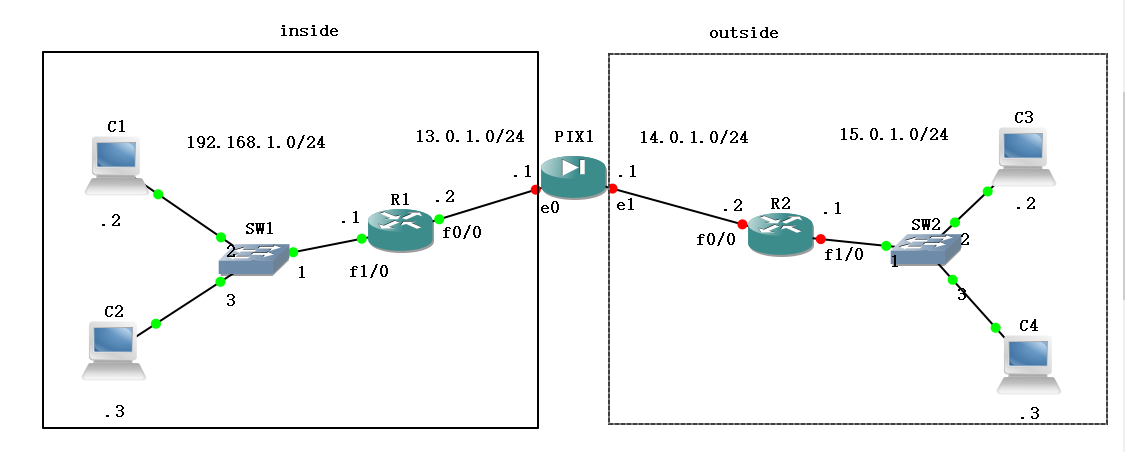
R1 arrangement
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#int f1/0
R1(config-if)#ip address 192.168.1.1 255.255.255.0
R1(config-if)#no sh
R1(config-if)#
*Mar 1 00:01:04.391: %LINK-3-UPDOWN: Interface FastEthernet1/0, changed state to up
*Mar 1 00:01:05.391: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet1/0, changed state to up
R1(config-if)#int f0/0
R1(config-if)#ip address 13.0.1.2 255.255.255.0
R1(config-if)#no sh
R1(config-if)#
*Mar 1 00:01:42.527: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up
*Mar 1 00:01:43.527: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
R1(config-if)#exit
R1(config)#ip route 14.0.1.0 255.255.255.0 13.0.1.1
R1(config)#ip route 15.0.1.0 255.255.255.0 13.0.1.1
PC1, PC2, PC3, PC4 configuration
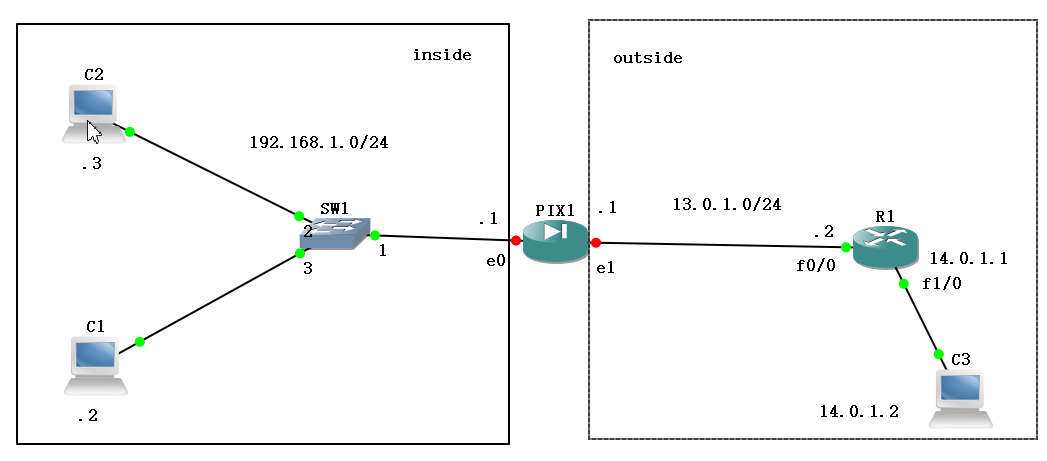
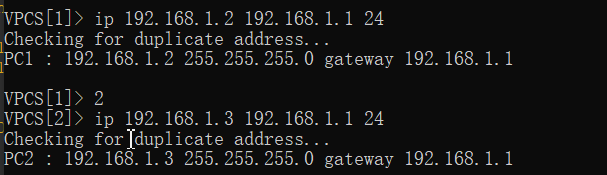
VPCS[1]> ip 192.168.1.2 192.168.1.1 24
Checking for duplicate address...
PC1 : 192.168.1.2 255.255.255.0 gateway 192.168.1.1
VPCS[1]> 2
VPCS[2]> ip 192.168.1.3 192.168.1.1 24
Checking for duplicate address...
PC2 : 192.168.1.3 255.255.255.0 gateway 192.168.1.1
VPCS[2]> 3
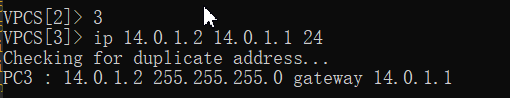
VPCS[3]> ip 15.0.1.2 15.0.1.1 24
Checking for duplicate address...
PC3 : 15.0.1.2 255.255.255.0 gateway 15.0.1.1
VPCS[3]> 4
VPCS[4]> ip 15.0.1.3 15.0.1.1 24
Checking for duplicate address...
PC4 : 15.0.1.3 255.255.255.0 gateway 15.0.1.1
VPCS[4]>
R2 Configuration
R2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#int f0/0
R2(config-if)#ip address 14.0.1.2 255.255.255.0
R2(config-if)#no sh
R2(config-if)#
*Mar 1 00:00:51.907: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up
*Mar 1 00:00:52.907: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
R2(config-if)#int f1/0
R2(config-if)#ip address 15.0.1.1 255.255.255.0
R2(config-if)#no sh
R2(config-if)#exit
R2(config)#ip route 13.0.1.0 255.255.255.0 14.0.1.1
R2(config)#ip route 192.168.1.0 255.255.255.0 14.0.1.1
#可以给路由器配置远程终端,用telnet来丰富一下测试
R2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#line vty 0 4
R2(config-line)#password zwish
R2(config-line)#end
R2#
*Mar 1 01:35:20.871: %SYS-5-CONFIG_I: Configured from console by console
R2#
PIX configuration
pixfirewall# conf t
pixfirewall(config)# int e0
pixfirewall(config-if)# ip address 13.0.1.1 255.255.255.0
pixfirewall(config-if)# no sh
pixfirewall(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
pixfirewall(config-if)# int e1
pixfirewall(config-if)# ip address 14.0.1.1 255.255.255.0
pixfirewall(config-if)# no sh
pixfirewall(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
pc1, R1 to ping the pix of e0, you can look through, may continue
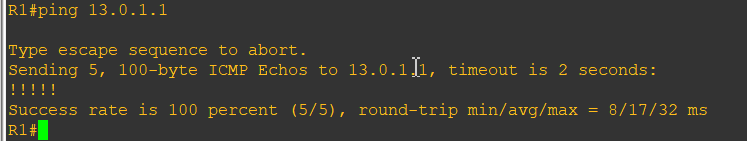
pixfirewall(config-if)# access
pixfirewall(config-if)# access-
pixfirewall(config-if)# access-l
pixfirewall(config-if)# access-list acl-1 permit icmp any any
pixfirewall(config)# access-g
pixfirewall(config)# access-group acl-1 in int
pixfirewall(config)# access-group acl-1 in interface outside
pixfirewall(config)# nat (inside) 1 0 0
pixfirewall(config)# global (outside) 1 14.0.1.3-14.0.1.6 netmask 255.255.255.0
#下面是配置回程路由
pixfirewall(config)# route inside 192.168.1.0 255.255.255.0 13.0.1.2
pixfirewall(config)# route outside 15.0.1.0 255.255.255.0 14.0.1.2
pixfirewall(config)#
test
pc1 ping R2

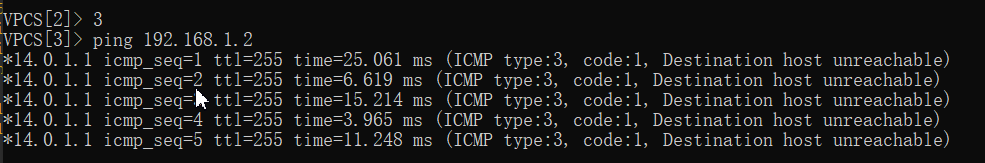
pc1 ping pc3
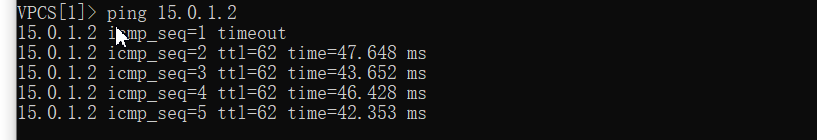
pc3 ping pc1

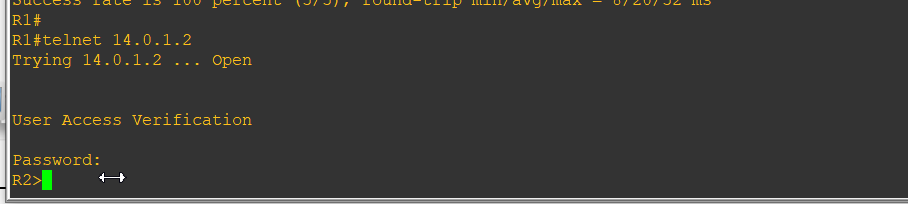
R1 telnet login R2 (because I did not use a router simulation host, with R1, if the router is simulated host, proceed directly to telnet PC1)