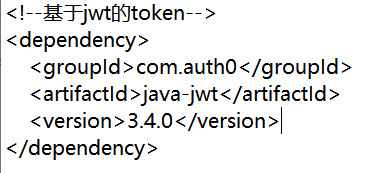
1. Import dependence
2. The first import of token generation and compilation tools JwtUtil.java (placed at the end of the tools)
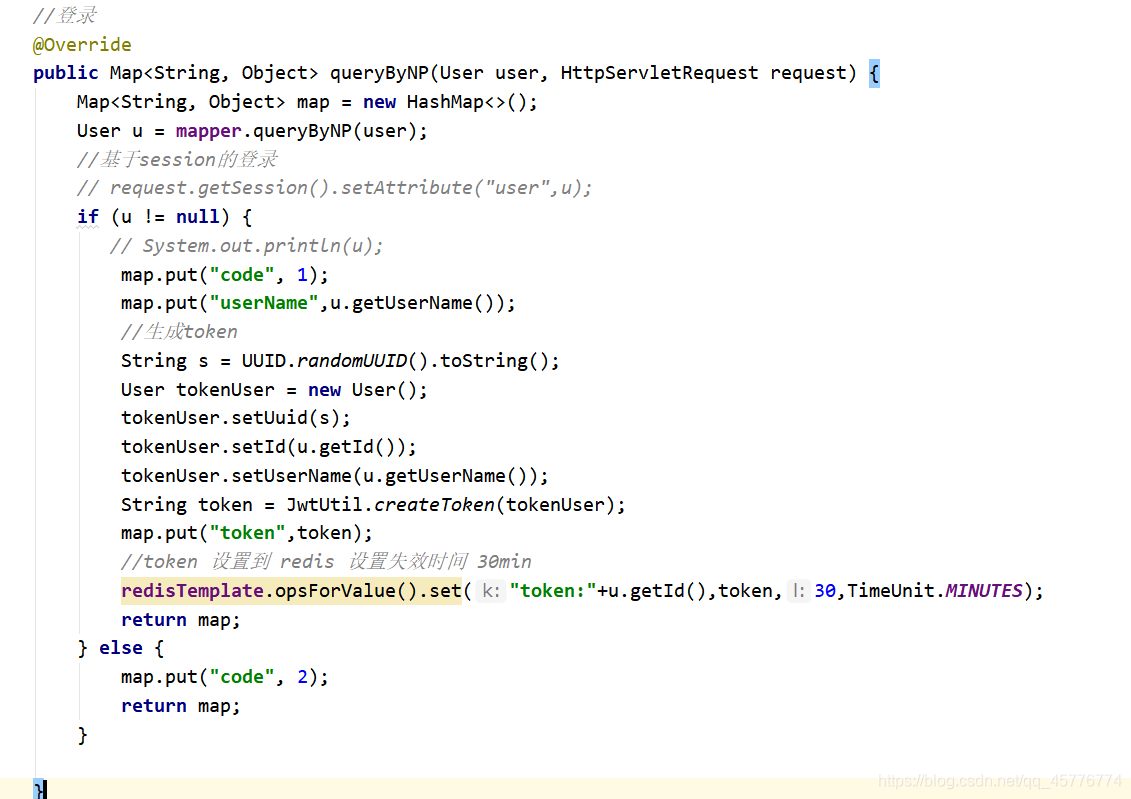
Returns the object 3. After the user service based on the service layer generated by a successful login authentication UUID, a user id, user name as a token (Do not use a password to generate the token secret operation) and the resulting token is returned to the front end to collectively as FIG.
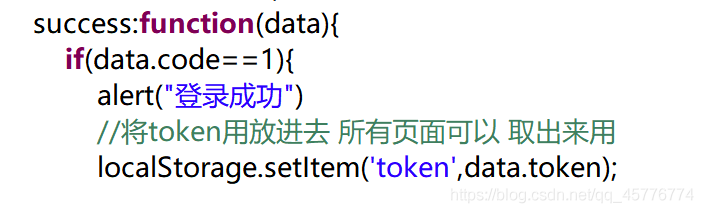
4. The front end may be removed and the token to the front page by localStorage.setItem () may take all token value using the following :( ajax request to herein as subjects following a successful callback function)
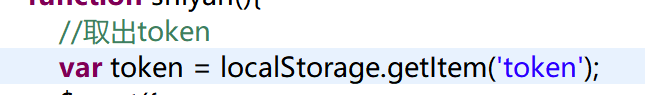
other ajax 5. After a successful login request can used localStorage.getItem ( "token") acquired token
and the first token is set to the request to access the inside of the rear end
setting request header (ajax request tagging below):
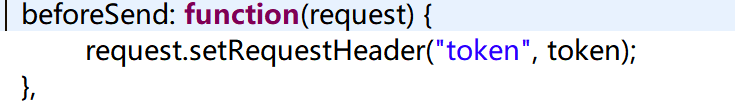
This request is transmitted to the rear end of the follower
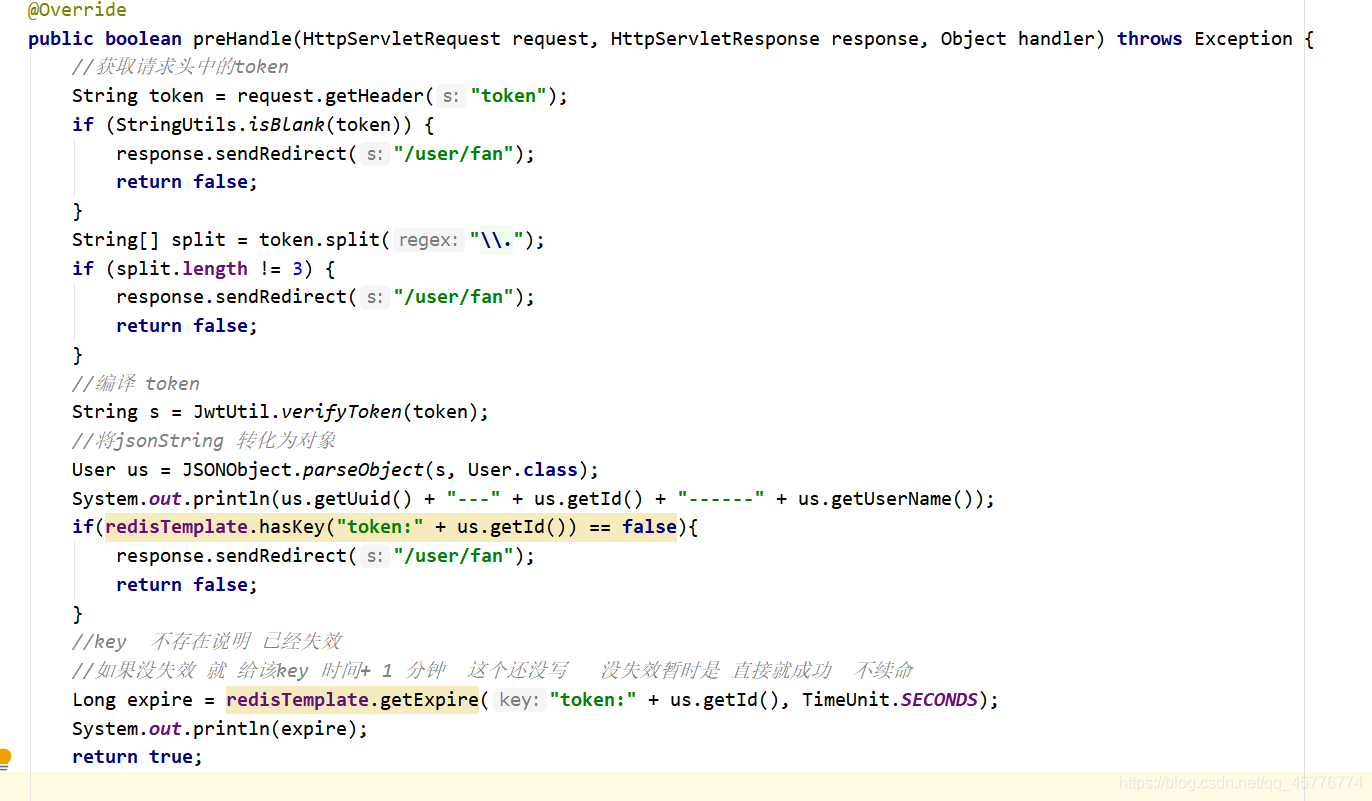
6. Analyzing the rear end of the interceptor
1) to obtain the first token and determines whether or not there token by request.getHead ( "token")
exists determines whether the length of the divided token 3 because I am here generated using three uuid id username 3 If the length attribute sure the job. (If not using the token redis confirmed the presence of release can intercept equal to)
2) after determining if token can be compiled into the acquisition memory to the object (this is for convenience using uuid / id used to process redis get token is invalid and other operations that use their own redis were on the line)
---------------------------------------- JwtUtil tools ------- -----------------------------------------------
Package Penalty for COM. fh.util;
import com.alibaba.fastjson.JSON;
import com.auth0.jwt.JWT;
import com.auth0.jwt.JWTVerifier;
import com.auth0.jwt.algorithms.Algorithm;
import com.auth0.jwt.interfaces.DecodedJWT;
public class JwtUtil {
private static final String SECRET_KEY = "sd237#@sd!$%sdk-=";
/**
* 加密生成token
*
* @param object 载体信息
* @param <T>
* @return
*/
public static <T> String createToken(T object) {
try {
final Algorithm signer = Algorithm.HMAC256(SECRET_KEY);//生成签名
String token = JWT.create()
.withSubject(JSON.toJSONString(object))//主题,科目
.sign(signer);
return token;
} catch (Exception e) {
e.printStackTrace();
throw new RuntimeException(e.getMessage());
}
}
/**
* 解析验证token
*
* @param token 加密后的token字符串
* @return
*/
public static String verifyToken(String token) {
try {
Algorithm algorithm = Algorithm.HMAC256(SECRET_KEY);
JWTVerifier verifier = JWT.require(algorithm).build();
DecodedJWT jwt = verifier.verify(token);
return jwt.getSubject();
} catch (Exception e) {
throw new RuntimeException(e.getMessage());
}
}
}
