Data is one of the important production factors in the new era, and work related to data assetization is accelerating. Starting from October 1 this year, the "Data Asset Valuation Guidance" formulated by the China Asset Appraisal Association has been officially implemented. At the same time, the "Interim Provisions on Accounting Treatment Related to Enterprise Data Resources" has recently been converted into a formal draft and will also come into effect on January 1 next year.
The "Interim Provisions" stipulate that if the data resources used by an enterprise meet the definition and recognition conditions stipulated in the "Accounting Standards for Business Enterprises No. 6 - Intangible Assets" (Financial Accounting [2006] No. 3), they shall be recognized as intangible assets; the daily activities of the enterprise Data resources held in the enterprise and ultimately intended for sale shall be recognized as inventory if they meet the definition and recognition conditions stipulated in the "Accounting Standards for Business Enterprises No. 1 - Inventory" (Financial Accounting [2006] No. 3); enterprise sales are not recognized For data resources that are assets, relevant income should be recognized in accordance with income standards and other regulations.
What is data asset entry into the table?
Before evaluating the value of data assets and entering them into tables, we first need to clarify what data assets are. Data assets refer to various data resources owned by enterprises or organizations, including but not limited to customer information, sales data, financial data, production data, etc.
Data asset inclusion refers to the process of incorporating data assets into the asset management system of an enterprise or organization and effectively managing and utilizing them. The "Interim Provisions" clearly recognize data assets in the table from a policy perspective for the first time, allowing the development costs of data resources that could only be expensed to be recognized as assets after meeting certain conditions.
The purpose of recording data assets is to ensure that enterprises or organizations recognize, manage and protect the value of data assets. Adding data assets to the table will test the company's data governance level, and at the same time help data-driven companies attract external financing, optimize financial structure, and enhance company value. By adding data assets to tables, enterprises can better manage the acquisition, storage, processing, sharing and use of data assets, and improve the reliability, accuracy and security of data.
How to enter data assets into the table?
If an enterprise expects to realize the accounting of data assets into the balance sheet, it needs to plan in advance and carry out the preparation work before the inclusion in the balance sheet, for example, improve data lineage management, strengthen data collection and governance capabilities, do a good job in data governance quality assessment, and conduct productization The data resources are graded and classified and passed through economic evaluation and value assessment.
In short, the entry of data assets into the table is inseparable from solid data governance preparations in the early stage. So how should the standardized management of data assets be achieved?
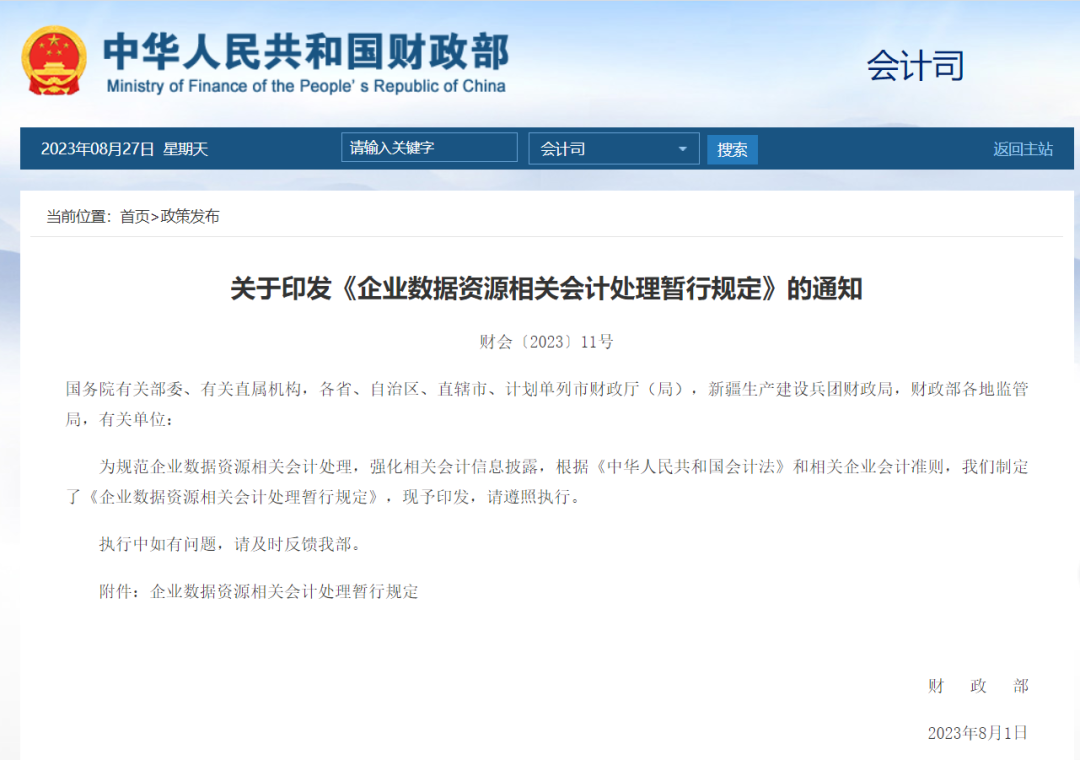
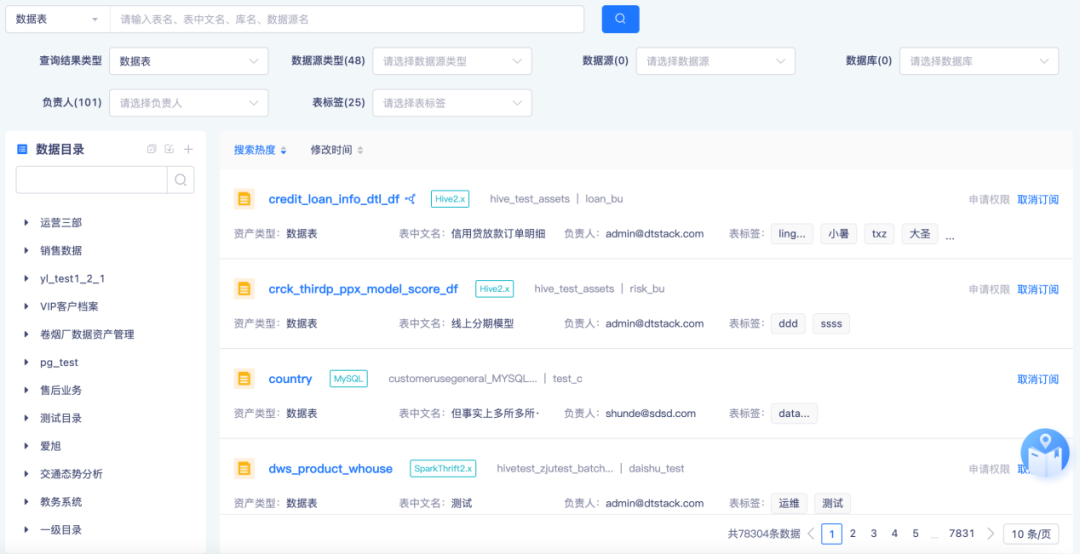
Through Kangaroo Cloud's " data asset management platform ", enterprises can formulate metadata models , data standards and other specifications, collect and maintain complete metadata information, open up the data relationship network, and realize data standardization and asset management. Monitor data quality through rule configuration, continue data governance, build an enterprise-level metadata center , inventory enterprise data assets, provide a "complete, unified, and transparent" metadata foundation for data value mining, and achieve standardized management of assets in the table.
Step 1: Collect and manage metadata
First, in the data asset confirmation process, the identity and boundaries of data assets are clarified through functions such as metadata collection, metamodel definition, metadata maintenance, and metadata query.
● Metadata collection
Through internal research, sort out the business data, lake warehouse data or application data that the enterprise needs to conduct unified metadata management , collect the data source connection information of various data, apply for read-only metadata permissions from each data person in charge, and conduct metadata collection.
● Metamodel definition
Communicate offline with the person in charge of each data source about the lack of metadata, discuss metadata model design specifications, list the metadata items that need to be maintained for each type of data source, and enter them into the platform.
● Metadata maintenance
Assign a responsible person to each piece of metadata to ensure that the metadata maintenance work can be assigned to the person responsible.
The person in charge needs to completely maintain the missing metadata information according to the arrangement, and all maintenance personnel can add custom labels to the data assets to facilitate quick query of data asset information according to label classification. Managers can regularly count metadata integrity and track the progress of metadata maintenance . They can conduct regular statistics based on multiple dimensions such as data sources and responsible persons, discover problems in a timely manner, and urge responsible persons to improve metadata information.
● Metadata query
Provide a unified, complete and convenient metadata query portal for all metadata query users , supporting multiple search modes and filter conditions to quickly locate metadata. At the same time, based on the query results, we can continuously discover missing metadata and provide feedback to promote metadata. maintenance work.
Step 2: Build data standards and data models
An important step in data governance is to sort out what data the enterprise has and integrate the data. For this purpose, a set of data standards and data models must be established to standardize the data.
● Data standards
Standardizes field-level standard information for data assets . Through root management and standard management, the standard information of the fields in the data table is defined, such as field name, field Chinese name, field type, field length and other information.
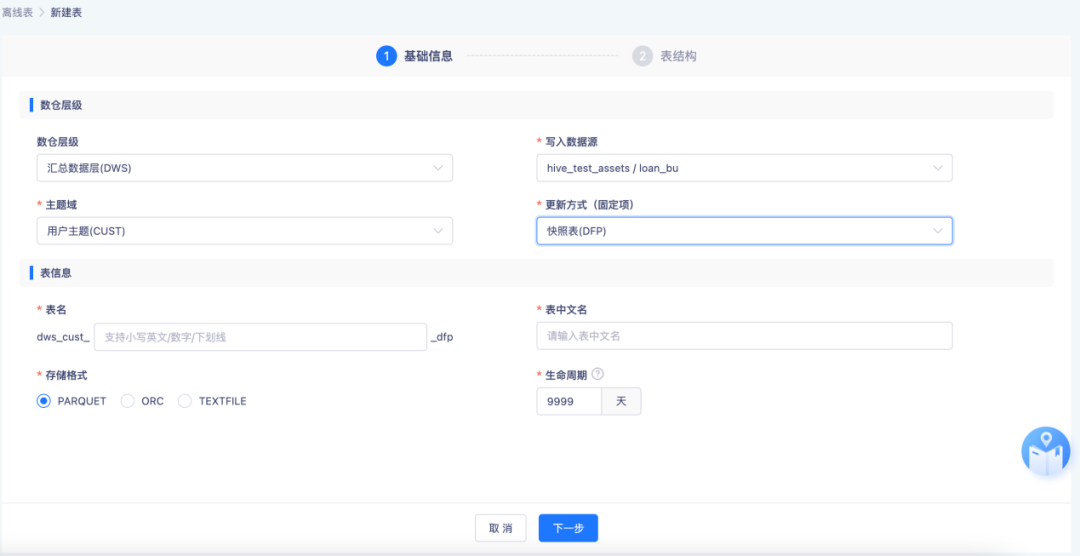
● Data model
Standardize data table design logic for data assets. Through standardized design, the hierarchical structure and theme information of the data table are defined, table names are automatically spliced according to model elements, and field information is automatically brought in according to data standards to achieve standardized design of data tables.
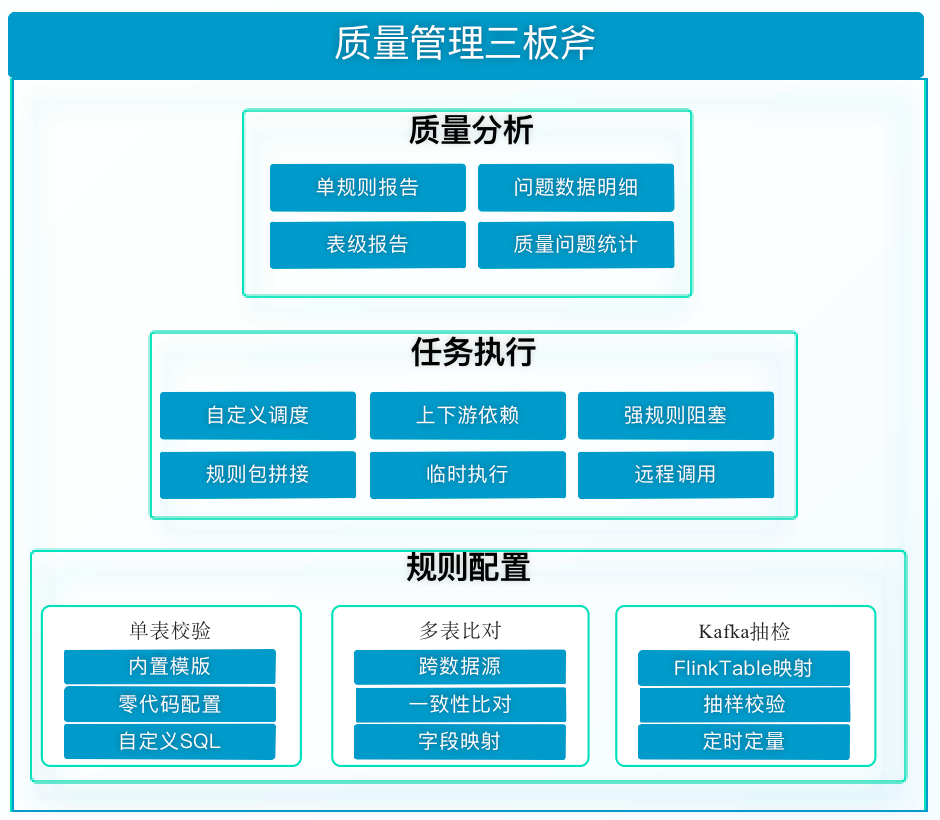
Step Three: Data Quality Verification
Starting from business scenarios, solve actual business data problems and standardize asset data.
Configure rules for data tables that require data quality verification . The platform has built-in standard rule templates such as completeness, accuracy, standardization, and uniqueness, which can realize code-free configuration of single-table verification rules and multi-table comparison rules. For complex scenarios, custom SQL is also supported for rule configuration. After configuring the rules, task execution is performed and quality reports are generated.
Step 4: Continuous Data Governance
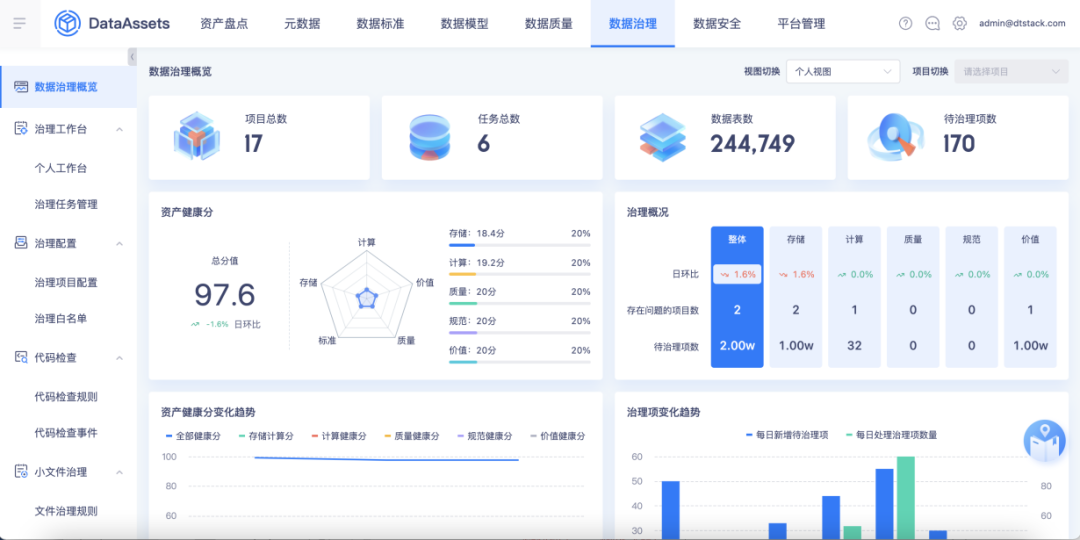
Build a data governance workbench to manage data assets from multiple dimensions: storage, computing, specification, quality, and value.
The data governance situation can be displayed from a personal perspective, a project perspective, and a panoramic perspective, and the data governance problem handling process of initiating governance tasks -> recording issues to be handled -> assigning handlers -> problem handling -> automatically rechecking the entire link can be realized closed loop. Through continuous management of data assets, enterprises are encouraged to improve data specifications, optimize data quality, save resources, reduce costs and increase efficiency.
Step Five: Data Security Control
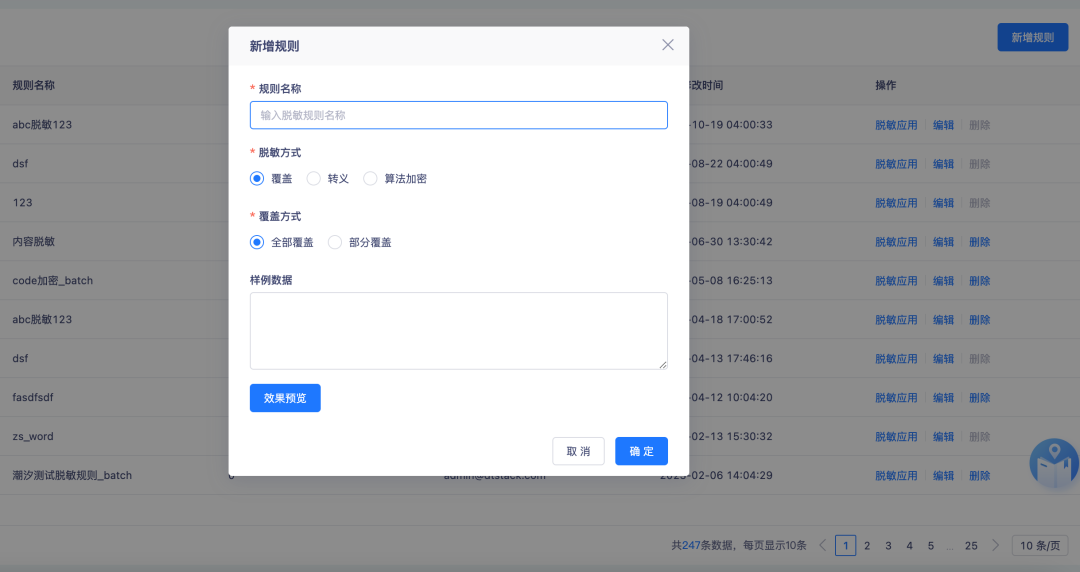
Standardized data management is inseparable from data security control. Kangaroo Cloud's " data asset management platform " supports data desensitization rule management , data permission management and data classification .
For some sensitive data, such as mobile phone numbers, ID numbers and other private information, desensitization rules can be customized for desensitization display; the platform supports permission configuration at the data source, database, data table and row and column levels, and supports permission application and permissions. Grant and permission recovery operations enable fine-grained control of data permissions.
The significance of entering data assets into the table
The pace of implementation of the policy of adding data assets to the balance sheet is faster than expected, marking the country’s firm determination to use data as a factor of production. Putting data assets into tables can improve the data management efficiency of enterprises. By putting data assets into the database, it is easier for enterprises to classify, store, and retrieve data, and realize the unified collection of data, instead of data information scattered in various systems and files.
At the same time, adding assets to the table also greatly improves data security. By encrypting data and controlling permissions, it ensures that only authorized personnel can access and modify the data. Through standardized management and continuous governance of data, it can help enterprises optimize storage resources. , avoid resource waste.
Therefore, enterprises should attach great importance to the work of adding assets to the balance sheet, strengthen data management capabilities, and make full use of data assets to promote the sustainable development of enterprises.
"Dutstack Product White Paper" download address: https://www.dtstack.com/resources/1004?src=szsm
"Data Governance Industry Practice White Paper" download address: https://www.dtstack.com/resources/1001?src=szsm
For those who want to know or consult more about big data products, industry solutions, and customer cases, visit the Kangaroo Cloud official website: https://www.dtstack.com/?src=szkyzg
IntelliJ IDEA 2023.3 & JetBrains Family Bucket annual major version update new concept "defensive programming": make yourself a stable job GitHub.com runs more than 1,200 MySQL hosts, how to seamlessly upgrade to 8.0? Stephen Chow's Web3 team will launch an independent App next month. Will Firefox be eliminated? Visual Studio Code 1.85 released, floating window Yu Chengdong: Huawei will launch disruptive products next year and rewrite the history of the industry. The US CISA recommends abandoning C/C++ to eliminate memory security vulnerabilities. TIOBE December: C# is expected to become the programming language of the year. A paper written by Lei Jun 30 years ago : "Principle and Design of Computer Virus Determination Expert System"