One, Shiro
【1 】What is Shiro?
Shiro is an open source framework under Apache. It extracts the security authentication-related functions of the software system to implement user identity authentication, permission authorization, encryption, session management and other functions, forming a universal security authentication framework.
【2 】Characteristics of Shiro
Shiro is a powerful and flexible open source security framework that handles authentication, authorization, session management, and password encryption very clearly. The following are its characteristics:
- Easy-to-understand Java Security API;
- Simple identity authentication (login), supporting multiple data sources (LDAP, JDBC, etc.);
- Simple signing of roles (access control), and also supports fine-grained authentication;
- Supports first-level caching to improve application performance;
- Built-in POJO-based enterprise session management, suitable for Web and non-Web environments;
- Heterogeneous client session access;
- Very simple encryption API;
- It is not bundled with any framework or container and can run independently.
【3】Shiro core component architecture diagram
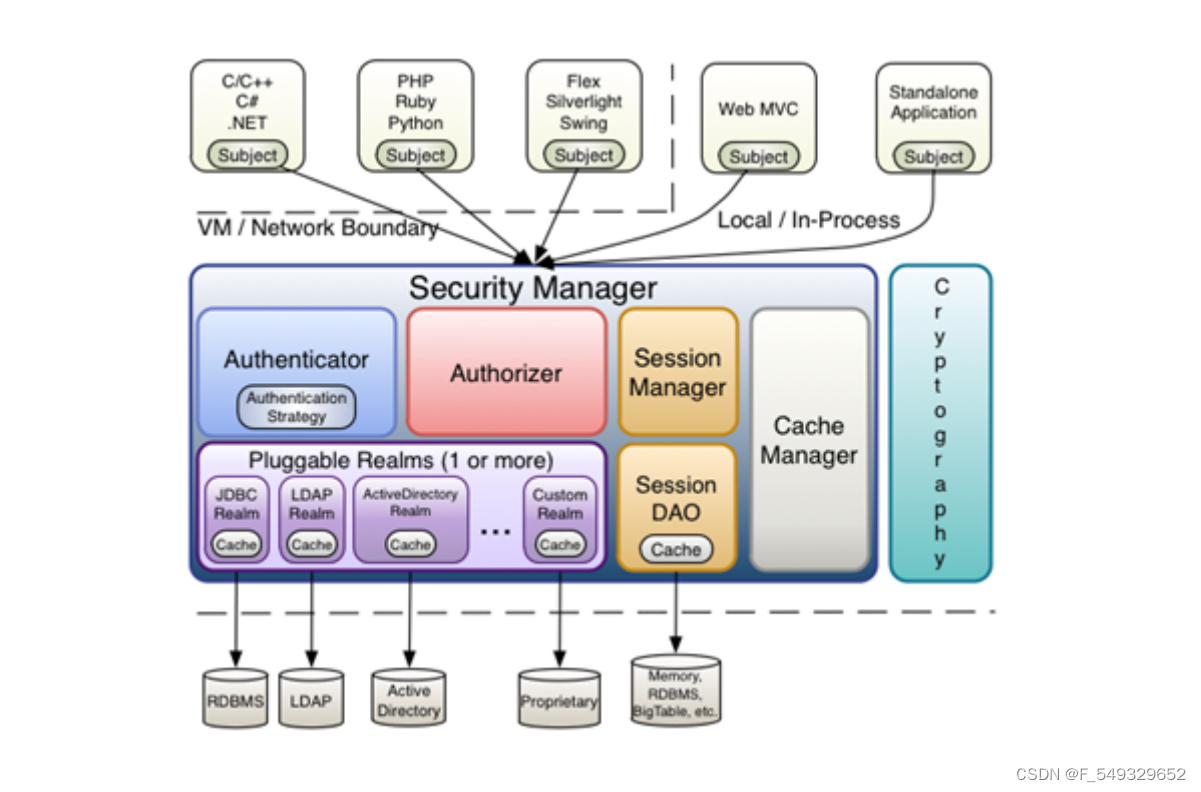
【4】Basic process of Shiro identity authentication
1. Shiro encapsulates user data into identification tokens. Tokens generally encapsulate user names, passwords and other information.2. Use the Subject facade to obtain the identification token that encapsulates the user's data.
SessionManager session management , the shiro framework defines a set of session management, which does not rely on the session of the web container, so shiro can be used in non-web applications, and can also centrally manage the sessions of distributed applications. This feature can make it possible sign in. SessionDAO is a session dao, which is a set of interfaces for session operations. For example: you can store the session in the database through jdbc, or you can store the session in the cache server CacheManager cache management, and store user permission data in the cache, which can improve performance Cryptography password For management, Shiro provides a set of encryption/decryption components to facilitate development. For example, it provides commonly used functions such as hashing, encryption/decryption, etc.
3. The Subject hands the identification token to the SecurityManager. In the SecurityManager security center, the SecurityManager entrusts the identification token to the authenticator Authenticator for identity verification. The role of the authenticator is generally to specify how to authenticate. It specifies which Realms are used for this authentication.4. The authenticator Authenticator compares the incoming identification token with the data source Realm to verify whether the token is legal.
【5】Basic process of Shiro identity authorization
1. First call the Subject.isPermitted/hasRole interface, which will be delegated to SecurityManager .
2. SecurityManager will then delegate to the internal component Authorizer;
3. The Authorizer then delegates its request to our Realm; Realm is the one that really does the work;
4. Realm encapsulates the parameters requested by the user into permission objects. Then get the permission set queried from the database from the doGetAuthorizationInfo method we overridden.
5. Realm compares the permission objects passed in by the user with the permission objects found from the database. If the permission object passed in by the user is among the permission objects found from the database, true is returned, otherwise false is returned.
Prerequisite for authorization operation: the user must be authenticated.
2. Spring Security
Spring Security mainly implements Authentication (authentication, solving who are you?) and Access Control (access control, that is, what are you allowed to do?, also known as Authorization). Spring Security architecturally separates authentication and authorization and provides extension points. It is a lightweight security framework that ensures authentication and authorization support for Spring-based applications. It is well integrated with Spring MVC and comes bundled with popular security algorithm implementations.
Implementation process
- The client initiates a request and enters the Security filter chain.
- When reaching LogoutFilter, determine whether it is the logout path. If it is the logout path, go to logoutHandler. If the logout is successful, go to logoutSuccessHandler for successful logout processing. If the logout fails, it will be handled by ExceptionTranslationFilter; if it is not the logout path, go directly to the next step. a filter.
- When reaching the UsernamePasswordAuthenticationFilter, determine whether it is the login path. If so, enter the filter for login operation. If the login fails, go to the AuthenticationFailureHandler login failure processor for processing. If the login is successful, it will reach the AuthenticationSuccessHandler login success handler for processing. If it is not login, Requests do not enter this filter.
- When reaching the FilterSecurityInterceptor, the uri will be obtained, and the corresponding authentication manager will be found based on the uri. The authentication manager will do the authentication work. If the authentication is successful, it will reach the Controller layer, otherwise it will go to the AccessDeniedHandler authentication failure handler for processing.
Features
What shiro can achieve, Spring Security can basically achieve, relying on the Spring system, but the advantage is that it is the biological son of Spring Family Bucket, which is more suitable for integration, and is slightly more responsible than shiro in terms of use.
3. Comparison between the two
Shiro is easier to use than Spring Security, that is, the implementation is simpler, and basic authorization and authentication Shiro is basically sufficient.
The Spring Security community has higher support. As a son of the Spring community, it has advantages in support and update and maintenance, and it integrates well with the Spring set.
Shiro is powerful yet simple and flexible. The projects under Apache are relatively reliable and are not bound to any framework or container and can run independently.