For most of us, passwords are just the most common method of authentication for countless online services. But to cybercriminals, it's so much more than that—an easy way into someone's life, a vital tool for crime, and a commodity to sell.
For most of us, passwords are just the most common method of authentication for countless online services. But to cybercriminals, it's so much more than that—an easy way into someone's life, a vital tool for crime, and a commodity to sell.
Knowing your password allows crooks not only to gain access to your accounts, data, money, and even your identity; they can also use you as a weak link to attack friends, relatives on your network, or even companies you work for or manage/own. To prevent this, you first need to understand how outsiders can steal your passwords.
How did your passwords fall into the hands of cybercriminals?
There is a common misconception that in order to give your passwords to cyber crooks, you need to make a mistake - download and run an unchecked file from the Internet, open a document from an unknown sender, or open a file on some suspicious website Enter your credentials on . Granted, all of these behavioral patterns can make an attacker's life easier, but there are others. Here are the most common cybercriminal methods for gaining account access.
Phishing
This is indeed one of the credential collection methods that relies primarily on human error. Hundreds of phishing sites appear every day, especially with the help of thousands of emails pointing to them. But if you for some reason think you’ll never fall for a phishing trick – you’re wrong. The method is nearly as old as the internet itself, so cybercriminals have had plenty of time to develop a plethora of social engineering tricks and camouflage tactics. Even professionals sometimes cannot tell the difference between a phishing email and a real email at a glance.
malicious software
Another common way to steal credentials is through the use of malware. According to our statistics, a large percentage of active malware consists of Trojan stealers whose main purpose is to wait for users to log into a site or service, then copy their passwords and send them back to their authors. If you don't use a computer security solution, Trojans can remain hidden on your computer for years without being detected, and you won't know what's wrong because they don't do any visible harm, they just execute silently their work.
Password-stealing Trojans aren't the only malware looking for passwords. Sometimes, cybercriminals inject web browsers on websites and steal anything users enter, including credentials, names, bank card details, and more.
Third party leaks
Becoming a user of some unsecured internet services or a customer of a company that exposes their customer data can also reveal your password. Of course, companies that take cybersecurity seriously won't store your passwords at all, or at least in encrypted form. But you can never be sure if enough security measures are in place. This year, for example, a SuperVPN leak contained the personal details and login credentials of 21 million users.
Additionally, some companies simply can't avoid storing your clear text passwords. Yes, I'm talking about the infamous LastPass password management utility hack. According to new information, an unknown attacker accessed cloud-based storage using some customer data, including backups of customer vaults. Yes, these vaults are properly encrypted, LastPass never stores or even knows the decryption key. But what if a LastPass customer logged into their vault using a password that had been leaked from another source? If they reuse unsecured passwords, now cybercriminals will be able to access all of their accounts at once.
initial access agent
Here we come to another source of stolen passwords – the black market. Modern cybercriminals prefer to specialize in certain areas. They might steal your passwords, but they won't necessarily use them: it's more profitable to sell them wholesale. Purchasing such a password database is particularly attractive to cybercriminals because it gives them an all-in-one function: users tend to use the same passwords across multiple platforms and accounts, often tying them all to the same email. So, with a password from one platform, a cybercriminal can gain access to a victim's many other accounts -- from their gaming accounts to their personal emails and even private accounts on adult websites.
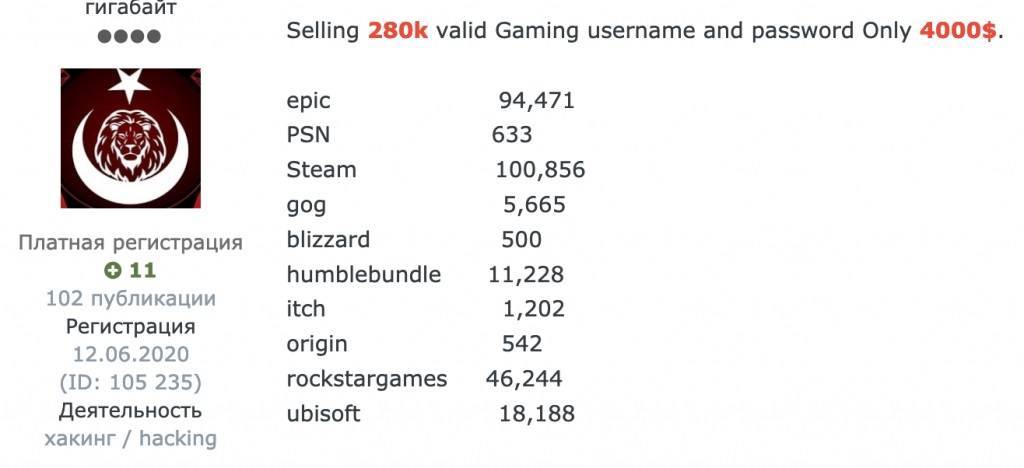
An ad on a hacker forum: Someone is offering 280,000 usernames and passwords for various gaming platforms for $4,000
Leaked company databases, which may or may not contain credentials, are also being sold on the same black market. The price of such databases varies depending on the amount of data and the industry the organization is in: some password databases can cost hundreds of dollars.
Certain services on the dark web aggregate leaked passwords and databases and then enable paid subscriptions or one-time access to their collections. In October 2022, the notorious ransomware group LockBit compromised a healthcare company and stole its user database containing medical information. Not only did they sell subscriptions to this information on the dark web—presumably they purchased the initial access on the same black market.
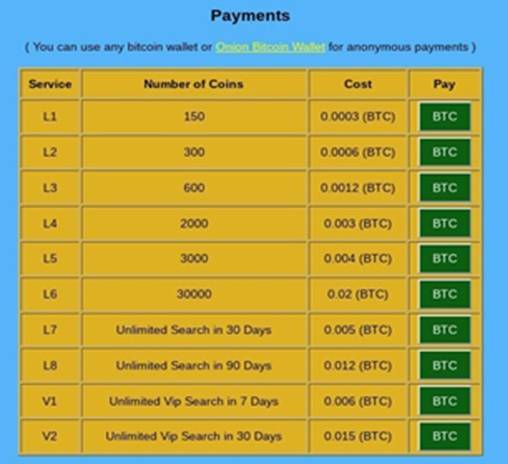
A dark web service that offers paid access to databases containing stolen data
Brute force attack
In some cases, cybercriminals don't even need to steal a database to find your password and break into your account. They can use brute force attacks, in other words, try thousands of typical password variations until one works. Yes, that doesn't sound very reliable. But they don't need to go through all possible combinations - there are certain tools (Wordlist Generators) that can generate a list of possible common passwords based on the victim's personal information (so-called brute-force dictionaries).
These procedures look like a mini-questionnaire about the victim. They ask for personal information about names, surnames, dates of birth, partners, children and even pets. The attacker can even add additional keywords they know about the target, which can be added to the mix. Using this combination of related words, names, dates, and other data, password dictionary generators create thousands of password variations that attackers try later on when logging in.
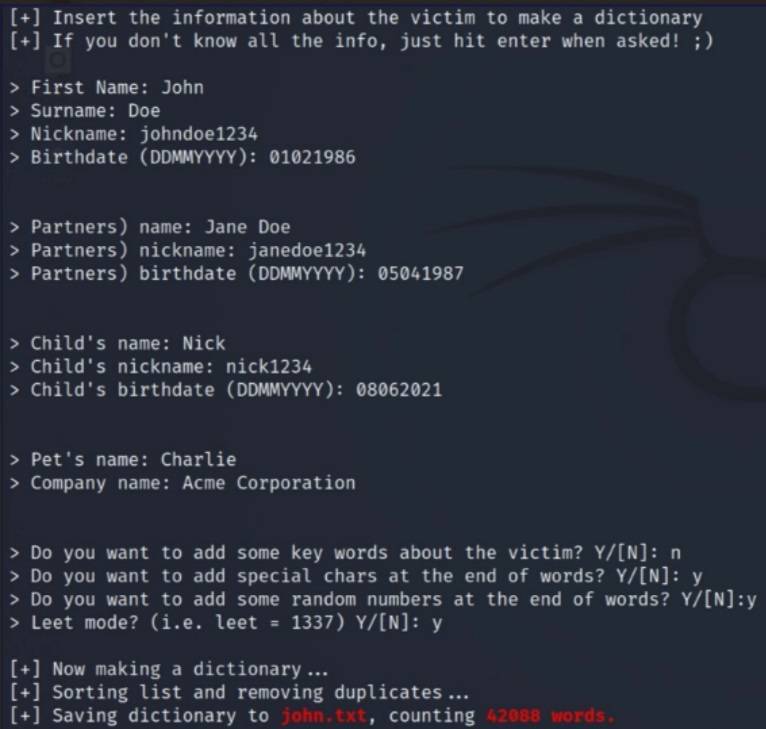
A dictionary can be generated for a brute force attack based on known information about the intended victim.
To use this method, cybercriminals first need to conduct research—which is where those leaked databases might come in handy. They may contain information such as date of birth, address or answers to "secret questions." Another source of data is oversharing in social networks. Something that seems absolutely trivial, like a photo from December 6th that says "Today is my beloved puppy's birthday."
Possible consequences of compromised or brute-forced passwords
There are some obvious consequences: cybercriminals can take over your account and hold it for ransom, use it to trick your contacts and online friends, or, if they are able to get your password to your banking website or app, It is possible to empty your account. However, sometimes their intentions are not so direct.
For example, as more and more games introduce in-game currency, more and more users are linking their payment methods to their accounts. This makes gamers a target for hackers. By gaining access to game accounts, they can steal in-game valuables such as skins, rare items, or internal game currency, or misuse victims' credit card data.
Leaked databases and information that can be obtained when searching for your account can be used not only for financial gain, but also for reputational damage and other types of societal harm. If you're a celebrity, you could be blackmailed and face a choice: give away personal information (which could affect your reputation) or lose money.
Even if you're not a celebrity, you can become a victim—the act of revealing someone's identifying information online—such as their real name, home address, workplace, phone, financial, and other personal information. Such attacks range from relatively innocuous attacks, such as signing up to countless mailing lists or bogus takeout orders in your name, to more dangerous attacks, such as various forms of cyber fraud, identity theft, and even face-to-face stalking .
Finally, if you use the same password for your personal and work accounts, cybercriminals can take over your business email and use it for commercial email compromise schemes or even targeted attacks.
How to protect your account from unwanted access
First - always keep in mind the principles of password usage:
- Don’t reuse the same password for multiple accounts;
- Make your passwords long and complex;
- Store passwords securely;
- Change your password immediately the first time you hear news about a data breach on a service or website protected by this password.
Major password manager software can help you with all these tasks and monitor the security of all your passwords in real time. Some password managers even offer services to check if a leak actually happened. Commonly known as a data leak checker, this feature lets you check whether your email has been found in a stolen database somewhere. If it has been compromised, you will receive a list of the compromised sites, the type of data exposed (personal, banking, online activity history, etc.), and advice on what to do about it.
Here are some additional suggestions:
- Enable two-factor authentication whenever possible. It provides an extra layer of security that prevents hackers from accessing your account - even if someone manages to get your login and password.
- Set up your social networks for better privacy. This will make it more difficult to find information about you, making it more complicated to use a brute force dictionary to attack your account.
- Stop oversharing personal information, even if only friends can see it. Today's friend may become tomorrow's enemy.