Let me start with the conclusion: basically impossible
principle
The groupId field in the Maven package is the reverse of the domain name. For example, if you have a 12345.com, you can apply for the groupId of com.12345.
Many open source projects have stopped maintenance, but many people use them, and these teams may forget to renew the domain name; at the same time, Maven search engines all use groupId + artifactId (arbitrary customization) to determine the uniqueness of the project, and the preempted content will be compared with the previous normal content The code is displayed as a project, making people mistakenly think that the new version has been updated, but in fact it is just adding malicious code.
It is estimated that normal carbon-based organisms will definitely not verify whether each version is officially released, mainly there is no way to verify...
we need to do
Find an open source project and preempt its domain name. Then apply for groupId, and then upload a version of the code, which is slightly different from the previous one.
If we can successfully implement it, we have succeeded; if we can't, we have failed.
Find Expired Domain Names
Our thinking is that domain names that are cheap to register and expensive to renew are more likely to expire. So consider a cheap domain name, here is an example of top, the registration price is about 9 yuan/first year, and the renewal fee is 26 yuan/year
Official fuzzy query interface:
https://search.maven.org/solrsearch/select?q=top.&rows=20&wt=jsonWanwang domain name query whether registered interface:
https://panda.www.net.cn/cgi-bin/check.cgi?area_domain=xxxx.comLet's write a script to automatically query, I'm getting older...
I found one soon (there are less than 30 out of which 2 can be registered, the probability is too high)
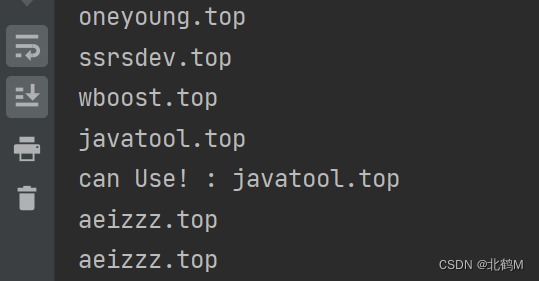
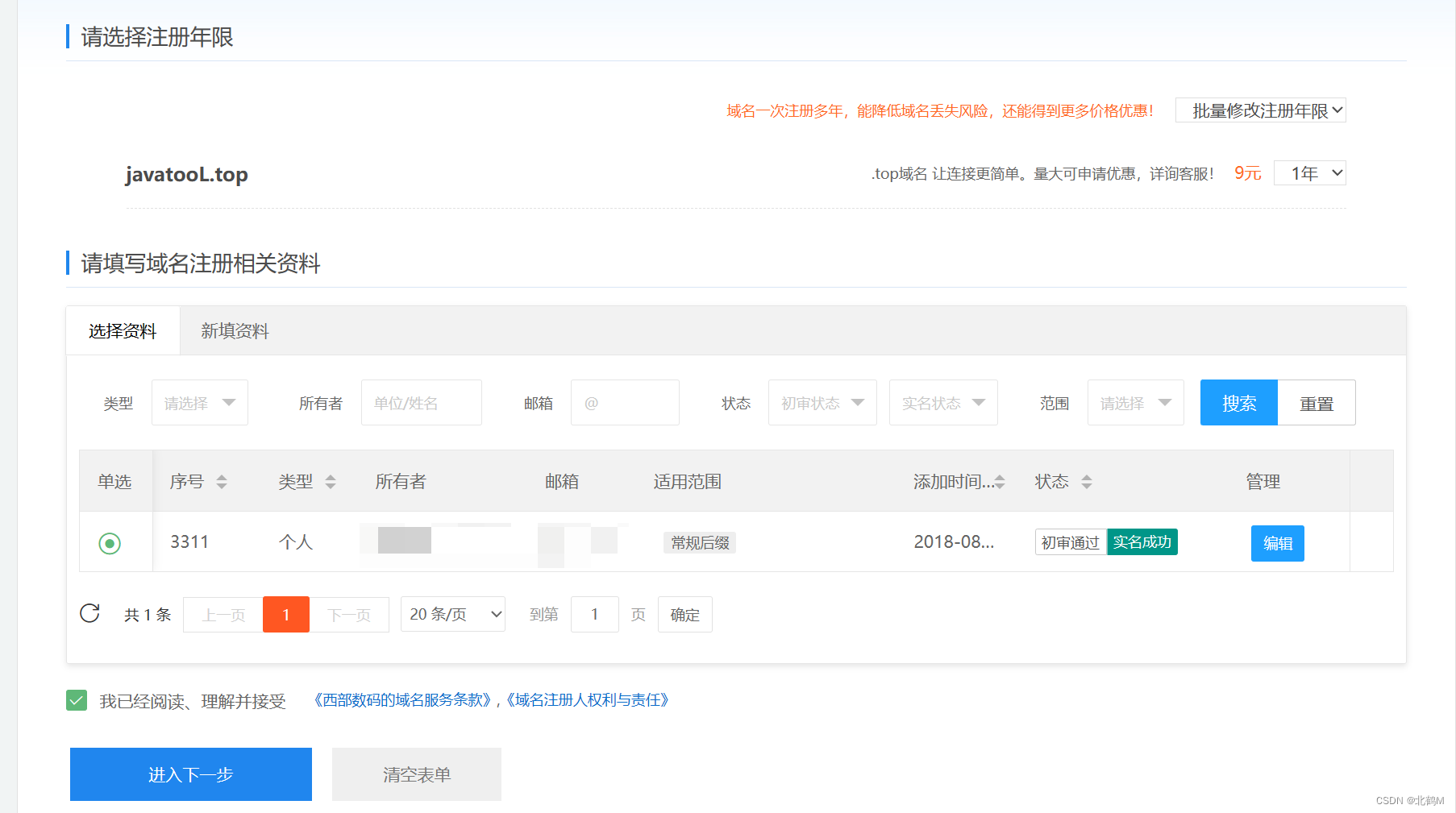
Register him for a year:
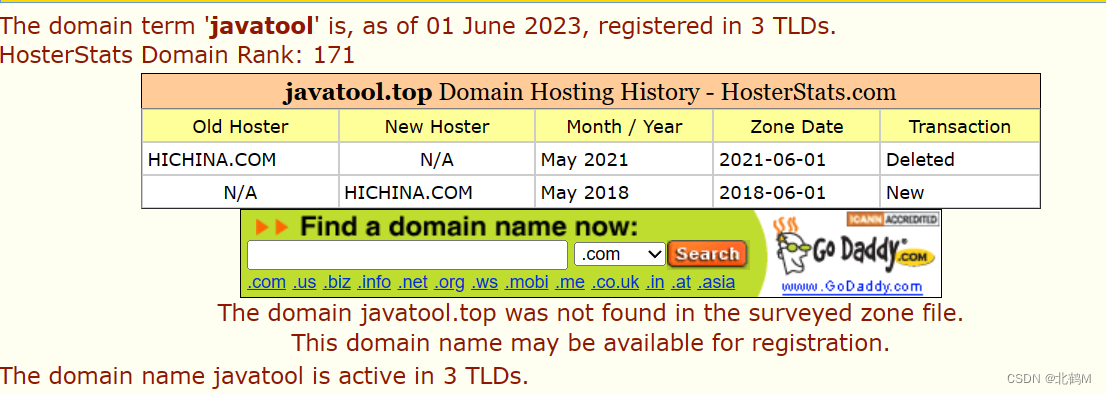
Through the query, we can see that this domain name has been registered twice before, and both of them have expired.
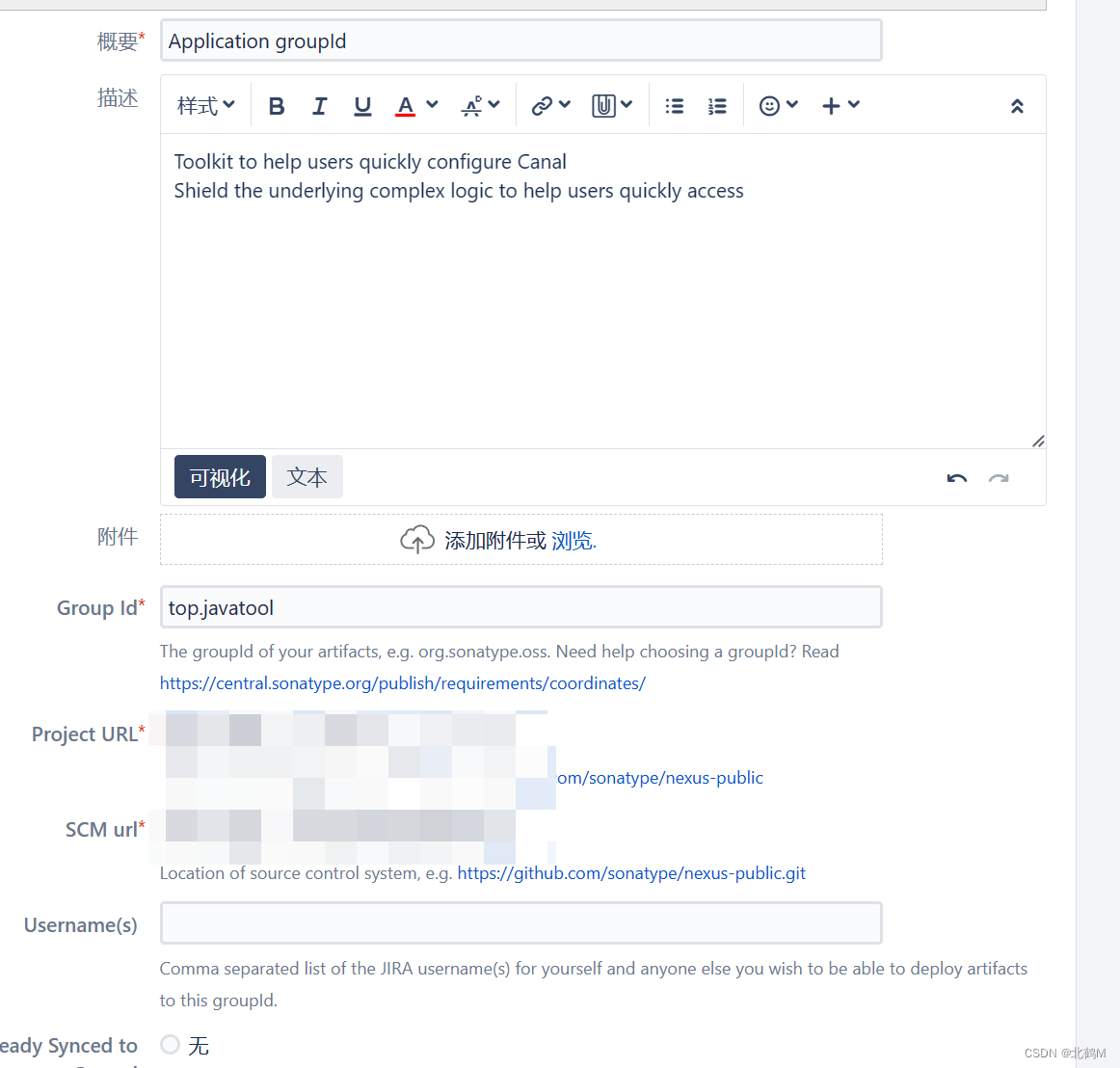
It just so happens that the repository under this name has codes for reference, so apply for groupId directly
Embarrassing after that:
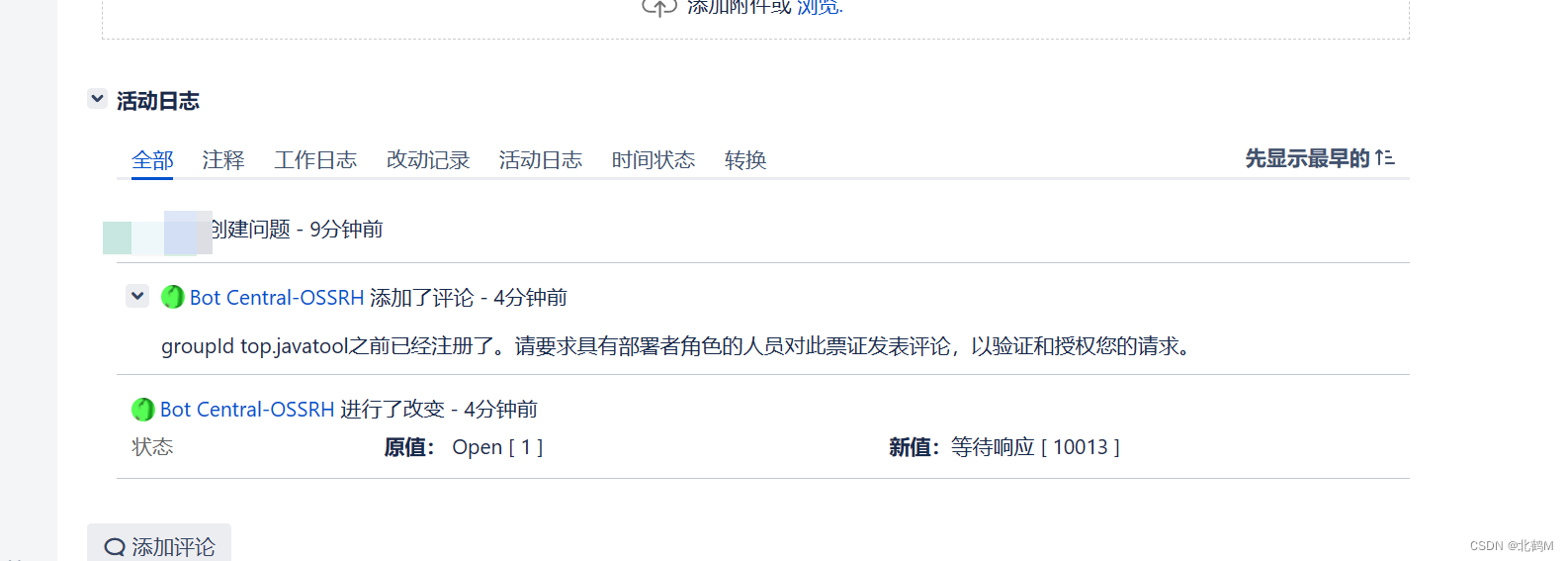
There will be requirements for the original role deployment person to comment under this jira
get comment
Obviously, it's stuck at the moment, because we can't find the original author at all, only know the original author's Github address
Instead, you can know the user's mailbox according to Github (most people will display it on their homepage)
In fact, there must be a situation where the user's email address and password exist at the same time in the social work database, but at this time it may be more luck
Since this is not our own test account, we will not conduct follow-up inquiries in line with the principle of user privacy
similar case
Quoted from an article by Tencent Security Response Center (TSRC):
Typical cases of dependent package squatting include:
In 2017, a variety of Python/Nodejs library packages were exposed to contain malicious code, mainly using name similarity to mislead users to install, and tens of thousands of hosts were affected by misinstallation.
In 2020, foreign security researchers discovered that the internal private package names of many well-known international companies were leaked on GitHub and Web pages, and then registered and uploaded packages with the same name on PyPI/NPM/RubyGems. Finally, the internal servers of these companies were forced to install malicious packages and were affected. .
postscript
In fact, foreign netizens have discussed it before, and no one in China seems to write similar things: https://news.ycombinator.com/item?id=26087489