Original: http://blog.csdn.net/gsnumen/article/details/7293266
ssh detailed login process
First, let’s talk about the related concepts:
Plaintext: A message that needs to be sent secretly.
Ciphertext: The message in which the plaintext has been ciphered.
Encryption: The transformation from plaintext to ciphertext.
Decryption: The process of recovering plaintext from ciphertext.
Cracking: The process by which an illegal receiver attempts to analyze the plaintext from the ciphertext.
Encryption Algorithm: A set of rules used to encrypt plaintext.
Decryption Algorithm: A set of rules used to decrypt ciphertext.
Key: A set of cryptographic information used when encrypting and decrypting.
Symmetric encryption: It is an encryption method that uses a single-key cryptosystem, and uses the same key to encrypt and decrypt information.
Asymmetric encryption: Two keys are required: a public key and a private key, which appear in pairs. The data encrypted by the public key can be decrypted only by the private key, and the data encrypted by the private key can be decrypted only by the public key. "Symmetric encryption", "asymmetric encryption" encryption method uses different keys for encryption and decryption, so it is called "asymmetric encryption" encryption method.
The difference between symmetric encryption and asymmetric encryption is whether the same key is used for encryption and decryption.
Encryption, identity authentication, digital signature authentication:
Encryption: Encrypt data data, so that even if illegal users obtain the encrypted data, they cannot obtain the correct data content, so data encryption can prevent data from monitoring attacks; the focus is on data security.
Identity authentication: Judging the authenticity of an identity, after confirming the identity, the system can grant different permissions according to different identities; the focus is on the authenticity of the user.
Digital signature authentication: First of all, "digital signature" is some data attached to the data unit, or the cryptographic transformation of the data unit. This kind of data or transformation allows the receiver to determine the origin of the data and the integrity of the data, preventing forgery and tampering. Digital signature authentication focuses on ensuring the integrity of data and preventing forgery and tampering.
Authentication principle:
There are 2 authentication methods:
Authentication method based on account and password and authentication method based on public key and private key
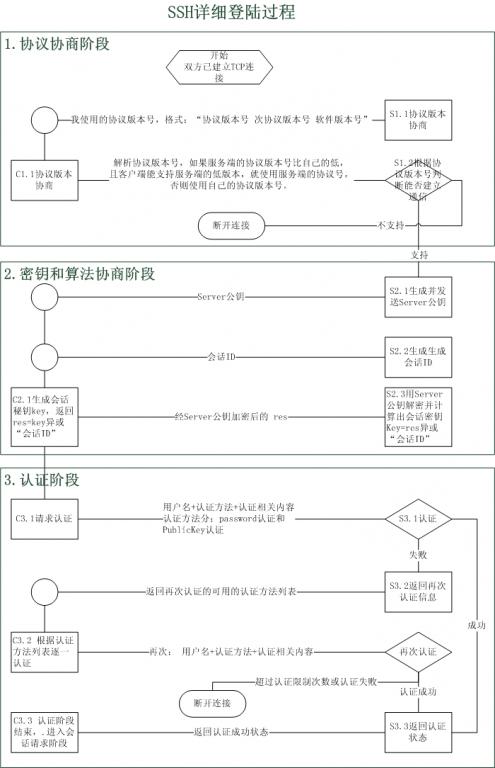
The ssh login process is divided into 5 stages
1. Version number negotiation stage
2. Key and algorithm negotiation stage
3. Certification stage
4. Session request stage
5. Conversational interaction stage
1. Version number negotiation stage
The server opens port 22 and waits for the client to connect.
The client initiates a TCP connection to the server. After the connection is established, the server sends the first message to the client, including the version flag string, in the format of "protocol version number minor protocol version number software version number".
After the client receives the message, it parses the protocol version number. If the server's protocol version number is lower than its own, and the client can support the server's lower version, it uses the server's protocol number, otherwise it uses its own protocol version number.
The client replies to the server with a packet containing the protocol version number the client decides to use.
The server compares the version number sent by the client to determine whether it can interact with the client.
If the negotiation is successful, enter the key and algorithm negotiation phase. Otherwise, the server disconnects the TCP connection.
2. Key and algorithm negotiation stage
The server and the client respectively send algorithm negotiation packets to each other, and the packets include the public key algorithm list, encryption algorithm list, message verification code algorithm list, and compression algorithm list that they support.
The server and the client obtain the final algorithm based on the algorithms supported by each other and themselves.
The server and client use the DH exchange algorithm, host key pairing and other parameters to generate the session key and session ID.
c public client public key
c encrypted client key
s public server public key
s-secret server key
After the version number negotiation phase is complete:
The server sends s to the client.
The server generates a session ID, sets it as id, and sends it to the client.
The client generates a session key, sets it as key, and computes the res = id XOR key.
The client encrypts res with s and sends the result to the server.
The server decrypts the s secret to get res.
The server calculates the res XOR id and gets the key.
At this point, both the server and the client know the session key and session ID, and subsequent data transmissions use the session key for encryption and decryption.
3. Certification stage
Authentication method based on account and password:
The client encrypts the account number, authentication method, and password using the session key generated during the key and algorithm negotiation phase, and sends the result to the server.
The server uses the obtained session key to decrypt the message to obtain the account and password.
The server judges the account and password. If it fails, it sends an authentication failure message to the client, which contains a list of methods that can be authenticated again.
The client selects a method from the list of authentication methods to authenticate again.
This process is repeated until the authentication succeeds or the number of authentication times reaches the upper limit, and the server closes the current TCP connection.
Authentication method based on public key and private key:
Use the ssh-keygen program to generate the public key id_dsa.pub and the private key id_dsa, which are generally generated on the client, and then send the id_dsa.pub to the server in some way.
The server is placed under the .ssh directory of the directory of the account that will be logged in remotely.
The client encrypts the account number, authentication method, and id_dsa.pub using the session key generated during the key and algorithm negotiation phase, and sends the result to the server.
The server uses the session key to decrypt the message to obtain the account number and id_dsa.pub. The server looks for the corresponding public key in the .ssh directory of the account's directory. If it is not found, it sends a failure message to the client. If it is found, it compares the public key sent by the client with the found public key. If the contents are the same, The server generates a random string, called "challenge" for short, then encrypts the challenge with the public key it found, and then encrypts it again with the session key.
The server sends this double encrypted data to the client.
The client decrypts the message with the session key, and then decrypts the data again with id_dsa to get the challenge.
The client encrypts the challenge with the session key and sends it to the server.
The server uses the session key to decrypt the message, gets the challenge, and judges whether it is the challenge generated by itself. If it is not the same, it sends a failure message to the client. If it is the same, the authentication passes.
refer to:
------------- end -------------
From: GS
-------------------------------
From: GS
-------------------------------