1. Experimental content
1. Practice command history, aliases, and special character usage in the shell (Chapter 4, Section 4.2 ~ Section 4.5)
2. Shell command application exercise (see the experimental steps for details)
3. Write a shell script and execute it in 4 ways (see the experimental steps for details)
4. Combined with the personal learning progress bar, choose new attempts and new explorations in the linux environment
2. Experimental steps
1. Practice command history, aliases, and special character usage in shell.
2. Shell command application practice
(1) View the help information and briefly describe the purpose of the following files
① /etc/passwd (hint: view the description of this file through man 5 passwd)
② /etc/shadow (hint: view the description of this file through man 5 shadow)
③ /etc/group (hint: view the description of this file through man 5 group)
④ /etc/gshadow (hint: check the description of this file through man 5 gshadow)
1) /etc/passwd file description
A row of records in /etc/passwd corresponds to a user, and each row of records is separated into 7 fields by colons (:). The format and specific meaning are as follows:
Username : Password : User ID : Group ID : Commentary Description : home directory : login shell
Username (login_name): is a string representing the user account.
Password (passwd): In some systems, the encrypted user password is stored.
User Identification Number (UID): is an integer that is used internally by the system to identify users.
Group Identification Number (GID): The field records the user group to which the user belongs. It corresponds to a record in the /etc/group file.
Annotative description (users): The field records some personal information of the user, such as the user's real name, phone number, address, etc.
Home directory (home_directory): that is, the user's starting working directory, which is the directory where the user is located after logging in to the system.
Login Shell (Shell): After the user logs in, a process is started, which is responsible for passing the user's operation to the kernel. This process is the command interpreter or a specific program that runs after the user logs in to the system, that is, the Shell.
2) /etc/shadow file description
The format of the /etc/shadow file is similar to that of the /etc/passwd file. It also consists of several fields, and the fields are separated by ":".
The main meanings of the fields in the file are:
Login Name: Encrypted Password: Last Modified Time: Min Interval: Max Interval: Warning Time: Inactivity Time: Expiration Time: Flag
"login name" is the user account that matches the login name in the /etc/passwd file
The "password" field stores the encrypted user password:
"Last Modified Time" represents the number of days from a certain moment to when the user last modified the password. The starting point of time may be different for different systems.
"Minimum time interval" refers to the minimum number of days required between password changes.
"Maximum Interval" refers to the maximum number of days a password will remain valid.
The "Warning Time" field indicates the number of days between when the system starts warning the user and when the user's password officially expires.
"Inactivity time" represents the maximum number of days that a user has no sign-in activity but the account can remain active.
The "Expiration Time" field gives an absolute number of days. If this field is used, it gives the lifetime of the corresponding account. After the expiration, the account is no longer a legitimate account, and can no longer be used to log in.
3)/etc/group
The /etc/group file and the /etc/passwd and /etc/shadow files are all files related to the system administrator's management of users and user groups. The linux /etc/group file is a file about the system administrator's management of users and user groups. All the information of linux user groups is stored in the /etc/group file. A collection of users with certain common characteristics is a group of users. User group (Group) configuration files mainly include /etc/group and /etc/gshadow, where /etc/gshadow is the encrypted information file of /etc/group.
All information about user groups is stored in the /etc/group file. The format of this file is that several fields are separated by colons (:) as follows:
Group name: Password: Group ID: List of users in the group
group name:
The group name is the name of the user group, consisting of letters or numbers. As with login names in /etc/passwd, group names should not be repeated.
Password:
The password field stores the encrypted password of the user group. Generally, the user groups of Linux systems do not have passwords, that is, this field is generally empty or *.
Group ID:
The group ID is similar to the user ID, it is also an integer and is used internally by the system to identify the group. Also known as GID.
List of users in the group:
is a list of all users belonging to this group, separated by commas (,). This user group may be the user's primary group, or it may be an additional group.
4)/etc/gshadow
/etc/gshadow
/etc/gshadow is the encrypted information file of /etc/group, such as user group (Group) management password is stored in this file.
/etc/gshadow and /etc/group are two complementary files; for large servers, for many users and groups, it is extremely necessary to customize some permission models with complex relational structures and to set user group passwords.
Group Name: Password: Group Manager: List
of users in the group 1) Group Name: It is the name of the user group, consisting of letters or numbers.
2) Password: User group password, this field can be empty or !, if it is empty or !, it means no password
3) Group Manager: This field can also be empty, if there are multiple user group managers,
4) User list in the group: if there are multiple members, use , to separate ;
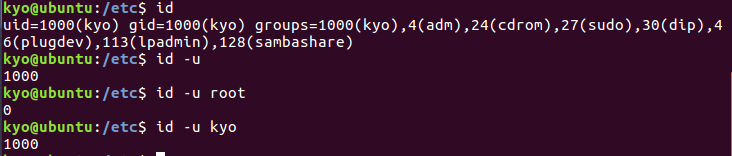
(2) Enter the following commands in sequence to observe the running results. Combined with the help information viewed by man id, point out the function of each command
① id Displays the current user id
② id -u display user id
③ id -u root shows the id of root
④ id -u kyo Display the id of user kyo
(3)在 shell 命令终端依次输入以下命令,观察执行结果,理解每条命令实现的具体功
能
① which python
whereis python
locate python
find /usr/bin -name python (说明: which, whereis, locate, find 都具有检索的功能,结合执行结果,查找帮 助信息,总结其区别)
which 查看可执行文件的位置
which是通过 PATH环境变量到该路径内查找可执行文件,所以基本的功能是寻找可执行文件
whereis 查看文件的位置
和find相比,whereis查找的速度非常快,这是因为linux系统会将 系统内的所有文件都记录在一个数据库文件中。当使用whereis和下面即将介绍的locate时,会从数据库中查找数据,而不是像find命令那样,通 过遍历硬盘来查找,效率自然会很高。
但是该数据库文件并不是实时更新,默认情况下时一星期更新一次,因此,我们在用whereis和locate 查找文件时,有时会找到已经被删除的数据,或者刚刚建立文件,却无法查找到,原因就是因为数据库文件没有被更新。
locate 配 合数据库查看文件位置
find 实际搜寻硬盘查询文件名称
find是在硬盘上遍历查 找,因此非常消耗硬盘的资源,而且效率也非常低
② grep -n -E 'root|kyo|^user*' /etc/passwd (提示:扩展正则表达式)
grep -n -E ' [[:digit:]] ' /etc/passwd
grep -n -E ' [[:alpha:]] ' /etc/passwd
grep -n '[0-9]\{4,\}' /etc/group (提示: 在用户组文件中查找 GID 是 4 位数 及以上的组信息记录)
grep 默认仅支持基础正则表达式,如果要使用扩展性正则表达式,可以使用 grep - E。grep -E 与 egrep 相当于命令别名关系。
[:digit:] 匹配任意一个数字字符
[:alpha:] 匹配任意一个字母字符(包括大小写字母)
(4)根据要求写出相应的 shell 命令
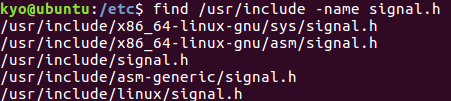
① 在目录/usr/include 下搜索文件 signal.h 是否存在 (提示: find 命令)
使用 find /udr/include -name signal.h
② 在/usr/include 目录下的所有文件中查找包含 BUFSIZ 的行,并显示所在行号。 要求:屏幕上只显示查找到的结果,过滤错误信息。 (提示: ① 利用 grep 和通配符*; ②利用错误信息重定向和特殊设备文件/dev/null)
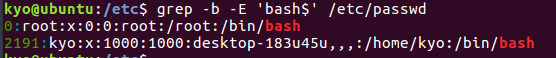
③ 在用户名密码文件/etc/passwd 中查找登录 shell 为 bash 的用户信息记录,并显 示行号(提示:使用 grep 和正则表达式中的$)
④ 从/etc/group 文件中截取第 1 列(组名)和第 3 列(组 id),并按照组 id 号的数 值大小由小到大排序。(提示:综合使用 cut, 管道线及 sort 命令)
3. 编写一个 shell 脚本,使用 4 种方式(参见第 4 章教材/课件)分别执行。
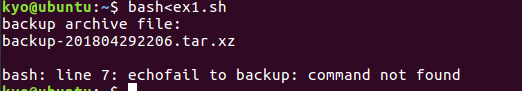

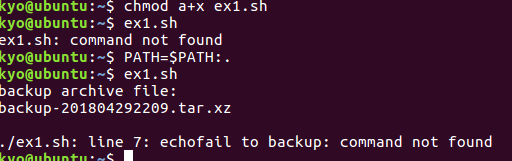
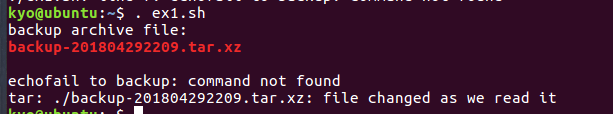
(2)练习 2 第 1 步,使用 vi/vim/gedit 或其它编辑器,编写 shell 脚本 ex2.sh,内容如下:
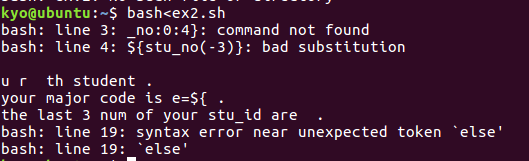
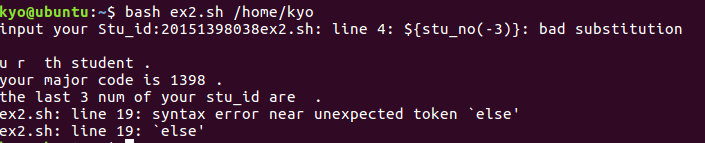
总结与体会
这次实验非常难受,我的虚拟机上的ubuntu不知道为什么很多实验中的命令都无法执行,很多东西也无法安装如gimp,就没进行那部分实验。等有时间会解决一下这个问题。shell总体感觉十分有趣,也非常强大,在考完研之后会好好琢磨琢磨。