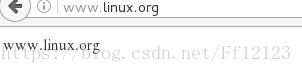
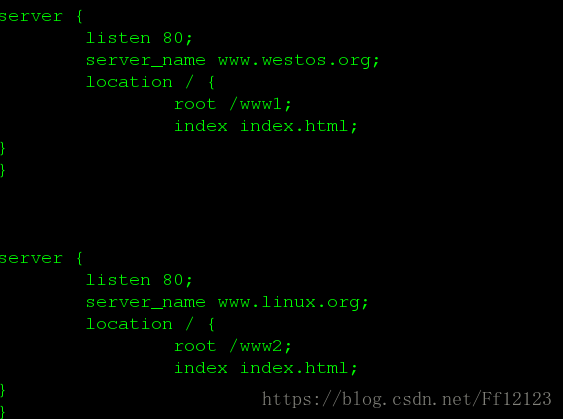
打开配置文件
增加nginx的虚拟主机 如下图所时:
这里要注意的是 末尾的分号不要忘记了
并建立相应的目录以及文件
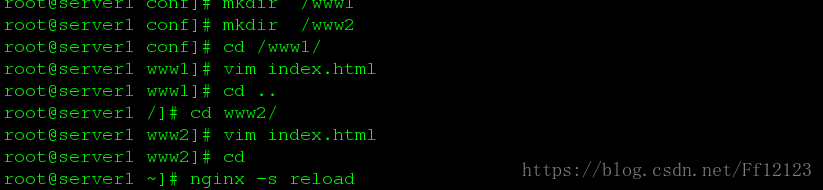
刷新过后 做好本地解析 测试 如下图
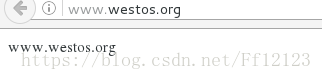
https
因为在编译源码包的时候已经增加了这部分内容,只需将他打开就可以了,写入我们的服务名称,证书,密钥,以及默认目录等
server {
listen 443 ssl;
server_name www.westos.org;
ssl_certificate cert.pem;
ssl_certificate_key cert.pem;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
root /www1;
index index.html index.htm;
}
}
[root@server1 conf] nginx -t #这里报错显示没有相应的证书密钥
nginx: [emerg] BIO_new_file("/usr/local/lnmp/nginx//conf/cert.pem") failed (SSL: error:02001002:system library:fopen:No such file or directory:fopen('/usr/local/lnmp/nginx//conf/cert.pem','r') error:2006D080:BIO routines:BIO_new_file:no such file)
nginx: configuration file /usr/local/lnmp/nginx//conf/nginx.conf test failed
[root@server1 conf] cd /etc/pk
pkcs11/ pki/
[root@server1 conf] cd /etc/pk
pkcs11/ pki/
[root@server1 conf] cd /etc/pki/
[root@server1 pki] cd tls/
[root@server1 tls] cd certs/ #进入当前目录 进行生成
[root@server1 certs] ls
ca-bundle.crt ca-bundle.trust.crt make-dummy-cert Makefile renew-dummy-cert
[root@server1 certs] make cert.pem 生成该文件
umask 77 ; \
PEM1=`/bin/mktemp /tmp/openssl.XXXXXX` ; \
PEM2=`/bin/mktemp /tmp/openssl.XXXXXX` ; \
/usr/bin/openssl req -utf8 -newkey rsa:2048 -keyout $PEM1 -nodes -x509 -days 365 -out $PEM2 -set_serial 0 ; \
cat $PEM1 > cert.pem ; \
echo "" >> cert.pem ; \
cat $PEM2 >> cert.pem ; \
rm -f $PEM1 $PEM2
Generating a 2048 bit RSA private key
....................+++
.................+++
writing new private key to '/tmp/openssl.L3RGRK'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:shaanxi
Locality Name (eg, city) [Default City]:xi'an
Organization Name (eg, company) [Default Company Ltd]:westos
Organizational Unit Name (eg, section) []:linux
Common Name (eg, your name or your server's hostname) []:server1
Email Address []:root@localhost
[root@server1 certs] cp cert.pem /usr/local/lnmp/nginx/conf/ 将它复制到配置文件所在目录里面
[root@server1 certs] nginx -t
nginx: the configuration file /usr/local/lnmp/nginx//conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/lnmp/nginx//conf/nginx.conf test is successful
[root@server1 certs] nginx -s reload
下面为结果:
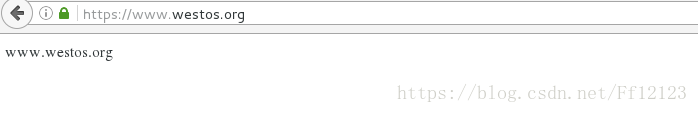
网页的重定向
server {
listen 80;
server_name www.westos.org westos.org;
rewrite ^(.*)$ https://www.westos.org$1 permanent; #当访问这两个域名时,会重新定向为https://www.westos.org而$1表示后面所跟的文件名不变 否则的话都会重新定向为主页
location / {
root /www1;
index index.html;
}
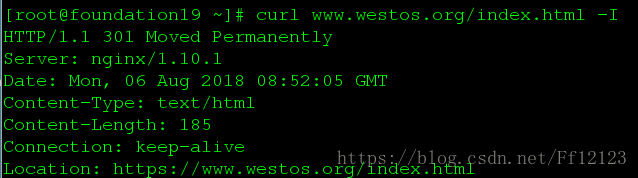
当访问我这台主机时,重新定向到www.westos.org里面
server {
listen 80;
server_name bbs.westos.org;
rewrite ^(.*)$ http://www.westos.org$1 permanent;
location / {
root /www2;
index index.html;
}
}
也可以用以台虚拟主机实现
加入一条判断语句
server {
listen 80;
server_name www.westos.org westos.org bbs.westos.org;
# rewrite ^(.*)$ https://www.westos.org$1 permanent;
if ($host = "bbs.westos.org"){ 当从这个域进来之后 进行判断来决定是否重定向
rewrite ^(.*)$ https://www.westos.org$1 permanent;
}
location / {
root /www1;
index index.html;
}
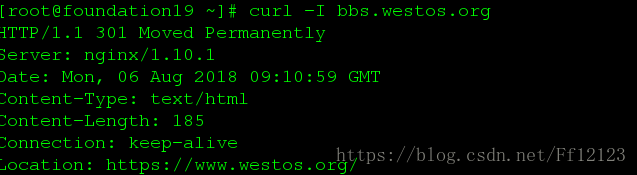
如图当访问bbs.westos.org 时

会自动调转至https://www.westos.org

nginx 的限制
limit_conn_zone $binary_remote_addr zone=addr:10m; 定义这个域的大小为10M
limit_req_zone $binary_remote_addr zone=one:10m rate=1r/s; 处理速度为1妙1个
server {
listen 80;
server_name localhost;
#charset koi8-r;
#access_log logs/host.access.log main;
location / {
# root /usr/local/tomcat/webapps/ROOT;
root html;
index index.php index.html index.htm;
}
location /download/ {
limit_conn addr 1; 最大连接数为1
limit_rate 50k;限制下载速度为50kb
limit_req zone=one burst=5;
下载速度为50k
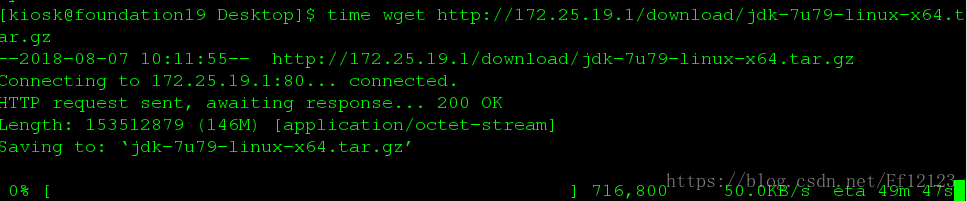
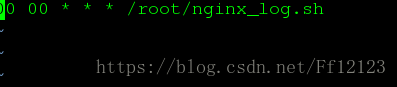
自动考配日志
[root@server1 ~]# vim nginx_log.sh
>#!/bin/bash
cd /usr/local/lnmp/nginx/logs && mv access.log access.log_$(date +%F -d -1day)
nginx -s reload
[root@server1 ~]# chmod +x nginx_log.sh
[root@server1 ~]# crontab -e
防止盗链
在server2端写入:
当访问它时,它会盗用server1的图片链接
下面是防止方法
在server1端配置 在nginx的配置文件里
server {
listen 80;
server_name www.westos.org westos.org; 当访问这个域名是会进入这台虚拟主机
location / {
root /www1;
index index.html;
}
location ~ \.(gif|jpg|phg)$ {
valid_referers www.westos.org;
if ($invalid_referer) {
rewrite ^/ http://bbs.westos.org/daolian.jpg permanent; 当其想要读取/www1的图片时进行重定向到/www2
}
}
server {
listen 80;
server_name bbs.westos.org;
# rewrite ^(.*)$ http://www.westos.org$1 permanent;
location / {
root /www2;
index index.html;
测试结果如下图
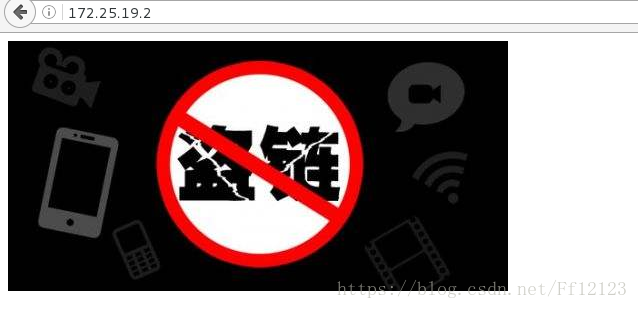
正常不加防盗链检测结果如下图:

或是直接return403 也可以