目录
服务熔断功能
实现方式
- 调用方的熔断保护
- 调用方手动指定远程服务的降级策略。远程服务被降级处理,触发我们的熔断回调方法。注意:是给远程服务指定降级策略
- 超大流量的时候,必须牺牲一些远程服务,在服务的提供方(远程服务)指定降级策略,提供方是在运行,但是不运行自己的业务逻辑,返回的是默认的降级数据(限流的数据)
sentinel整合ribbon+openFeign+fallback
Ribbon系列
启动nacos,sentinel。
准备工作
新建提供者模块:cloudalibaba-provider-payment9003
pom:
<dependencies>
<!--SpringCloud ailibaba nacos -->
<dependency>
<groupId>com.alibaba.cloud</groupId>
<artifactId>spring-cloud-starter-alibaba-nacos-discovery</artifactId>
</dependency>
<dependency>
<groupId>com.lzh.springcloud</groupId>
<artifactId>cloud-api-commons</artifactId>
<version>1.0-SNAPSHOT</version>
</dependency>
<!-- SpringBoot整合Web组件 -->
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-actuator</artifactId>
</dependency>
<!--日常通用jar包配置-->
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-devtools</artifactId>
<scope>runtime</scope>
<optional>true</optional>
</dependency>
<dependency>
<groupId>org.projectlombok</groupId>
<artifactId>lombok</artifactId>
<optional>true</optional>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
</dependencies>
配置文件:
server:
port: 9003
spring:
application:
name: nacos-payment-provider
cloud:
nacos:
discovery:
server-addr: localhost:8848 #配置Nacos地址
#暴露监控端口
management:
endpoints:
web:
exposure:
include: '*'
启动类:
@SpringBootApplication
@EnableDiscoveryClient
public class PaymentMain9003
{
public static void main(String[] args) {
SpringApplication.run(PaymentMain9003.class, args);
}
}
业务类:
@RestController
public class PaymentController
{
@Value("${server.port}")
private String serverPort;
public static HashMap<Long, Payment> hashMap = new HashMap<>();
static{
hashMap.put(1L,new Payment(1L,"28a8c1e3bc2742d8848569891fb42181"));
hashMap.put(2L,new Payment(2L,"bba8c1e3bc2742d8848569891ac32182"));
hashMap.put(3L,new Payment(3L,"6ua8c1e3bc2742d8848569891xt92183"));
}
@GetMapping(value = "/paymentSQL/{id}")
public CommonResult<Payment> paymentSQL(@PathVariable("id") Long id){
Payment payment = hashMap.get(id);
CommonResult<Payment> result = new CommonResult(200,"from mysql,serverPort: "+serverPort,payment);
return result;
}
}
测试:
http://localhost:9003/paymentSQL/1
在新建一个cloudalibaba-provider-payment9004,同上改改端口之类的就行。
新建一个消费者模块:cloudalibaba-consumer-nacos-order84
pom:
<dependencies>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-openfeign</artifactId>
</dependency>
<dependency>
<groupId>com.alibaba.cloud</groupId>
<artifactId>spring-cloud-starter-alibaba-nacos-discovery</artifactId>
</dependency>
<dependency>
<groupId>com.alibaba.cloud</groupId>
<artifactId>spring-cloud-starter-alibaba-sentinel</artifactId>
</dependency>
<dependency>
<groupId>com.lzh.springcloud</groupId>
<artifactId>cloud-api-commons</artifactId>
<version>1.0-SNAPSHOT</version>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-actuator</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-devtools</artifactId>
<scope>runtime</scope>
<optional>true</optional>
</dependency>
<dependency>
<groupId>org.projectlombok</groupId>
<artifactId>lombok</artifactId>
<optional>true</optional>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
</dependencies>
配置文件:
server:
port: 84
spring:
application:
name: nacos-order-consumer
cloud:
nacos:
discovery:
server-addr: localhost:8848 #nacos注册中心地址
sentinel:
transport:
dashboard: localhost:8082 #sentinel地址
port: 8719
启动类:
@EnableDiscoveryClient
@SpringBootApplication
@EnableFeignClients
public class OrderNacosMain84
{
public static void main(String[] args) {
SpringApplication.run(OrderNacosMain84.class, args);
}
}
配置类:开启ribbon负载均衡
@Configuration
public class ApplicationContextConfig
{
@Bean
@LoadBalanced
public RestTemplate getRestTemplate()
{
return new RestTemplate();
}
}
业务类:
@RestController
@Slf4j
public class CircleBreakerController {
public static final String SERVICE_URL = "http://nacos-payment-provider";
@Resource
private RestTemplate restTemplate;
@RequestMapping("/consumer/fallback/{id}")
@SentinelResource(value = "fallback") //没有配置
//@SentinelResource(value = "fallback",fallback = "handlerFallback") //fallback只负责业务异常
//@SentinelResource(value = "fallback",blockHandler = "blockHandler") //blockHandler只负责sentinel控制台配置违规
// @SentinelResource(value = "fallback",fallback = "handlerFallback",blockHandler = "blockHandler",
// exceptionsToIgnore = {IllegalArgumentException.class})
public CommonResult<Payment> fallback(@PathVariable Long id) {
CommonResult<Payment> result = restTemplate.getForObject(SERVICE_URL + "/paymentSQL/"+id, CommonResult.class,id);
if (id == 4) {
throw new IllegalArgumentException ("IllegalArgumentException,非法参数异常....");
}else if (result.getData() == null) {
throw new NullPointerException ("NullPointerException,该ID没有对应记录,空指针异常");
}
return result;
}
//fallback
public CommonResult handlerFallback(@PathVariable Long id,Throwable e) {
Payment payment = new Payment(id,"null");
return new CommonResult<>(444,"兜底异常handlerFallback,exception内容 "+e.getMessage(),payment);
}
//blockHandler
public CommonResult blockHandler(@PathVariable Long id, BlockException blockException) {
Payment payment = new Payment(id,"null");
return new CommonResult<>(445,"blockHandler-sentinel限流,无此流水: blockException "+blockException.getMessage(),payment);
}
}
启动测试:
http://localhost:84/consumer/fallback/1 多次访问
{"code":200,"message":"from mysql,serverPort: 9004","data":{"id":1,"serial":"28a8c1e3bc2742d8848569891fb42181"}}
{"code":200,"message":"from mysql,serverPort: 9003","data":{"id":1,"serial":"28a8c1e3bc2742d8848569891fb42181"}}
出现负载均衡,环境准备完毕!
演示fallback
fallback管运行时异常;
blockHandler只负责sentinel控制台配置违规,限流时用到;
@SentinelResource没有任何配置
@RequestMapping("/consumer/fallback/{id}")
@SentinelResource(value = "fallback") //没有配置
public CommonResult<Payment> fallback(@PathVariable Long id) {
CommonResult<Payment> result = restTemplate.getForObject(SERVICE_URL + "/paymentSQL/"+id, CommonResult.class,id);
if (id == 4) {
throw new IllegalArgumentException ("IllegalArgumentException,非法参数异常....");
}else if (result.getData() == null) {
throw new NullPointerException ("NullPointerException,该ID没有对应记录,空指针异常");
}
return result;
}
访问:http://localhost:84/consumer/fallback/5
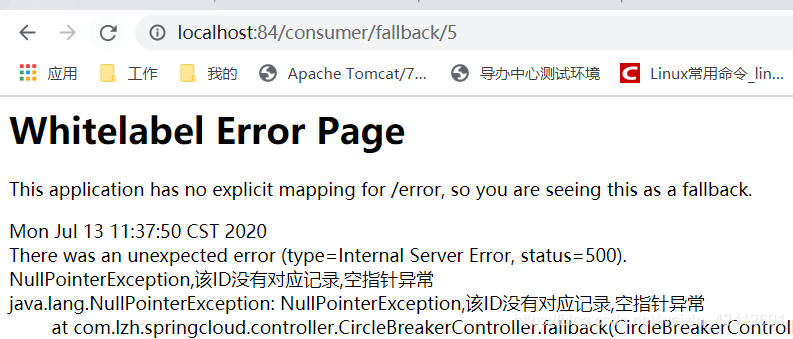
并没有限流,但是是接口自身出现的异常,给客户error页面,不友好。
只配置fallback
@RequestMapping("/consumer/fallback/{id}")
@SentinelResource(value = "fallback",fallback = "handlerFallback") //fallback只负责业务异常
public CommonResult<Payment> fallback(@PathVariable Long id) {
CommonResult<Payment> result = restTemplate.getForObject(SERVICE_URL + "/paymentSQL/"+id, CommonResult.class,id);
if (id == 4) {
throw new IllegalArgumentException ("IllegalArgumentException,非法参数异常....");
}else if (result.getData() == null) {
throw new NullPointerException ("NullPointerException,该ID没有对应记录,空指针异常");
}
return result;
}
//fallback
public CommonResult handlerFallback(@PathVariable Long id,Throwable e) {
Payment payment = new Payment(id,"null");
return new CommonResult<>(444,"兜底异常handlerFallback,exception内容 "+e.getMessage(),payment);
}
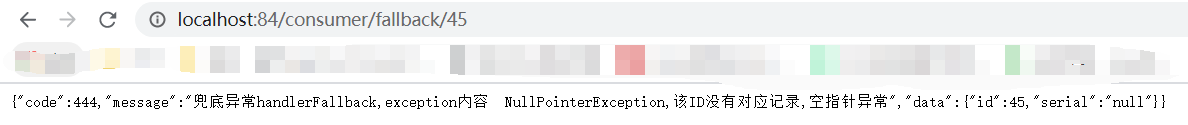
当接口自身再次出现异常时,就可以使用fallback自定义的兜底异常处理方法了。会比较友好。
只配置blockHandler
不说了,之前一直都用这个。就是如果触发了限流的规则,就限流,并且返回blockHandler指定的兜底方法
fallback和blockHandler都配置
@RequestMapping("/consumer/fallback/{id}")
@SentinelResource(value = "fallback",fallback = "handlerFallback",blockHandler = "blockHandler",
exceptionsToIgnore = {IllegalArgumentException.class})
public CommonResult<Payment> fallback(@PathVariable Long id) {
CommonResult<Payment> result = restTemplate.getForObject(SERVICE_URL + "/paymentSQL/"+id, CommonResult.class,id);
if (id == 4) {
throw new IllegalArgumentException ("IllegalArgumentException,非法参数异常....");
}else if (result.getData() == null) {
throw new NullPointerException ("NullPointerException,该ID没有对应记录,空指针异常");
}
return result;
}
//fallback
public CommonResult handlerFallback(@PathVariable Long id,Throwable e) {
Payment payment = new Payment(id,"null");
return new CommonResult<>(444,"兜底异常handlerFallback,exception内容 "+e.getMessage(),payment);
}
//blockHandler
public CommonResult blockHandler(@PathVariable Long id, BlockException blockException) {
Payment payment = new Payment(id,"null");
return new CommonResult<>(445,"blockHandler-sentinel限流,无此流水: blockException "+blockException.getMessage(),payment);
}
如果没有被限流,是接口自身的异常,兜底方法调的是blockHandler的;
如果被限流了,兜底方法调的是fallback 的;
如果既被限流了,又接口同时也出现异常,调哪个兜底方法?
调blockHandler的,因为blockHandler包在外头,限流了,都进不去接口里头,当然是调blockHandler的兜底方法啦。
忽略属性…
@SentinelResource(value = "fallback",fallback = "handlerFallback",blockHandler = "blockHandler",
exceptionsToIgnore = {IllegalArgumentException.class})
意思就是如果接口发生IllegalArgumentException类型的异常,就不调用fallback 指定的兜底方法。
依旧使用系统的错误页面,给用户返回一个不太友好的界面。
Feign系列
A调用B,B容易炸,给A配,即调用方的熔断保护
之前豪猪哥,服务降级那学过,一样的
修改84模块
POM:
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-openfeign</artifactId>
</dependency>
配置文件:
#对Feign的支持
feign:
sentinel:
enabled: true
业务类:
带@FeignClient注解的业务接口
@FeignClient(value = "nacos-payment-provider",fallback = PaymentFallbackService.class)
public interface PaymentService
{
@GetMapping(value = "/paymentSQL/{id}")
CommonResult<Payment> paymentSQL(@PathVariable("id") Long id);
}
PaymentFallbackService实现类:
@Component
public class PaymentFallbackService implements PaymentService
{
@Override
public CommonResult<Payment> paymentSQL(Long id)
{
return new CommonResult<>(44444,"服务降级返回,---PaymentFallbackService",new Payment(id,"errorSerial"));
}
}
Controller:
@Resource
private PaymentService paymentService;
@GetMapping(value = "/consumer/paymentSQL/{id}")
public CommonResult<Payment> paymentSQL(@PathVariable("id") Long id) {
return paymentService.paymentSQL(id);
}
主启动:
@EnableFeignClients
测试:启动9003提供者和当前84消费者
访问:http://localhost:84/consumer/paymentSQL/2
{"code":200,"message":"from mysql,serverPort: 9003","data":null}
此时故意关闭9003微服务提供者,看84消费者自动降级,不会被耗死:
再次访问接口:
{"code":44444,"message":"服务降级返回,---PaymentFallbackService","data":{"id":4,"serial":"errorSerial"}}
自定义流控响应
https://github.com/alibaba/Sentinel/tree/master/sentinel-adapter/sentinel-spring-webmvc-adapter
https://developer.aliyun.com/article/740637
除了使用,上面的fallback、blockHandler 之外,还有一种方式
@Configuration
public class SeckillWebConfig implements WebMvcConfigurer {
@Autowired
private SentinelWebInterceptor sentinelWebInterceptor;
/**
* 添加拦截器
* @param registry
*/
@Override
public void addInterceptors(InterceptorRegistry registry) {
registry.addInterceptor(sentinelWebInterceptor).addPathPatterns("/**");
}
/**
* 自定义流控响应
* @return
*/
@Bean
public SentinelWebInterceptor sentinelWebInterceptor(){
SentinelWebMvcConfig sentinelWebMvcConfig = new SentinelWebMvcConfig();
sentinelWebMvcConfig.setBlockExceptionHandler((request, response, e) -> {
R error = R.error(BizCodeEnum.TOO_MANY_REQUEST.getCode(), BizCodeEnum.TOO_MANY_REQUEST.getMessage());
response.setCharacterEncoding("utf-8");
response.setContentType("application/json");
response.getWriter().write(JSON.toJSONString(error));
});
return new SentinelWebInterceptor(sentinelWebMvcConfig);
}
}
配置文件:
spring.cloud.sentinel.filter.enabled=false
结果:限流时返回的流控响应,就是自己定义的了

注意:这个方式是在sentinel1.7.1才有的,之前的版本不是这样使用的
这样:配置文件不需要配置
@Configuration
public class GulimallSeckillSentinelConfig {
public GulimallSeckillSentinelConfig() {
WebCallbackManager.setUrlBlockHandler(new UrlBlockHandler() {
@Override
public void blocked(HttpServletRequest request, HttpServletResponse response, BlockException ex) throws IOException {
R error = R.error(BizCodeEnum.TO_MANY_REQUEST.getCode(), BizCodeEnum.TO_MANY_REQUEST.getMessage());
response.setCharacterEncoding("UTF-8");
response.setContentType("application/json");
response.getWriter().write(JSON.toJSONString(error));
}
});
}
}
规则持久化
是什么?
一旦我们重启应用,Sentinel规则将消失,生产环境需要将配置规则进行持久化。
怎么玩?
将限流配置规则持久化进Nacos保存,只要刷新8401某个rest地址,sentinel控制台的流控规则就能看到,只要Nacos里面的配置不删除,针对8401上Sentinel上的流控规则持续有效
演示:修改cloudalibaba-sentinel-service8401
pom:
<dependency>
<groupId>com.alibaba.csp</groupId>
<artifactId>sentinel-datasource-nacos</artifactId>
</dependency>
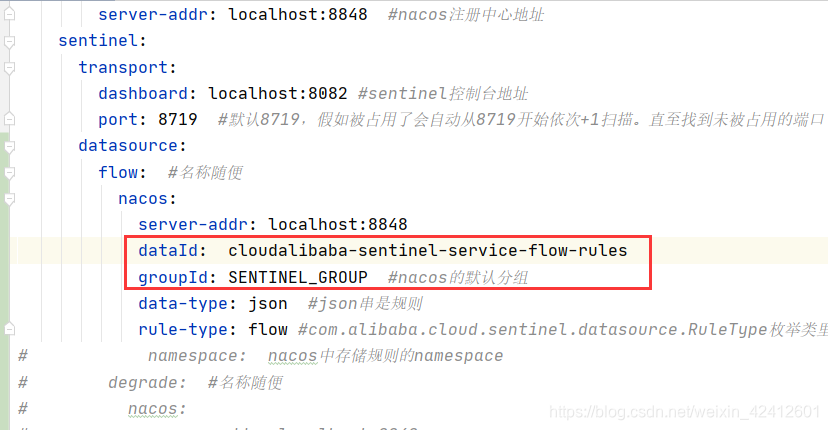
配置文件:
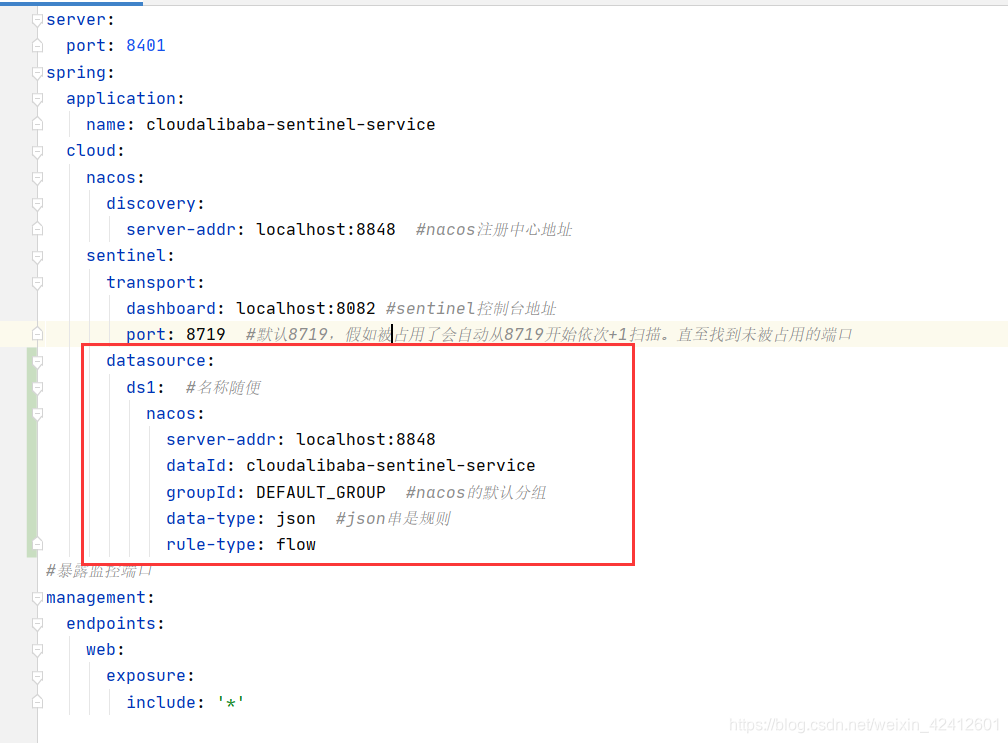
flow: #名称随便
nacos:
server-addr: localhost:8848
dataId: cloudalibaba-sentinel-service
groupId: DEFAULT_GROUP #nacos的默认分组
data-type: json #json串是规则
rule-type: flow #com.alibaba.cloud.sentinel.datasource.RuleType枚举类里有更多的规则类型
# namespace: nacos中存储规则的namespace
# degrade: #名称随便
# nacos:
# server-addr: localhost:8848
# dataId: ${spring.application.name}-degrade-rules
# groupId: DEFAULT_GROUP #nacos的默认分组
# data-type: json #json串是规则
# rule-type: degrade #com.alibaba.cloud.sentinel.datasource.RuleType枚举类里有更多的规则类型
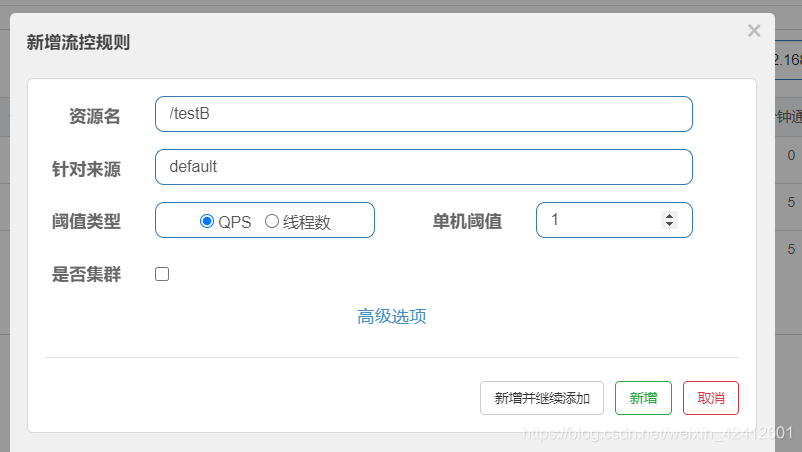
添加Nacos业务规则配置:添加一个配置,DataID,就是上面配置文件配的那个
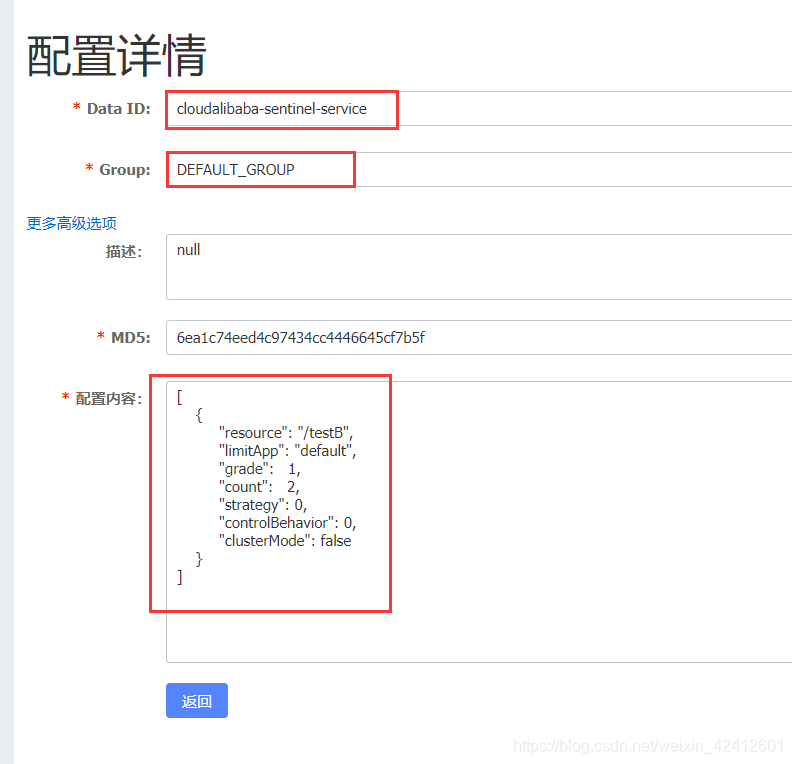
给接口/testB添加一个规则
[
{
"resource": "/testB",
"limitApp": "default",
"grade": 1,
"count": 2,
"strategy": 0,
"controlBehavior": 0,
"clusterMode": false
}
]
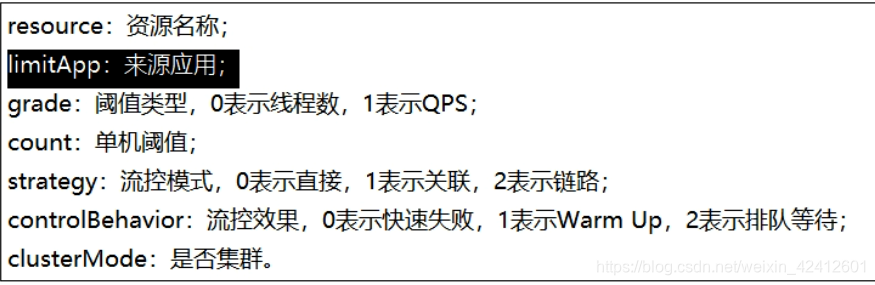
启动8401。
访问接口:http://localhost:8401/testB
多次访问会发现,能够触发限流,然后到sentinel控制台看看:规则也已经同步上去了
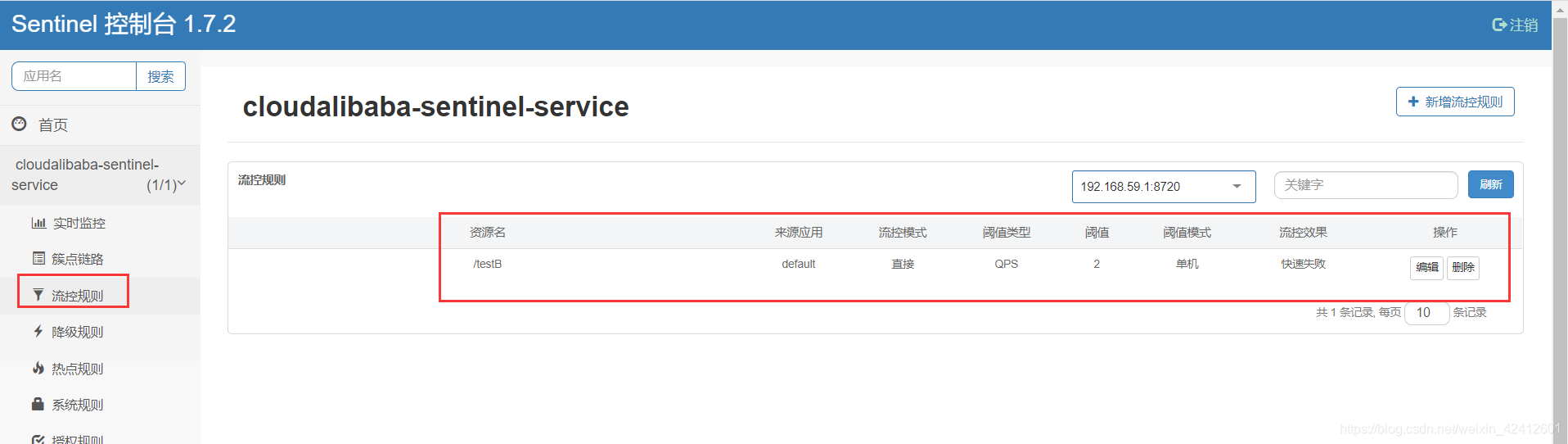
问题1:修改nacos里的sentinel规则,能同步到sentinel里吗?
nacos里把QPS改为5
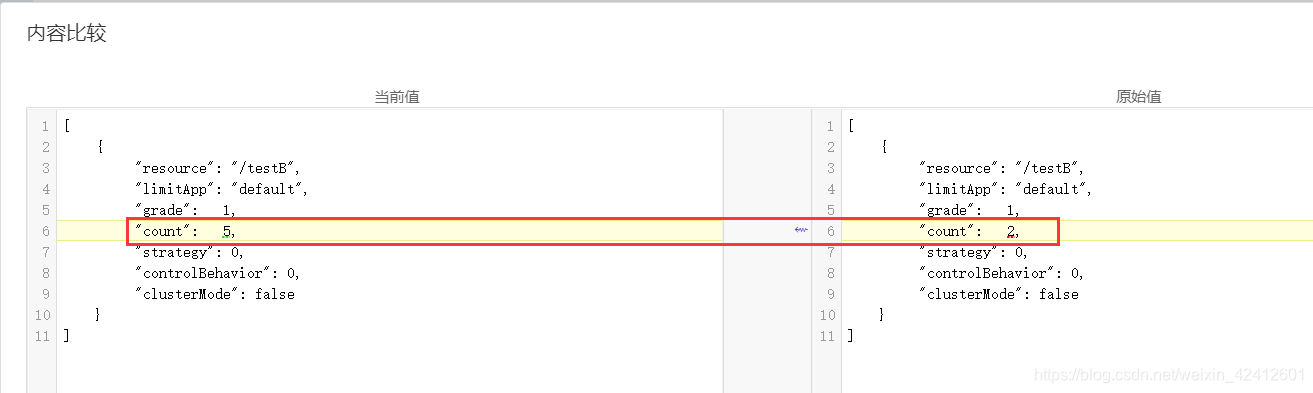
sentinel页面刷新,阈值为5了。
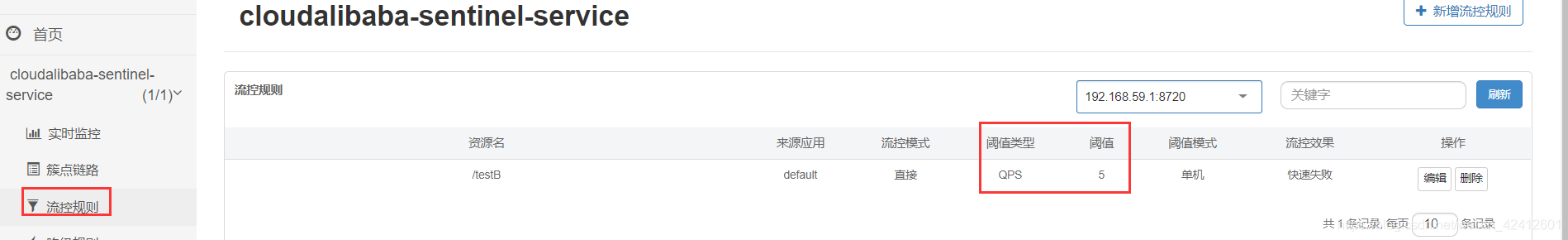
结论:在nacos上修改sentinel规则能实时推送到sentinel上。
问题2:修改sentinel里的规则,能同步到nacos里吗?
这里就不测了。不能
Sentinel控制台改造:规则同步到Nacos
1.下载源码:https://github.com/alibaba/Sentinel/releases/tag/1.7.2
2.导入源码
3.修改sentinel-dashboard模块
4.修改POM
把sentinel-datasource-nacos的<scope>注释了
<!-- for Nacos rule publisher sample -->
<dependency>
<groupId>com.alibaba.csp</groupId>
<artifactId>sentinel-datasource-nacos</artifactId>
<!-- <scope>test</scope>-->
</dependency>
5.修改sidebar.html
找到sentinel-dashboard\src\main\webapp\resources\app\scripts\directives\sidebar中的sidebar.html
把
<li ui-sref-active="active">
<a ui-sref="dashboard.flowV1({app: entry.app})">
<i class="glyphicon glyphicon-filter"></i> 流控规则
</a>
</li>
修改为:其实就是把flowV1的V1去掉
<li ui-sref-active="active">
<a ui-sref="dashboard.flow({app: entry.app})">
<i class="glyphicon glyphicon-filter"></i> 流控规则
</a>
</li>
6.在com.alibaba.csp.sentinel.dashboard.rule包下把nacos包复制到,com.alibaba.csp.sentinel.dashboard.rule目录下
7.只修改NacosConfig,其他不修改。
@Bean
public ConfigService nacosConfigService() throws Exception {
Properties properties = new Properties();
//nacos地址
properties.put(PropertyKeyConst.SERVER_ADDR, "localhost:8848");
// properties.put(PropertyKeyConst.NAMESPACE, "xxx");
return ConfigFactory.createConfigService(properties);
}
8.NacosConfigUtil说明:
GROUP_ID 配置的规则在nacos中的分组
FLOW_DATA_ID_POSTFIX DataId的后缀
public static final String GROUP_ID = "SENTINEL_GROUP";
public static final String FLOW_DATA_ID_POSTFIX = "-flow-rules";
9.FlowRuleNacosProvider说明:拉取Nacos配置
其中有一段代码,意思是从nacos上获取配置,获取的方式:
DataId:appName + NacosConfigUtil.FLOW_DATA_ID_POSTFIX
组: NacosConfigUtil.GROUP_ID
String rules = configService.getConfig(appName + NacosConfigUtil.FLOW_DATA_ID_POSTFIX,
NacosConfigUtil.GROUP_ID, 3000);
10.FlowRuleNacosPublisher 说明:推送配置给Nacos
推送时,DataId还是应用名拼接NacosConfigUtil.FLOW_DATA_ID_POSTFIX
组 NacosConfigUtil.GROUP_ID
configService.publishConfig(app + NacosConfigUtil.FLOW_DATA_ID_POSTFIX,
NacosConfigUtil.GROUP_ID, converter.convert(rules));
9.FlowControllerV2修改
将之前的ruleProvider,rulePublisher替换成下面的
@Autowired
@Qualifier("flowRuleNacosProvider")
private DynamicRuleProvider<List<FlowRuleEntity>> ruleProvider;
@Autowired
@Qualifier("flowRuleNacosPublisher")
private DynamicRulePublisher<List<FlowRuleEntity>> rulePublisher;
10.FlowControllerV1修改:
把方法publishRules注释了,替换成下面的
@Autowired
@Qualifier("flowRuleNacosPublisher")
private DynamicRulePublisher<List<FlowRuleEntity>> rulePublisher;
private CompletableFuture<Void> publishRules(String app, String ip, Integer port) {
List<FlowRuleEntity> rules = repository.findAllByMachine(MachineInfo.of(app, ip, port));
try {
rulePublisher.publish(app, rules);
logger.info("添加限流规则成功{}", JSON.toJSONString(rules.stream().map(FlowRuleEntity::toRule).collect(Collectors.toList())));
return sentinelApiClient.setFlowRuleOfMachineAsync(app, ip, port, rules);
} catch (Exception e) {
logger.info("添加限流规则失败{}",JSON.toJSONString(rules.stream().map(FlowRuleEntity::toRule).collect(Collectors.toList())));
e.printStackTrace();
}
return null;
}
11.打包编译,启动sentinel-dashboard
12.修改客户端8041
这里的DataId要和上面FlowRuleNacosProvider,FlowRuleNacosPublisher设置的一样,都是应用名拼接上-flow-rules
组也要一致。data-type: flow 表示流控规则
13.启动客户端
14.测试
添加一个流控规则。
nacos查看:配置同步过去了
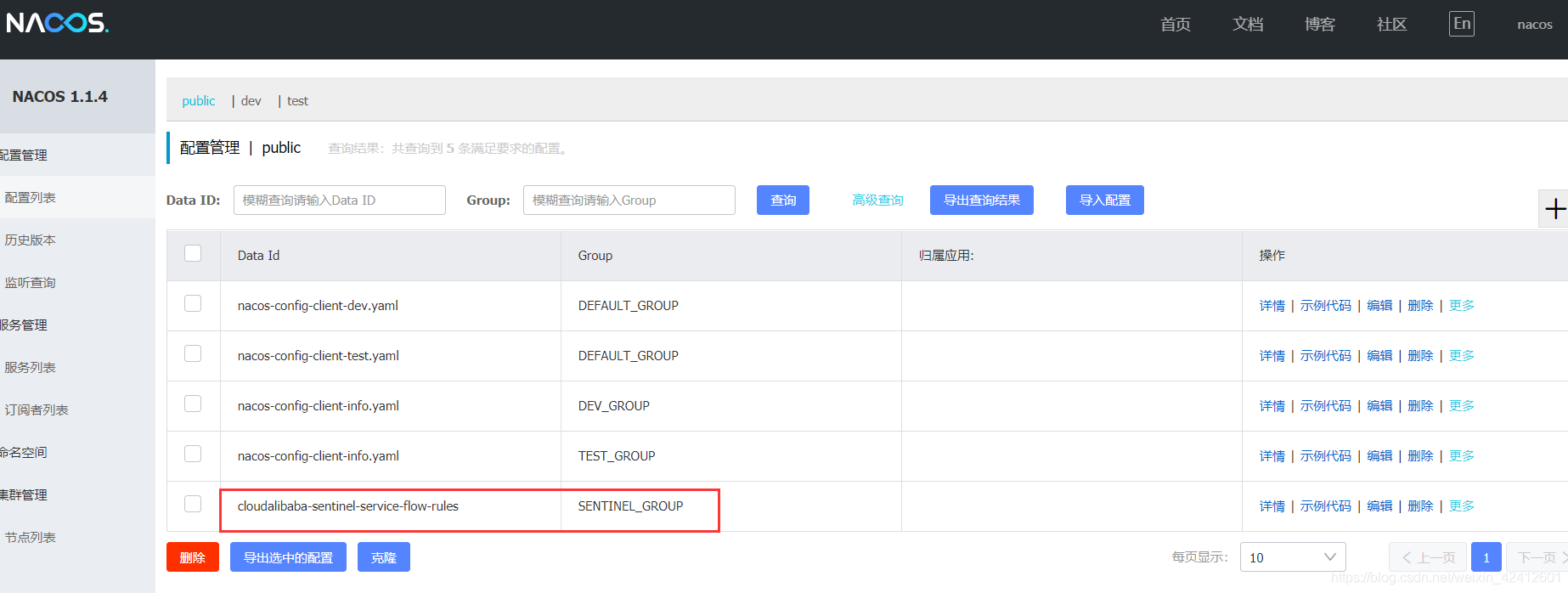
访问接口试试:http://localhost:8401/testB
会出现限流。
sentinel里修改配置能实时同步到nacos, 同时nacos里改也能实时同步到sentinel。
再加一个限流规则:
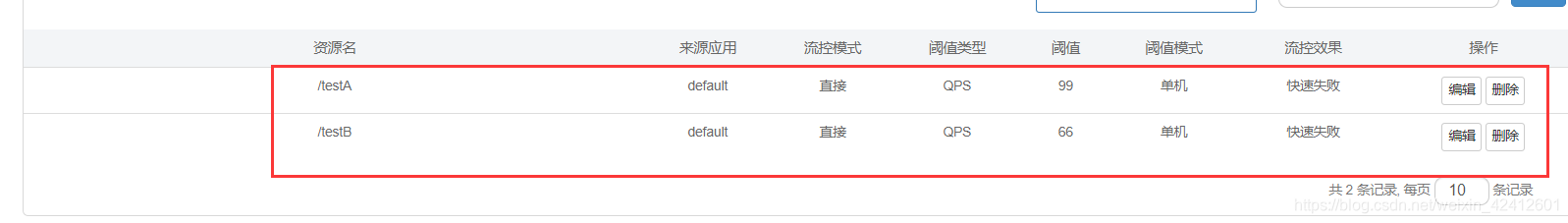
nacos查看两条都在
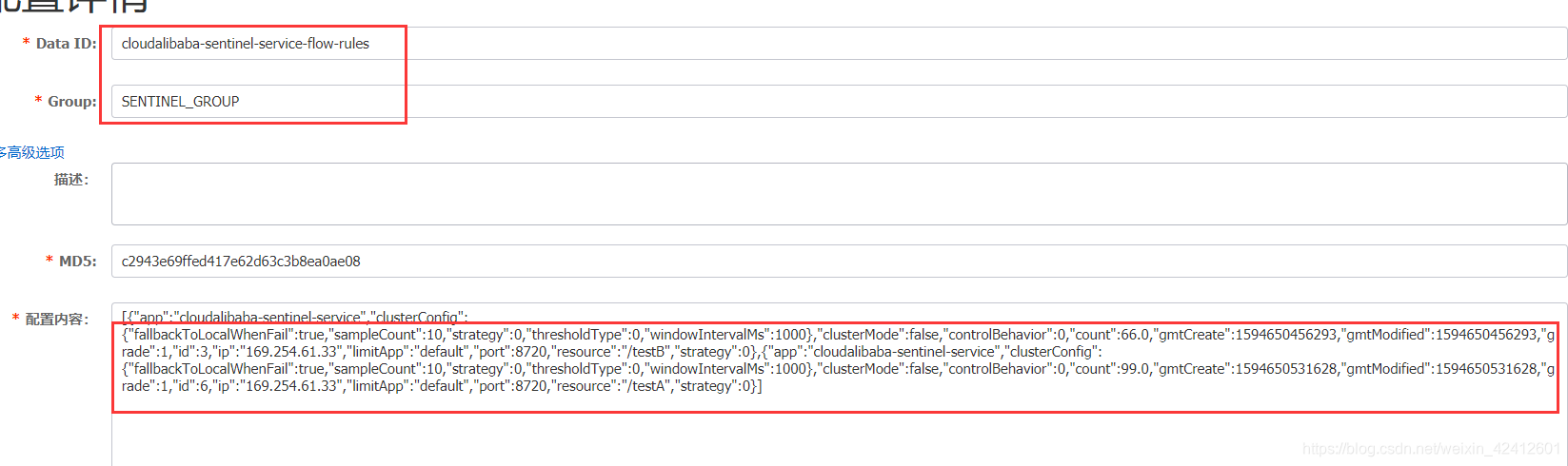
这里只配置了流控规则同步到Nacos,其他规则也得配。
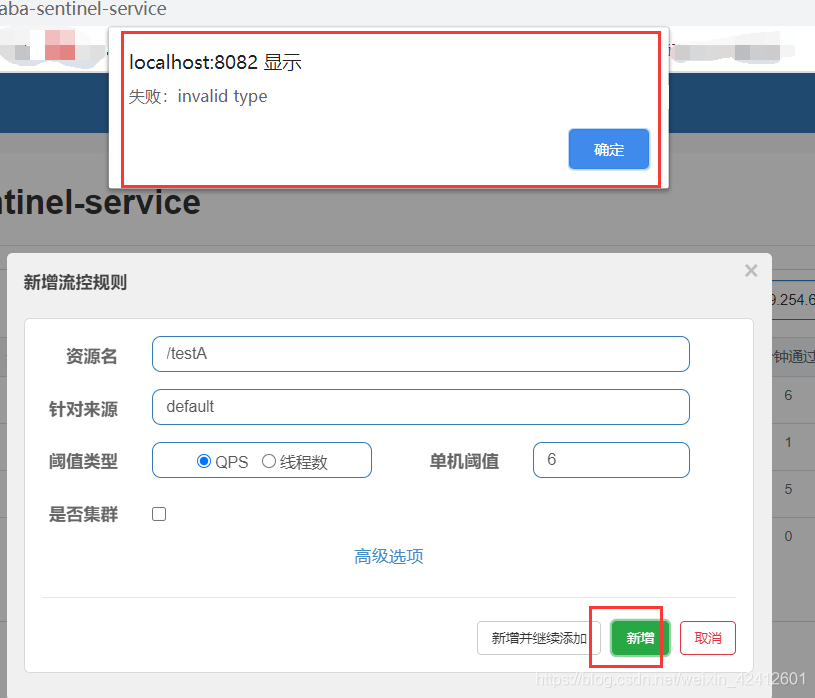
注意:我测试的时候,使用1.7.1的版本在新曾流控规则的时候,会出现非法类型的错误。
没解决这个问题,但是这一套配下来,在1.7.2版本下好使的。
排查了好久,还没找着什么原因。。。